
In this repository we will find a step-by-step guide on how to Reverse Engineer an APK.
Reverse Engineering can help us in several aspects, such as identifying malicious software or code , discovering security flaws , finding features that were not expected /breaking business rules... That said, let's go deeper into the Android universe.
Starting with the basics, we can divide our Android Package (APK) into some parts:
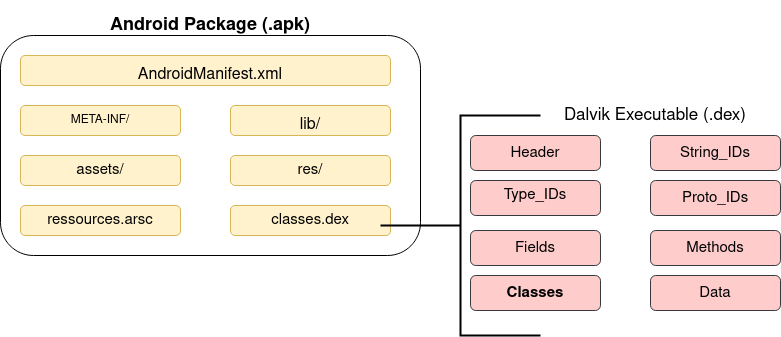
Smali is the human readable version of Dalvik bytecode, simply put, it works as an assemble/disassemble. Dalvik Executable Format (.dex)
In terms of code, let's take a look at the difference between Java and Smali:
public static void printHelloWorld() {
System.out.println("Hello World")
}
And our same code in Smali:
.method public static printHelloWorld()V
.registers 2
sget-object v0, Ljava/lang/System;->out:Ljava/io/PrintStream;
const-string v1, "Hello World"
invoke-virtual {v0,v1}, Ljava/io/PrintStream;->println(Ljava/lang/String;)V
return-void
.end method
We went through the necessary basic concepts and now get to work!
Step 1:
Choose the APK you want to Reverse.
If you can't find it easily through the app store itself, you can do so directly on sites like APKCombo or APKMonk.
Once here, pay attention to some things that may be interesting:
- Qual é o URL da API? (geralmente emos algo como api.domain.com)
- Qual é método de autenticação utilizado? Eu preciso criar um login para acessar?
- Quais são as chamadas que eu posso encontrar e quais são os parâmetros eles esperam?
Once we have the APK, it's time to decompile it, so that we can analyze the code.
(Dynamic Analysis Tools such as MOBSF allow you to download the code directly, whether in Java or SMALI).
Now we are going to use tools, the first of which is APKTOOL, you will see more details about it below, but in general it will be responsible for decompiling the files, creating a folder, in the same place, with all the decompiled files. From here, you will be able to analyze all the necessary codes.
The command used here will be the following:
- apktool d ~/Desktop/aplicativo_app.apk
Extracting the “classes.dex” file from the APK.
Use the dex2jar tool to convert to Java class files. Resulting in a jar file.
- sh d2j-dex2jar.sh classes.dex
Use JD-GUI to extract the source code from the jar file.
- Arraste o arquivo classes-dex2jar.jar pro JD-GUI
Mobile Security Framework is a tool that automates APK analysis. Inside it we get more details about the parts that make up APKs, which we saw previously.
dex2jar
dedexer
apktool
apktool is an opensource Java tool for reverse engineering Android applications. It can decode APK files to their original code in a human-readable XML. Also dividing all classes and methods contained in the file into Smali. This way, you are able to modify features or program executions. Using Smali code, you can add new functionality within that application or change the expected behavior.
Commonly used for SSL Pinning.
adb (Android Debug Bridge)
androguard
Xposed Framework
Commands: //soon
Bypass Android SSL
Frida
Now that we have a base of how this works, it's time to practice! Here is a list of some labs that you can use as an exercise:
Test the following attack types:
Thank you for getting here! Have a nice day.