FIDO2(WebAuthn) Server officially certified by FIDO Alliance

FIDO (Fast IDentity Online) is an open standard for online authentication, aiming to eliminate the vulnerabilities of passwords. FIDO uses public-key cryptography instead of symmetric credentials like passwords or PINs.
In essence, the user's device generates a key pair, storing the private key securely and sharing the public key with the server. During both registration and authentication, the server challenges the device, and the device responds with a digital signature using the private key. The server then verifies this signature with the stored public key. This challenge-response protocol helps prevent replay attacks.
FIDO2 is an enhancement of the FIDO standard for web and other platforms, supported by major web browsers and operating systems. It encompasses two primary operations: Registration and Authentication.
Both the registration and authentication processes utilize a challenge-response protocol to prevent replay attacks. During registration, a challenge is sent from the server to the device and the device responds using its private key. Similarly, during authentication, another challenge is sent to verify the user's identity. This ensures that each attempt is unique and secure.
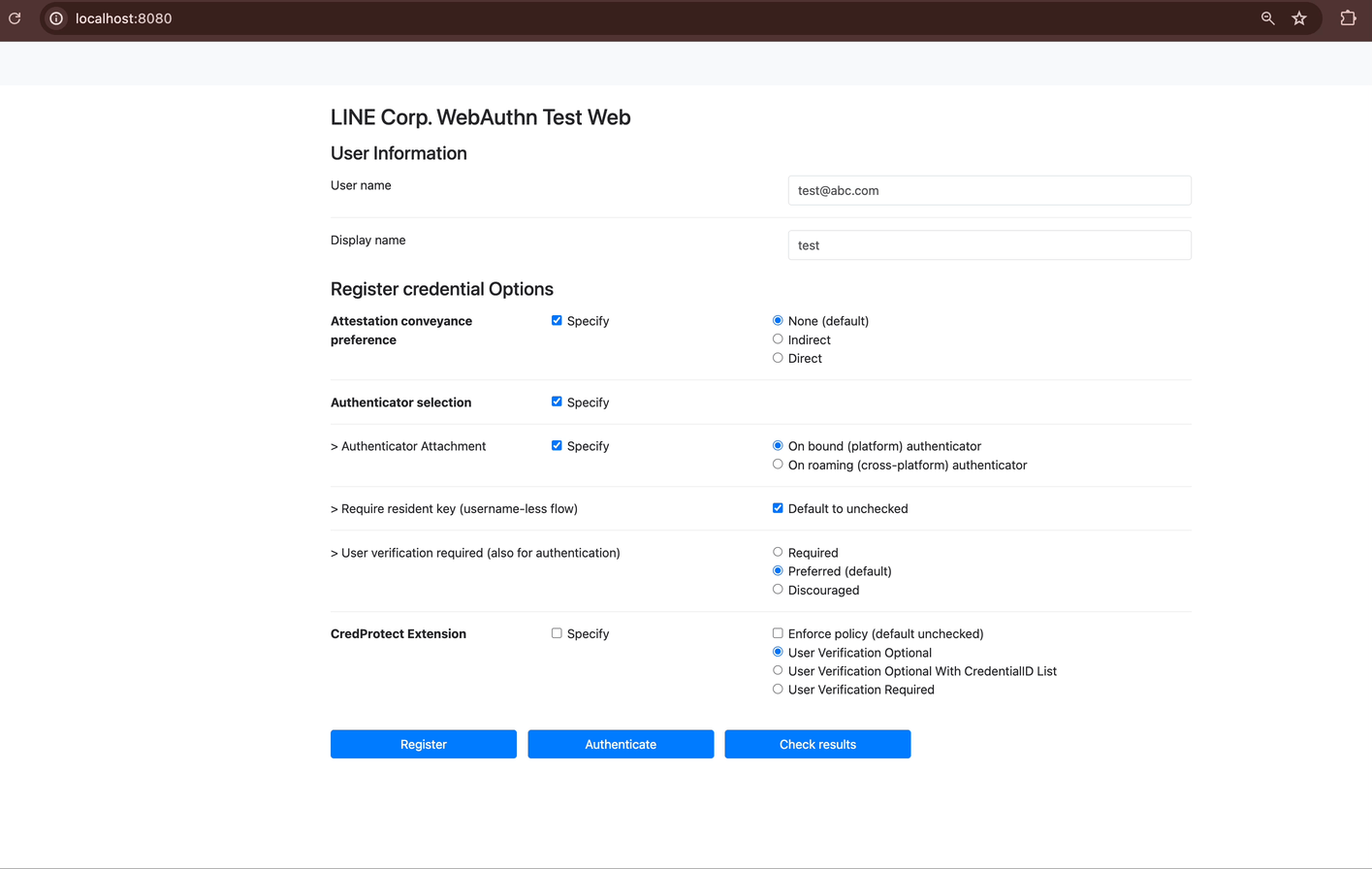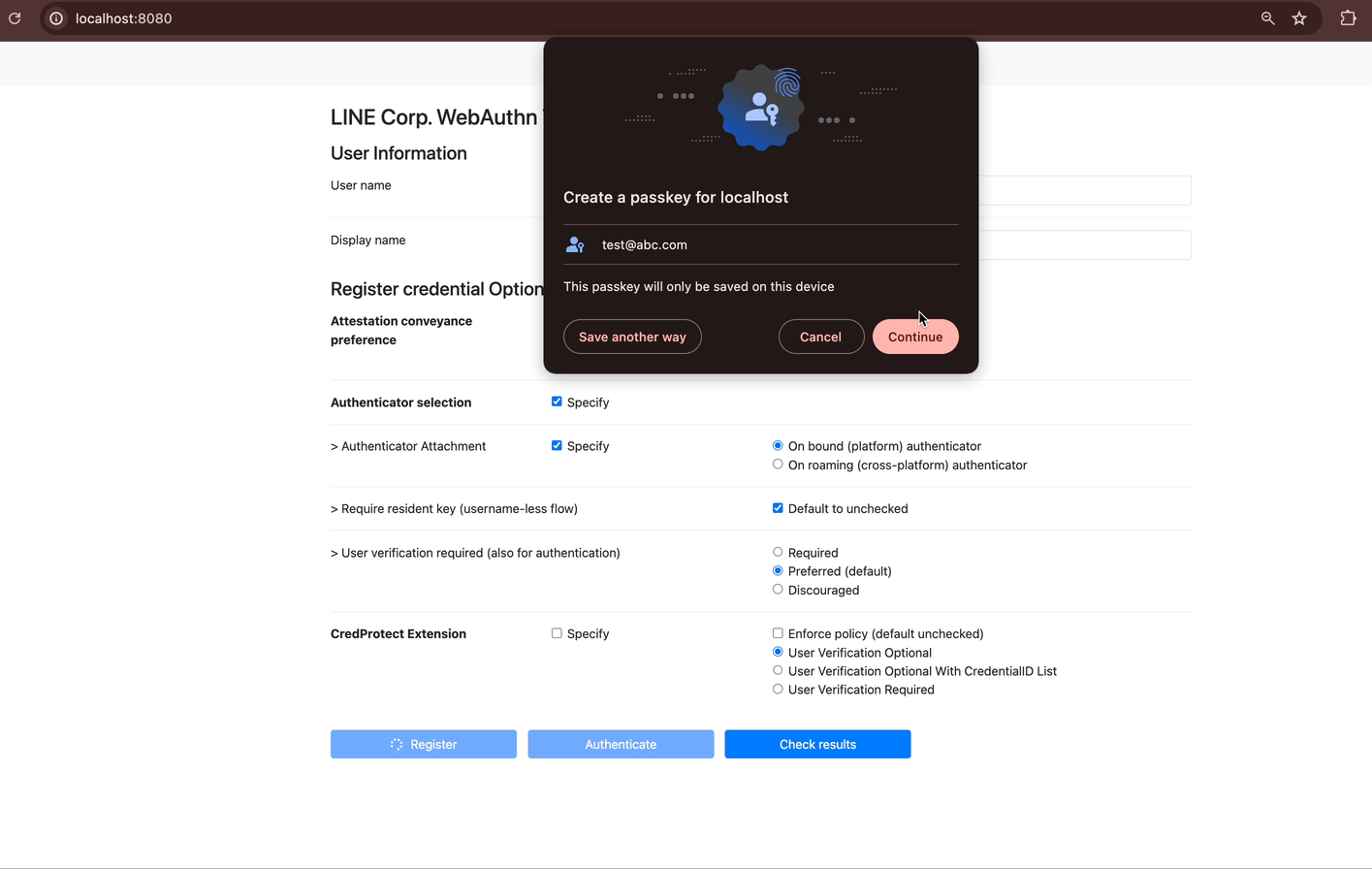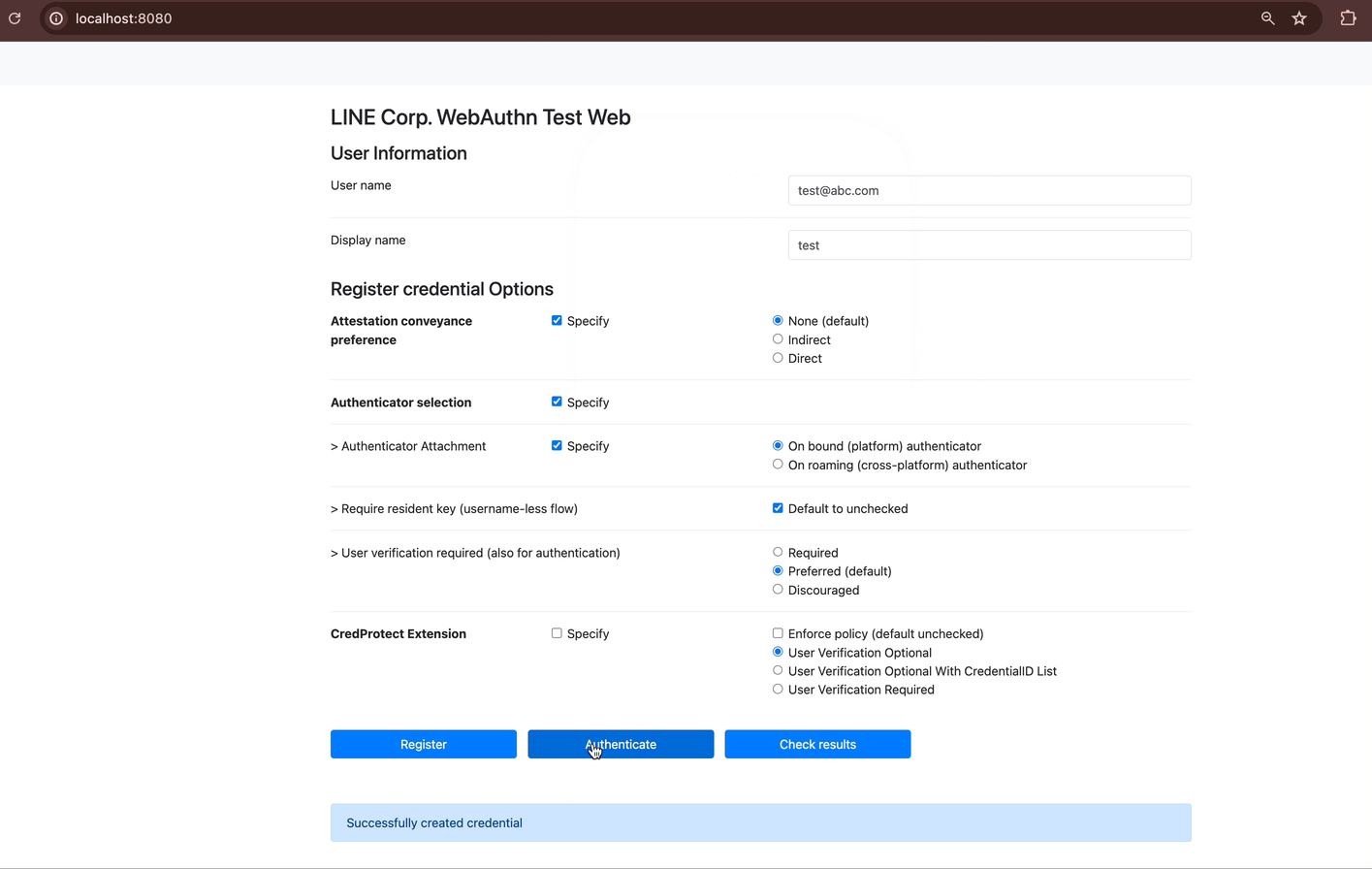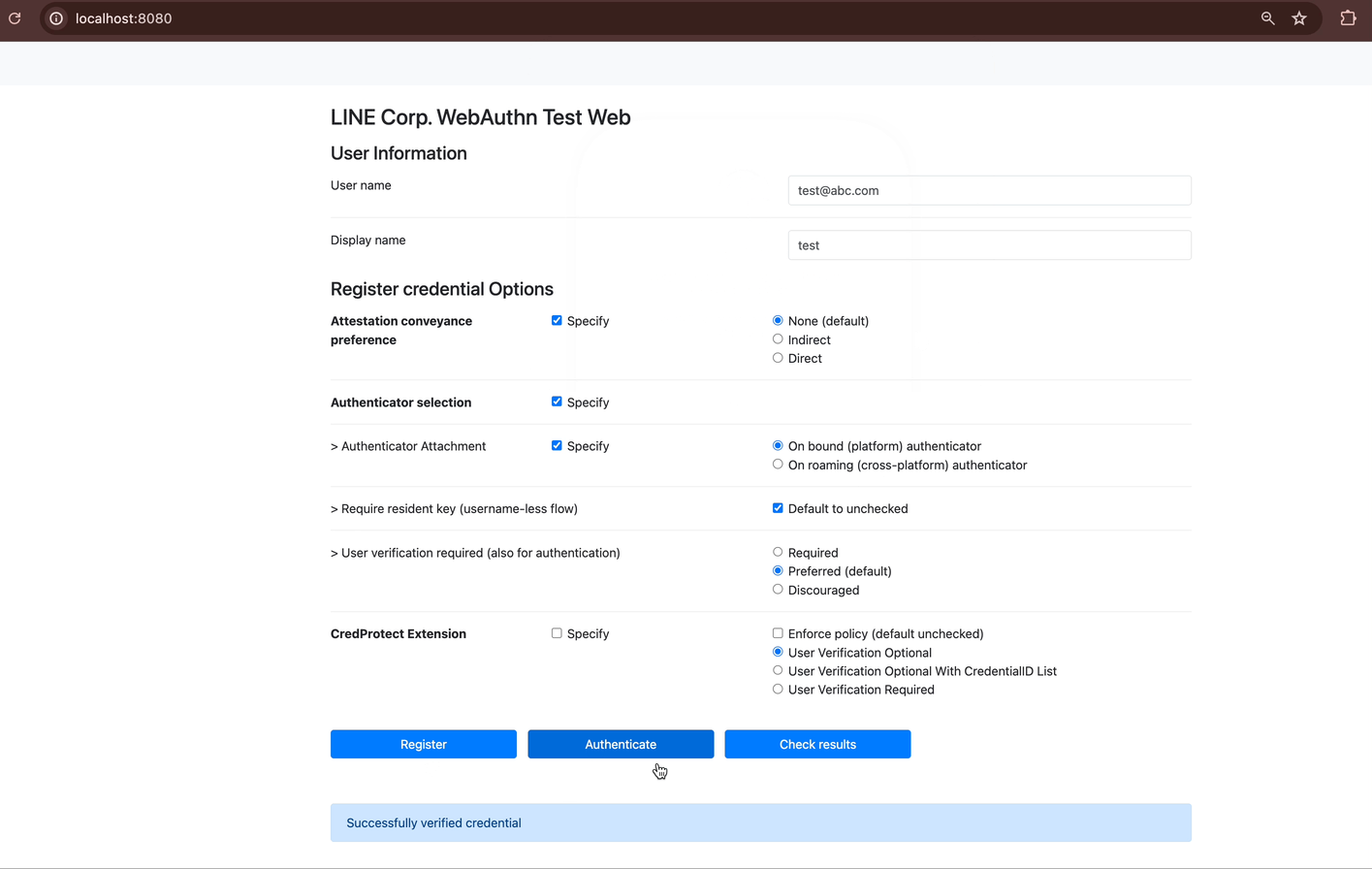
Start the RP Server and FIDO2 Server:
# Start RP Server
cd rpserver
./gradlew bootRun
# Start FIDO2 Server
cd fido2-demo/demo
./gradlew bootRunIf you have Docker configured, you can use docker-compose.
# Start both RP Server and FIDO2 Server
docker-compose upOnce the applications are running, access the test page at:
The FIDO2 Server uses H2 as an embedded DB in a local environment, which should be replaced with a standalone DB (like MySQL) for staging, beta, or production environments. Access the H2 web console at:
jar {
processResources {
exclude("**/*.sql")
}
}To view the API documentation, follow these steps:
cd fido2-demo/demo
./gradlew makeRestDocs
./gradlew bootRunAfter running the applications, you can view API guide documents at the link below.
We are also providing Client SDK for Android/iOS applications. Please see below.
The checkOrigin method validates the origin of requests from LINE's Android and iOS applications. It ensures security
by checking that the request's origin matches a pre-configured list of allowed origins.
How to Configure
To use the checkOrigin method, set up the allowed origins in the application.yml file. Here is an example
configuration:
app:
origins:
- android:aaa-bbb
- ios:aaa-bbbNote: Replace aaa-bbb with the appropriate values for your application.
Important: This configuration is optional and only necessary when integrating with LINE WebAuthn for Android and iOS applications.
LY Engineering Blogs
LY Tech Videos
Internal