Microsoft Sentinel is a scalable, cloud-native security information and event management (SIEM) that delivers an intelligent and comprehensive solution for SIEM and security orchestration, automation, and response (SOAR). Microsoft Sentinel provides cyberthreat detection, investigation, response, and proactive hunting, with a bird's-eye view across your enterprise.
Microsoft Sentinel also natively incorporates proven Azure services, like Log Analytics and Logic Apps, and enriches your investigation and detection with AI. It uses both Microsoft's threat intelligence stream and also enables you to bring your own threat intelligence.
Use Microsoft Sentinel to alleviate the stress of increasingly sophisticated attacks, increasing volumes of alerts, and long resolution time frames. This article highlights the key capabilities in Microsoft Sentinel.
SIEM INTEGRATION WITH ARTIFICIAL INTELLIGENCE CHATGPT.
STEPS HOW I INTEGRATE CHATGPT:
STEP-1:
FIRSTLY WE NEED TO CREATE OUR WORKSPACE
STEP-2 : WE NEED TO CREATE LOGIC FOR PLAYBOOK.
WHAT ARE PLAYBOOK IN SENTINAL? In Microsoft Sentinel, a playbook is an automated workflow designed to respond to security incidents and alerts. Playbooks use Azure Logic Apps to define a sequence of actions that are triggered when certain conditions are met, such as the detection of a specific type of alert or incident.
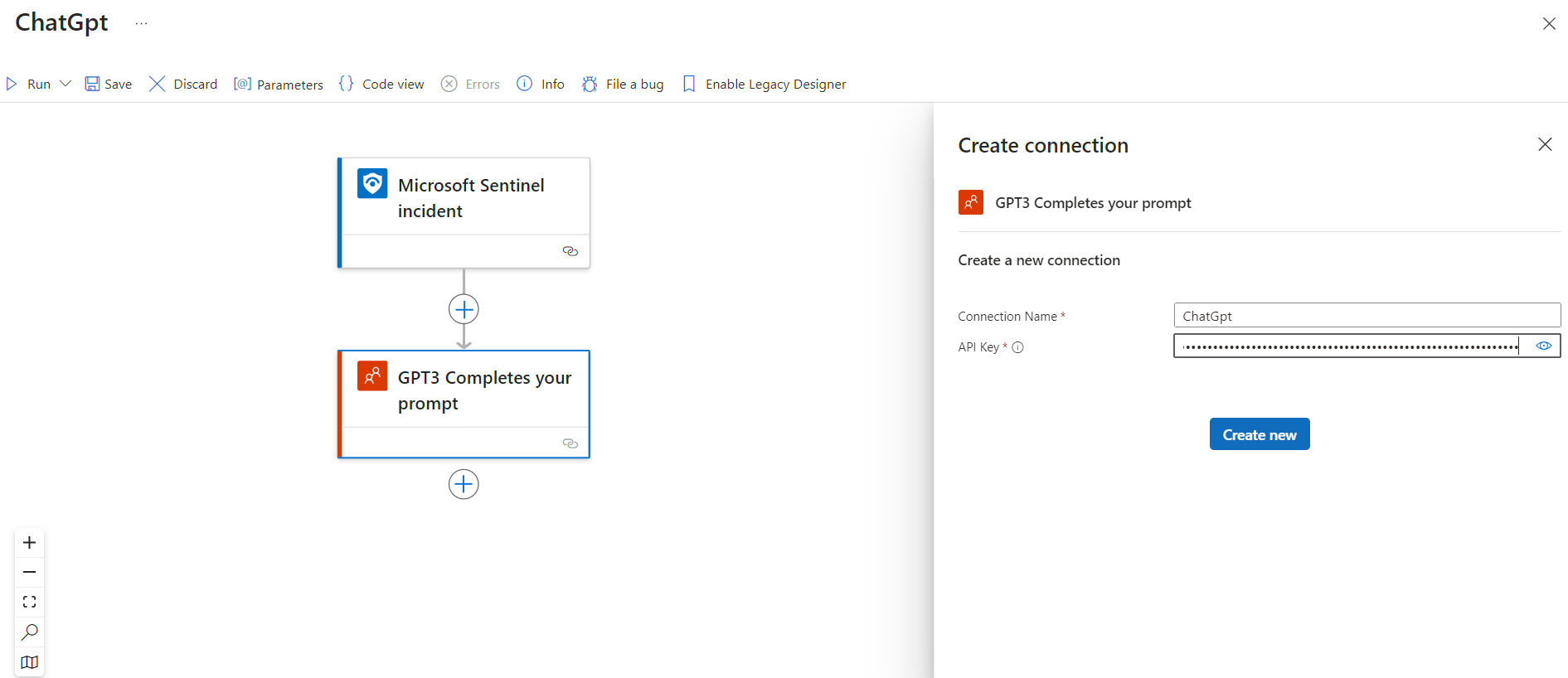
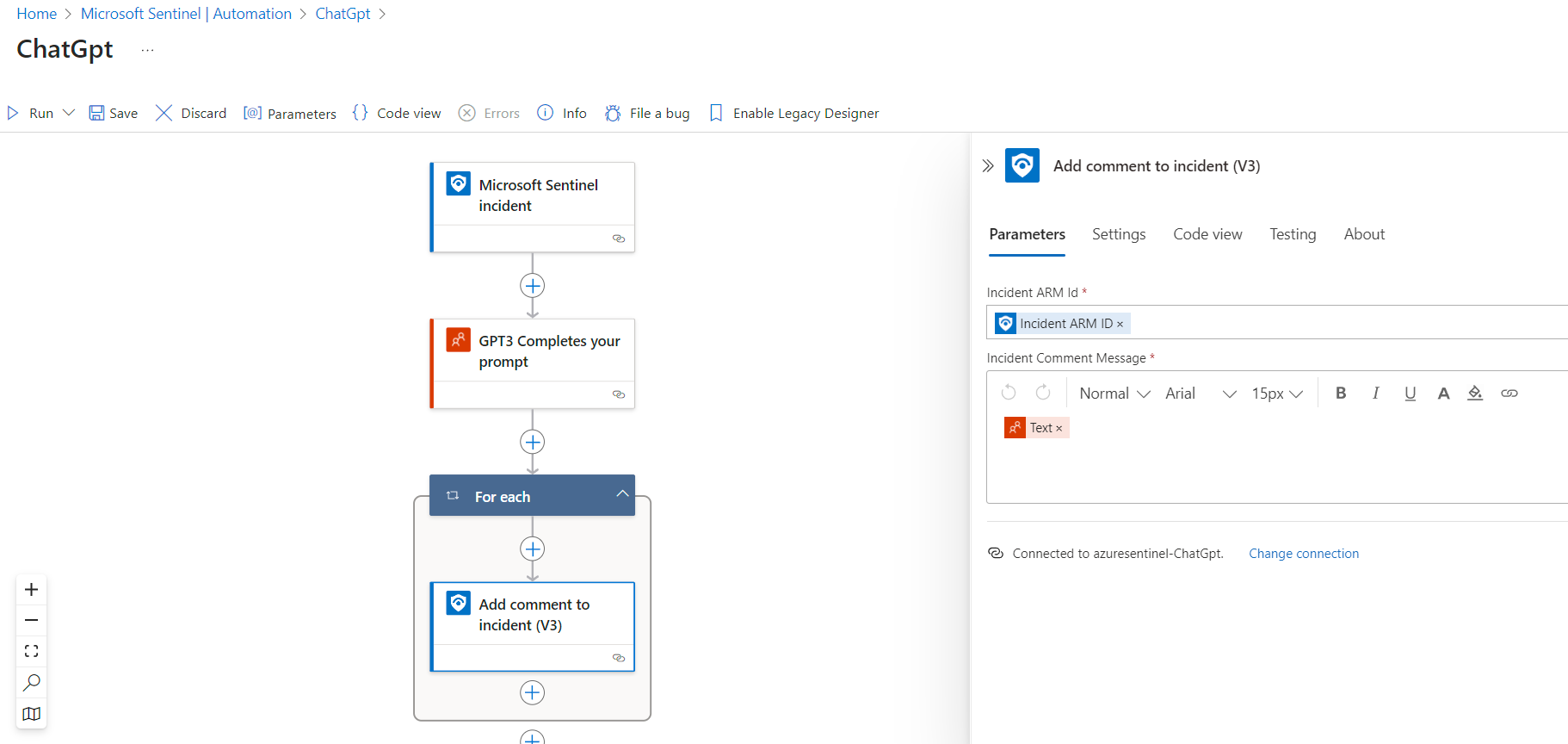
WHILE BUILDING THE LOGIC WE NEED TO INTEGRATE THE CHATGPT BY IMPORTING WITH OUR SECRET KEY PROVIDED BY OPENAI.
THEN WE NEED TO CREATE A AUTOMATION INCLUDES:
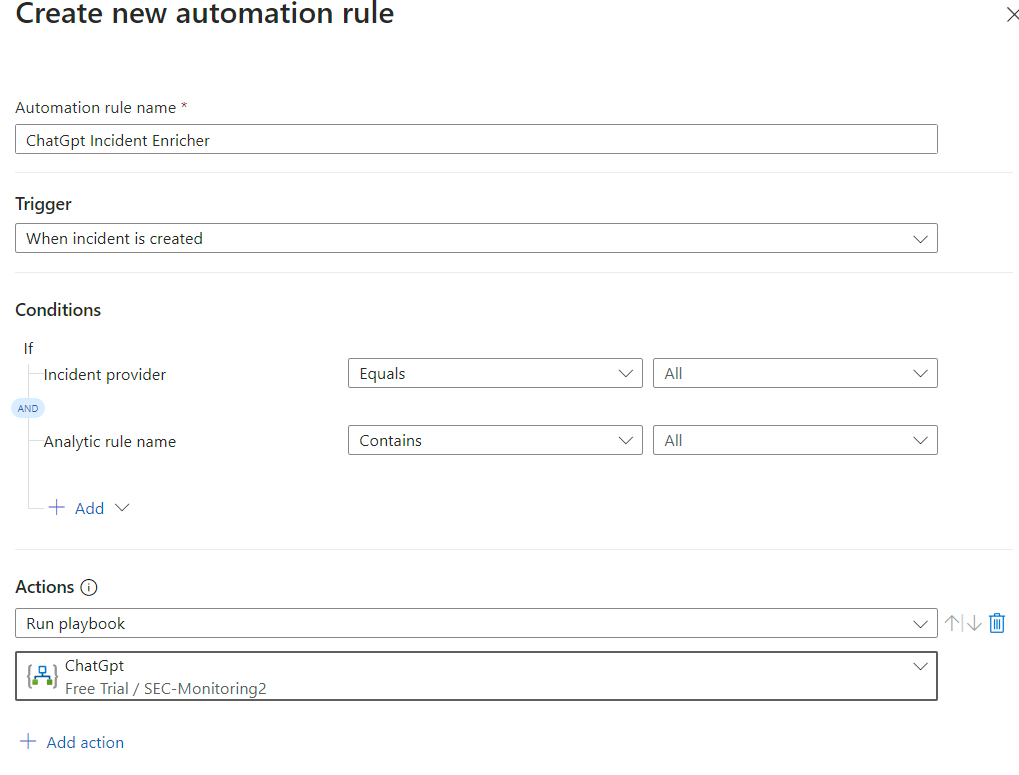
WHEN ANY INCIDENT CREATED THE AUTOMATION AUTOMATICALLY TRIGGERS AND ANALYZE THE INCIDENT BY CHATGPT AND PROVIDE A OVERVIEW OF INCIDENT AND MITIGATING PROCESS.