At this stage, there are endless voting activities held in WeChat Moments. I believe many students are already annoyed by this, because people (relatives, friends, or whatever) will always pop up from time to time to ask you to vote for them.
This article does not intend to explore this issue from a moral or emotional level. What interests me is that most current voting activities actually have obvious loopholes, and "vote manipulation" can be achieved through simple technical means.
Here is an example.
An online hairdressing mall (hereinafter referred to as S Mall) held an online voting event on the WeChat platform. WeChat users can access the voting page through the event link and vote for their favorite hairstylists’ works; each WeChat account can only vote for Cast 1 vote for a single work.
The voting activity page is shown below:
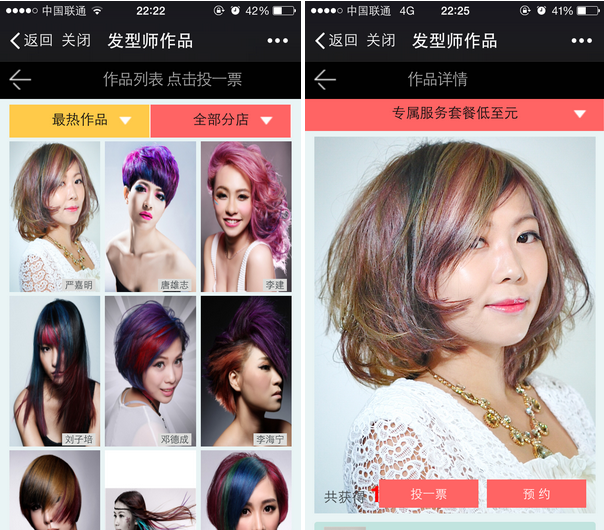
On the surface, S Mall has already implemented anti-cheating measures on voting activities because each WeChat user is restricted to only one vote per day. If users access this voting service normally through WeChat to vote, it will indeed have the desired effect.
However, if you view the original address of the voting page, that is, hold down the page and drag it down, you will find that "This webpage is provided by XXX" is displayed at the top of the screen. It should be noted that "XXX" here is not "mp.weixin. qq.com", but the domain name of S Mall. In other words, the program for this voting activity is running on the server of S Mall.
Based on the above analysis, it can be inferred that the network topology diagram of user voting operations should be as follows:
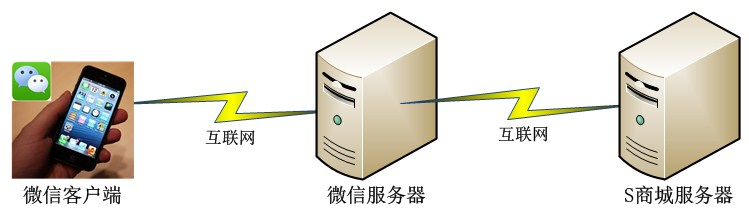
When a WeChat user accesses the voting page, the WeChat server only forwards the request, and the specific vote counting and verification are done on the S Mall server.
So, how does S Mall distinguish voting users?
This involves the concept of WeChat public platform OpenID . The official explanation of OpenID is: after encrypting WeChat ID, each user’s OpenID for each official account is unique.
It is easy to verify this. You only need to use multiple WeChat accounts to vote, capture network packets during the voting process, and check the parameters in the POST to confirm.
Based on this, the WeChat public platform will include the user's OpenID in the POST parameter when forwarding the voting request; after S Mall receives the voting POST request, it can prevent a single vote by querying whether the current OpenID has voted on that day. The user voted repeatedly.
However, there is a big loophole here!
S Mall can only determine whether OpenID is duplicated, but it cannot verify the validity of OpenID because it cannot call the WeChat server to verify the OpenID .
After clarifying this loophole, it is very simple to achieve ticket brushing.
OpenID parameters and make repeated POST requests.If you want to implement batch brushing of tickets or automated ticket brushing operations, you can implement ticket brushing requests through Python scripts; you can even use LoadRunner.
Run VoteRobot.py , the output log is as follows:
======== Start to vote zpid(38), Total votes: 3
1 tickets has been voted, the next ticket will be voted after 35 seconds.
2 tickets has been voted, the next ticket will be voted after 31 seconds.
3 tickets has been voted, the next ticket will be voted after 10 seconds.
======== Voting Ended!
It should be noted that it is usually best to have a random time interval when automating ticket brushing, and it is best to dynamically simulate different devices, that is, modify User-Agent . Otherwise, the server can easily identify cheating behavior.
Seeing this, some students may be secretly happy. Can this method be used to "swipe votes" in future votes?
Sadly, of course not.
In fact, the loopholes in the case in this article are very low-level. However, there are still a large proportion of voting activities that use this model.
It's also easy to tell whether a voting campaign could be cheated in this way. Using the method in this article, if the URL of the event is not official WeChat, and there is no additional verification in the entire voting process, then the possibility of cheating is very high; then capture the packet to see the communication interaction process, and use After modifying the parameters of the network request tool and re-requesting, you can verify whether cheating is really possible.
In addition, some people may want to ask, is it impossible to prevent "vote manipulation" in online voting activities?
The answer is that it is indeed difficult to completely eliminate it. Have you ever heard of the 12306 scalper? Have you ever heard of the Apple Store professionally ranking apps? Have you ever heard of the “Internet trolls” and the “50 Cent Party”?
However, event organizers can use some means to greatly raise the threshold for cheating. For example, many current activities use the following methods:
No matter which of these two methods is used, the "vote brushing" method in this article is completely ineffective.