Full documentation
Win32 executables
It is a desktop application in Visual Basic 6 that allows you to describe the structure of a dangerous object in the form of a GERT network and calculate risk factor estimates for each node. The system is based on an engine based on COM objects implemented in Visual C++ / ATL, and there is a system of plugins for assessing hazards. Each plugin is a COM object. Also, there is a system facade in the form of a COM object for integration into Mathcad.
The hazard rating scale used is too large (11 points) for ratings to be easily made manually. Therefore, an essential part of the system is the automation component of their calculation (see Fig. 5.1). For this purpose, a special technique is proposed and implemented, outlined in the next paragraph. It turns out that many of the identified hazards overlap with those used by safety engineers. This implies a significant advantage of the developed model, which is expressed in the fact that methods for assessing conditions, occupational health and safety, can be relatively easily adapted for our many hazard factors. It is important that existing methods allow, on the basis of GOSTs, regulations and documentation for hazardous production facilities, to determine various quantitative characteristics of an object, converting them into universal scales (scoring). The very presence and testing of these methods is essential, simplifying the very labor-intensive process of developing a methodology for calculating estimates. The proposed methodology can be used in many cases, but not always, and not every expert will be satisfied with this approach. Therefore, greater flexibility is required. This is why an architecture was developed based on the implementation of the assessment module as an external component in relation to Hazard. To provide this flexibility, it is necessary to provide the user (usually an expert) with the ability to implement their own value estimation algorithms and use their own structures and databases. Since the type of connection between such a module and the Hazard system is simple, it is not advisable to burden the product with Visual Basic for Applications. The specifics of the development of such algorithms are determined by the need to work with complex data structures. Therefore, the Hosting script is also unsuitable and unjustifiably makes the product heavier, since it is designed to implement algorithms for managing objects, rather than processing structured data. The optimal concept here is the concept of expansion modules (plugins), which was implemented using COM technology. Such modules are usually very compact (small in size, have little dependence on various libraries and components, and consume little resources). They can be implemented in any language for which there is a tool that allows the development of components using COM technology. This provides greater implementation flexibility, but, in itself, does not introduce significant technological complexity to the task. Labor intensity and complexity increase significantly when implementing this component in low-level tools and languages, for example, using Visual C++. However, as a method accessible to unskilled programmers, the least labor-intensive and very effective, an implementation in Visual Basic is proposed. The type of communication with Hazard is very simple and the component is only required to be an in-process COM server that implements the IFactorAssign interface and can act as a COM client using the IDispatch interface and the MGertNet dual interface. Creating such COM objects, implemented by an in-process COM server, using Visual Basic 6 is trivial and can be easily performed by unskilled programmers, since it is essentially automated. The formulated essence of developing an extension determines the content of the specification for it. For the component to be recognized by Hazard, connected and able to interact with it, the following is required:
As an example, a universal extension was implemented (in Visual Basic 6), which is a very complex product and implements the weighted average technique. The implemented evaluation module using the weighted average method is universal, therefore it uses a sophisticated graphical interface, complex dynamic data structures and editors for them, which allows you to effectively describe a wide range of OPO. Therefore it is not a typical example. However, as already indicated, all these difficulties do not relate to the mechanism of interaction with Hazard, but are features of this implementation, certain requirements for it (as a universal commercial product). For special cases (official use), it is proposed to create simple modules with a static structure that can be effectively developed by unskilled programmers using Visual Basic.
Hazard is implemented as an out-of-process COM server (ActiveX EXE) using Visual Basic 6 and is represented by the COM class Hazard.HazardApp. The Hazard core, which contains codes for a model of the development of an incident at a hazardous production facility, codes for model running and optimization algorithms, is implemented as an in-process COM server (ActiveX DLL), using Visual C++ 6.0 (ATL) and is represented by the COM class GERTNETLib.MGertNet. Hazard can be used by OLE Automation clients, for which it provides the ability to create its own instances by creating Hazard.HazardApp. The HazardApp class has a number of public properties and methods that provide limited access to the capabilities of Hazard, for which a special layer has been implemented (albeit quite “crude”), taking into account the peculiarities of working in OLE automation server mode. The layer ensures not only the correct execution of functions, but also access to the Hazard core. The latter can also be used directly - by creating an instance of MGertNet without running Hazard. Most of the interfaces and classes of the GERTNETLib library are open and created (public, creatable), but their implementation largely imposes restrictions on the implementation of the interfaces described there, since an expanding conversion of pointers to interfaces to the types of implementing C++ objects is carried out. Therefore, direct use of the Hazard core must follow strict rules: Creating a Hazard instance:
Dim m_haApp As HazardApp
Set m_haApp = CreateObject( "Hazard.HazardApp" )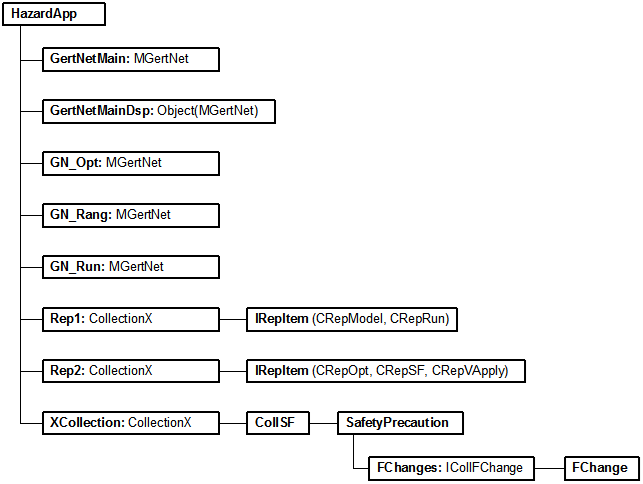 To notify clients about the progress of asynchronous operations, HazardApp and MGertNet provide a connection point for the sink with the ICallBack interface. Let's look at the objects included by a HazardApp instance. GertNetMain (read only) – incident development model. If there is no model (it was not loaded or a new one was created), then empty (Nothing). GertNetMainDsp (read only) – IDispatch interface of the incident development model. If there is no model (it was not loaded or a new one was created), then empty (Nothing).
To notify clients about the progress of asynchronous operations, HazardApp and MGertNet provide a connection point for the sink with the ICallBack interface. Let's look at the objects included by a HazardApp instance. GertNetMain (read only) – incident development model. If there is no model (it was not loaded or a new one was created), then empty (Nothing). GertNetMainDsp (read only) – IDispatch interface of the incident development model. If there is no model (it was not loaded or a new one was created), then empty (Nothing).
GN_Opt (read only) – a copy of the model used for optimization. Set only while optimization is running.
GN_Rang (read only) – a copy of the model used for ranking. Set only while ranking is in progress.
GN_Run (read only) – a copy of the model used during the run. Set only during run execution.
Rep1 (read only) – a collection of reports on the model (runs, model).
Rep2 (read only) – a collection of reports on sets of measures (optimization, complexes, trial application of sets of measures).
XCollection (read only) – a collection of security improvement measures. Each complex is described by a collection of activities (CollSF). Each event (SafetyPrecaution) contains a collection of impacts (FChange) on the model. To access complexes of measures, there is one more public property: SFnn(n). It is indexed and read-only.
Enumerators (read-only) – a collection of enumerators.
Factors (read only) – a collection of hazard factors. Each factor in this collection is assigned an enumerator from the Enumerators collection.
OptimizResultsGetAndClear (read only) – SAFEARRAY(IDispatch). Used after optimization has been performed. When this property is called, an array of pointers to the IDispatch interface of collections of security improvement measures is returned. In this case, the calling client becomes the owner of the collections, and the Hazard core releases references to them. Therefore, it can only be called once. Each collection contains a selection of activities - a possible solution to the optimization problem.
| Model editor | Score Table Editor |
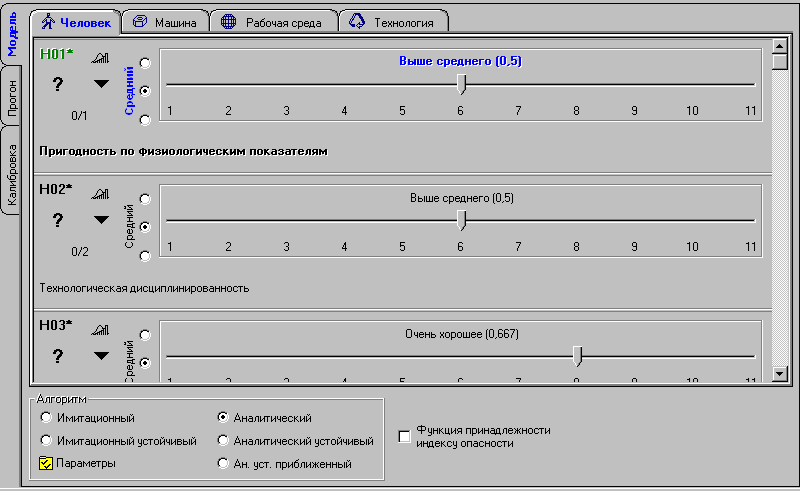 | 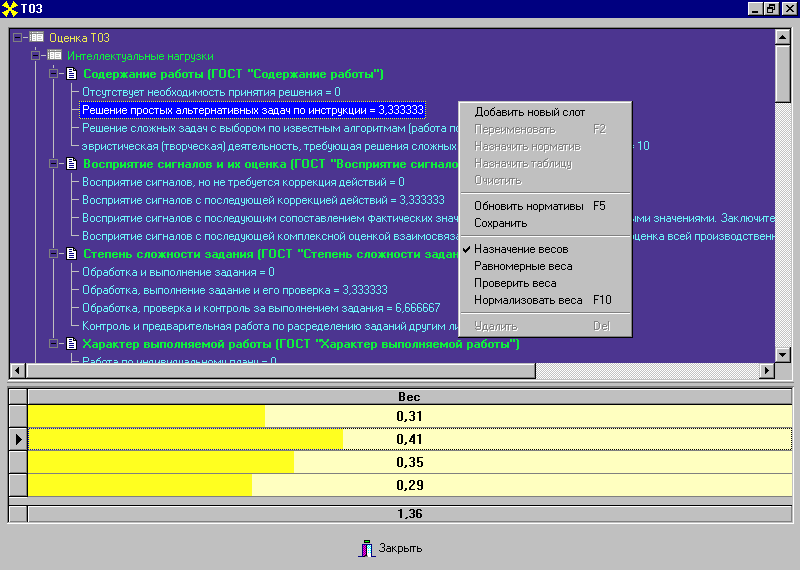 |
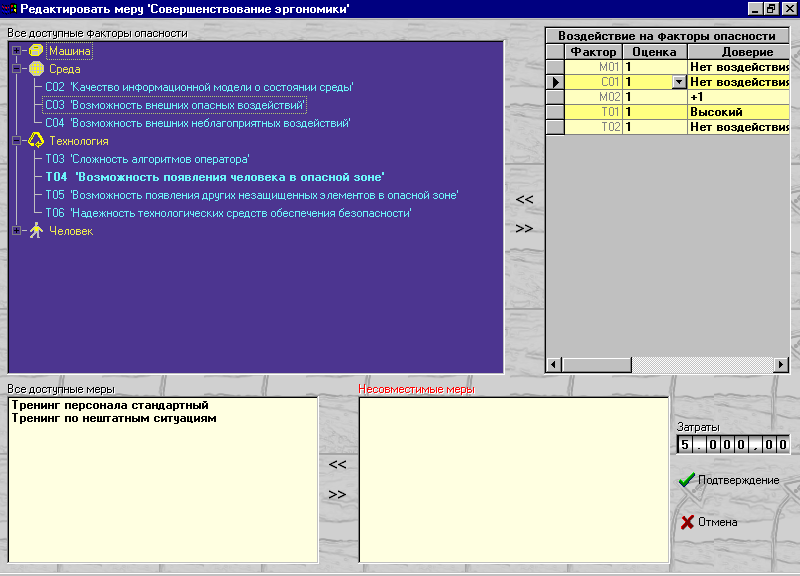
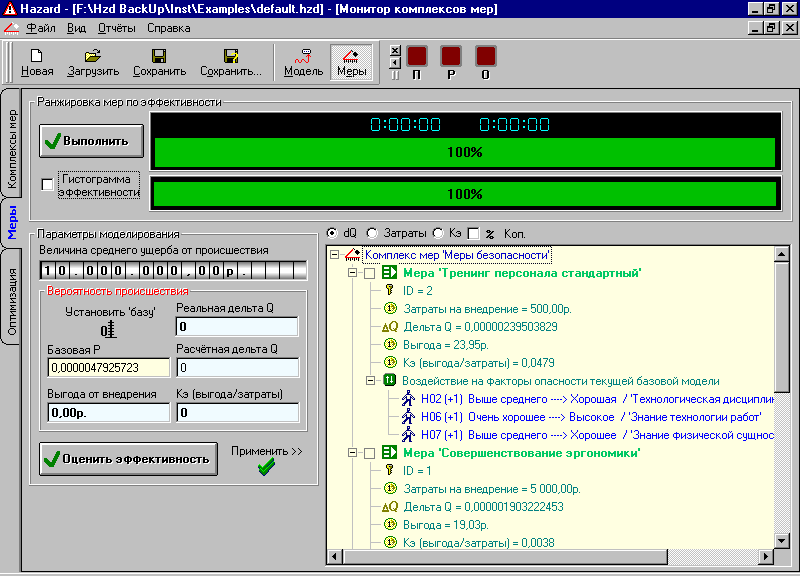
| Security Enhancement Editor | Measure package monitor |
 |  |