meth
1.0.0
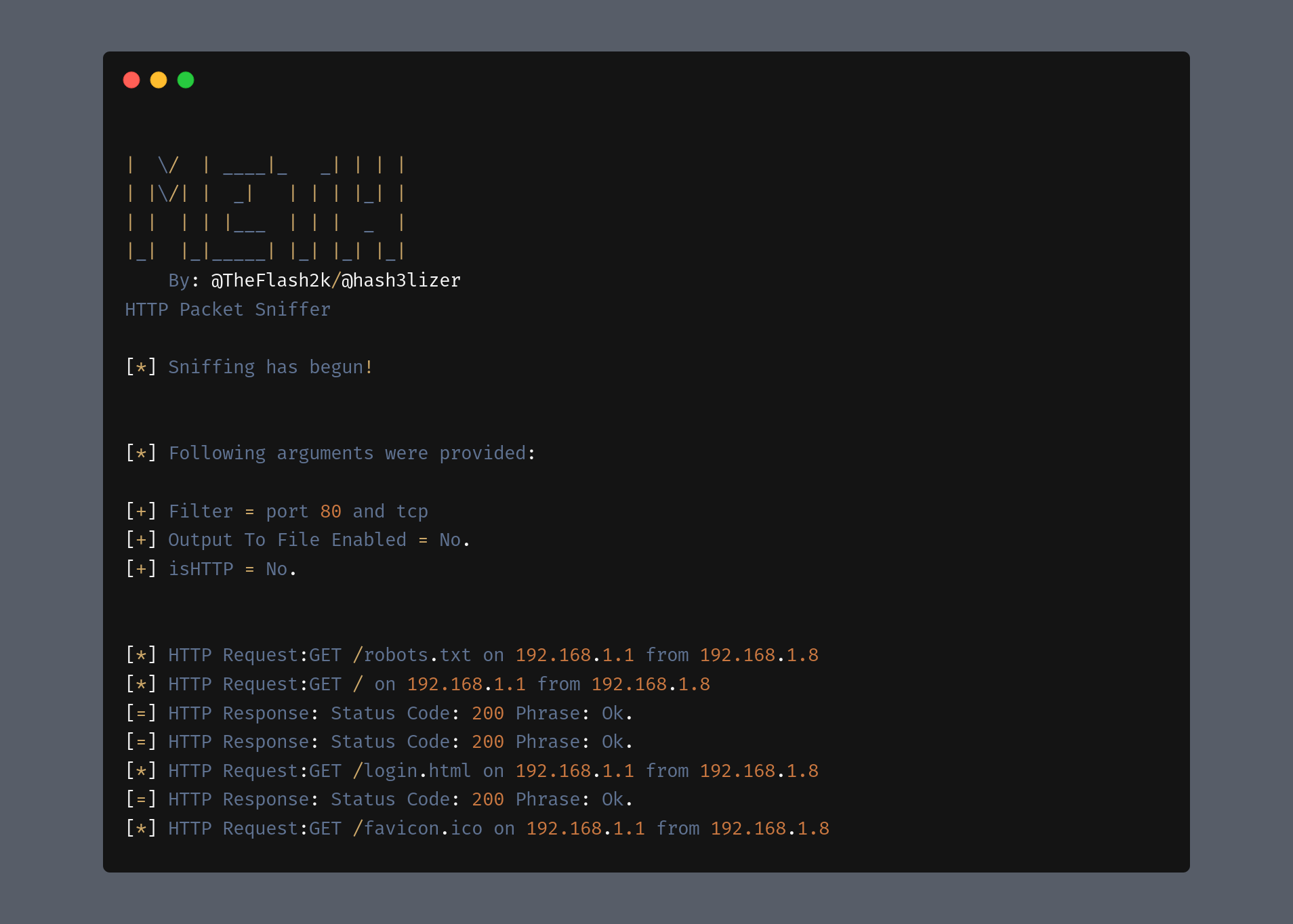
Um Packet Sniffer baseado em Python3 que tem a capacidade de detectar pacotes brutos HTTP, TCP, UDP, ICMP, ARP e gravar a saída em .pcap para inspeção em ferramentas como Wireshark.
Clonagem:
$ git clone https://github.com/TheFlash2k/meth.git
$ cd meth/
$ pip3 install -r requirements.txt
Primeira execução:
$ python3 meth.py
usage: meth.py [-h] [-c COUNT] [-f FILTER [FILTER ...]] [-H] [-o OUTFILE] [-i INTERFACE]
METH - HTTP Packet Sniffer.
optional arguments:
-h, --help show this help message and exit
-c COUNT, --count COUNT
Numbers of packets that you need to capture (0 = Infinity)
-f FILTER [FILTER ...], --filter FILTER [FILTER ...]
The Berkeley Packet Filter (BPF) that you need to set. (Default is: 'port 80 and tcp') NOTE: You need to Specify them as a string
-H, --http-only Limit the results to display only http/https packets
-o OUTFILE, --outfile OUTFILE
Store all the sniffed packet to a .pcap file (You don't need Specify the extension, just the file name.)
-i INTERFACE, --interface INTERFACE
Specify an interface to sniff traffic on