Crack the WeChat database of a certain host environment to obtain its chat history
If you use a WeChat bot such as wechaty , you can only hook each real-time message and cannot obtain complete historical chat records.
However, if within the framework of wechaty , plus the API for obtaining chat records, it may be feasible.
Since WeChat chat records are stored in the database, they can be obtained from the database perspective.
Because WeChat chat records are stored in sqlcipher , which is a sqlite database that supports encryption and requires a secret key to open, so we must first obtain the secret key of the database.
Taking MacOS as an example, we can use some reverse methods ( dtrace ) to hook the database activity of the program. Since the program opening the database involves reading the key, we can parse this reading action to obtain the plaintext secret key.
In theory, it can be implemented on any platform, especially Android, Windows and other platforms. There are more reverse engineers and it may be less difficult to crack. However, my personal main computer is Mac/iOS, so I have not considered compatibility with the Windows/Android ecosystem for the time being.
Secondly, the engineering capabilities on the PC side are richer than those on the mobile side. Therefore, giving priority to breakthroughs on the PC side is a cost-effective choice.
At present, our dtrace script and the entire hook logic need to ensure that the version of the MacOS WeChat client is below 3.6 .
Download address of previous versions of WeChat: Older versions of WeChat (Mac) | Uptodown
On MacOS, an environment that can read and write sqlcipher must be configured.
# 1. check where is your `libcrypto.a`
brew list openssl | grep libcrypto.a
# 或者 find /usr/local/Cellar -name libcrypto.a
# 2. use the libcrypto.a with openssl version >= 3
LIBCRYPTO={YOUR-libcrypto.a}
# 3. install sqlcipher
git submodule add https://github.com/sqlcipher/sqlcipher
cd sqlcipher
./configure --enable-tempstore=yes CFLAGS= " -DSQLITE_HAS_CODEC "
LDFLAGS= $LIBCRYPTO --with-crypto-lib=none
make
# need password
sudo make installYou need to hold down cmd + shift + R to enter safe mode (just press and hold the power button on Mac Studio)
# check SIP
csrutil status
# disable SIP, need in recovery mode (hold on shift+R when rebooting)
csrutil disable
tip: You need to ensure that you are running the correct WeChat program with the corresponding version.
# comparing to `wechat-decipher-macos`, I make the script more robust.
# 由于key是固定的,也可以把输出内容持久化,只需要在命令后面加上 `> data/dbcracker.log`
pgrep -f /Applications/WeChat-3.6.0.app/Contents/MacOS/WeChat | xargs sudo core/dbcracker.d -p > .keystip: The key reading action will occur when logging in, so you need to run the program first and then log in.
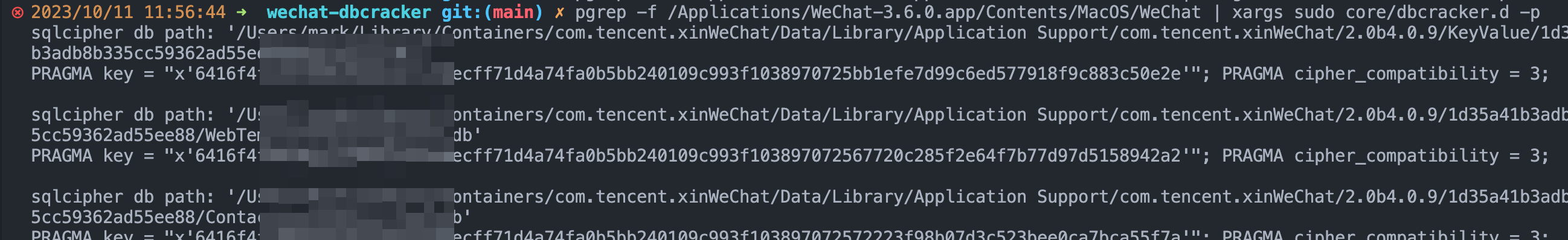
Since we have obtained the storage address, secret key, version, etc. of each database, we can programmatically read all data.
pysqlciphernode-sqlcipher