One-stop page debugging and packet capture tool. Remotely debug any mobile browser page and any mobile webview (such as WeChat, HybridApp, etc.). Supports HTTP/HTTPS, no USB connection device required.
Language: English
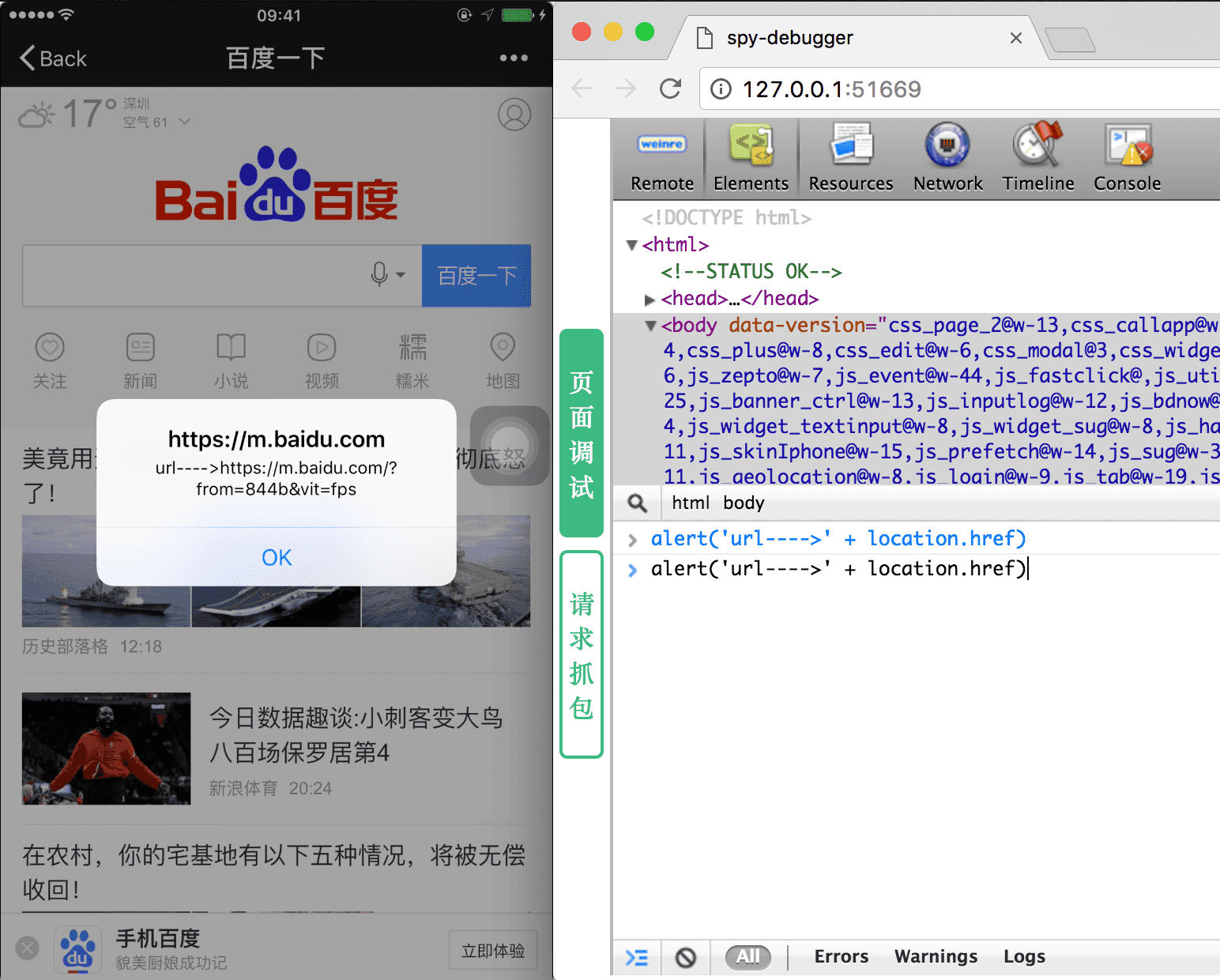
1. Page debugging + packet capture
2. Easy to operate, no USB connection device required
3. Support HTTPS .
4. spy-debugger integrates weinre , node-mitmproxy , and AnyProxy .
5. Automatically ignore https requests initiated by native App and only intercept https requests initiated by webview. It will not have any impact on native apps that use SSL pinning technology. [PS: Due to the adjustment of the proxy protocol iOS 15 , iOS 15 is no longer able to detect whether the request is initiated by the browser]
6. Can be used with other proxy tools (AnyProxy is used by default) (set external proxy)
Start command: spy-debugger -w true 
Under Windows
npm install spy-debugger -g
Under Mac
sudo npm install spy-debugger -g
Step 1: Keep the mobile phone and PC on the same network (for example, connected to a Wi-Fi at the same time)
Step 2: Enter spy-debugger on the command line, and follow the command line prompts to open the corresponding address with a browser.
Step 3: Set the HTTP proxy of the mobile phone. The proxy IP address is set to the IP address of the PC, and the port is the startup port of spy-debugger (default port: 9888).
设置- WLAN - 长按选中网络- 修改网络- 高级- 代理设置- 手动设置- 无线局域网- 选中网络- HTTP代理手动Step 4: Install the certificate on your phone. Note: The mobile phone must first set up the proxy and then access http://s.xxx (地址二维码) through a (non-WeChat) mobile browser to install the certificate (the first debugging of the mobile phone requires the installation of the certificate. Mobile phones that have already installed the certificate do not need to repeat it. Install). Newly installed certificates on iOS need to manually turn on certificate trust
Step 5: Use your mobile browser to access the page you want to debug.
(Default port: 9888)
spy-debugger -p 8888
spy-debugger -e http://127.0.0.1:8888
spy-debugger's built-in AnyProxy provides packet capture function, but it can also be used with other packet capture proxy tools by setting up an external proxy, such as Charles and Fiddler.
This function makes page content modification more intuitive and convenient. (Default: false)
spy-debugger -w true
Internal implementation principle: Inject code into the page that needs to be debugged: document.body.contentEditable=true . Pages using the iscroll frame are not supported yet.
(Default: false)
spy-debugger -i true
iOS 15 , it is no longer possible to detect whether the request is initiated by the browser](Default: false)
spy-debugger -b true
The connect request issued by some browsers does not carry the userAgent correctly, and this judgment sometimes goes wrong, such as UC Browser . This time it needs to be set to false. In most cases, it is recommended to enable the default configuration: true. Since a large number of requests issued by the App itself (non-WebView) currently use SSL pinning technology, the custom certificate will not pass the app's certificate verification.
(Default: false)
spy-debugger -c true
Fixed the bug where weinre would crash in node.js V7 version
Improved and repaired the problem that weinre cannot print the console.log log before the page document ready event.
Enhance weinre printing uncaught exceptions (Uncaught Exceptions) function.
The principle of spy-debugger is to integrate weinre , which simplifies the need for weinre to add js code to each debug page. The principle of spy-debugger is to intercept all html page requests and inject the js code required by weinre . Make page debugging more convenient.