맬웨어 및 기타 항목을 안전하게 에뮬레이트하기 위한 x86 32/64비트 에뮬레이터입니다.

https://www.youtube.com/@JesusOlmos-wm8ch/videos https://www.youtube.com/watch?v=yJ3Bgv3maq0
Python 앱 https://pypi.org/search/?q=pyscemu
Rust 앱 https://crates.io/crates/libscemu
SCEMU emulator for malware 0.7.10
@sha0coder
USAGE:
scemu [FLAGS] [OPTIONS]
FLAGS:
-6, --64bits enable 64bits architecture emulation
--banzai skip unimplemented instructions, and keep up emulating what can be emulated
-h, --help Prints help information
-l, --loops show loop interations, it is slow.
-m, --memory trace all the memory accesses read and write.
-n, --nocolors print without colors for redirectin to a file >out
-r, --regs print the register values in every step.
-p, --stack trace stack on push/pop
-t, --test test mode
-V, --version Prints version information
-v, --verbose -vv for view the assembly, -v only messages, without verbose only see the api calls and goes
faster
OPTIONS:
-b, --base <ADDRESS> set base address for code
-c, --console <NUMBER> select in which moment will spawn the console to inspect.
-C, --console_addr <ADDRESS> spawn console on first eip = address
-a, --entry <ADDRESS> entry point of the shellcode, by default starts from the beginning.
-f, --filename <FILE> set the shellcode binary file.
-i, --inspect <DIRECTION> monitor memory like: -i 'dword ptr [ebp + 0x24]
-M, --maps <PATH> select the memory maps folder
--mxcsr <MXCSR> set mxcsr register
--r10 <R10> set r10 register
--r11 <R11> set r11 register
--r12 <R12> set r12 register
--r13 <R13> set r13 register
--r14 <R14> set r14 register
--r15 <R15> set r15 register
--r8 <R8> set r8 register
--r9 <R9> set r9 register
--rax <RAX> set rax register
--rbp <RBP> set rbp register
--rbx <RBX> set rbx register
--rcx <RCX> set rcx register
--rdi <RDI> set rdi register
--rdx <RDX> set rdx register
-R, --reg <REGISTER1,REGISTER2> trace a specific register in every step, value and content
--rflags <RFLAGS> set rflags register
--rsi <RSI> set rsi register
--rsp <RSP> set rsp register
-x, --script <SCRIPT> launch an emulation script, see scripts_examples folder
--stack_address <ADDRESS> set stack address
-s, --string <ADDRESS> monitor string on a specific address
-T, --trace <TRACE_FILENAME> output trace to specified file
scemu는 execve() 인터럽트를 감지하는 간단한 쉘코드를 에뮬레이트합니다. 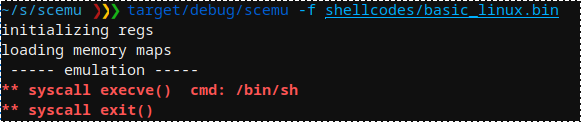
중지할 라인을 선택하고 메모리를 검사합니다. 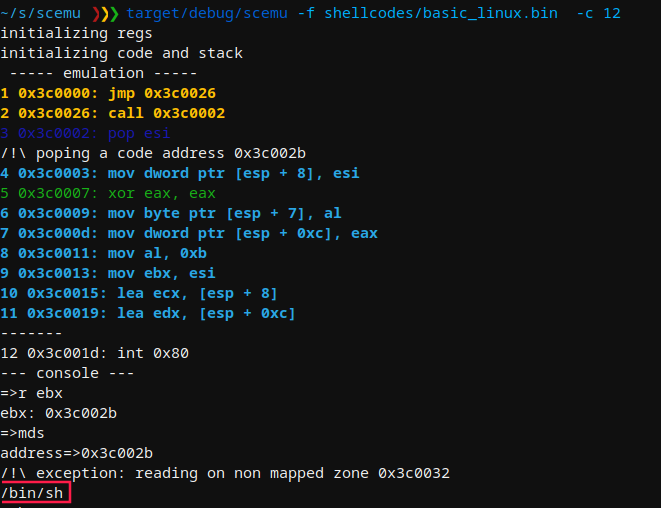
Linux에서 거의 200만 개의 GuLoader win32 명령을 에뮬레이션한 후 CPUID 및 기타 트릭을 위조하여 디버거를 혼란스럽게 하는 sigtrap에 도달합니다. 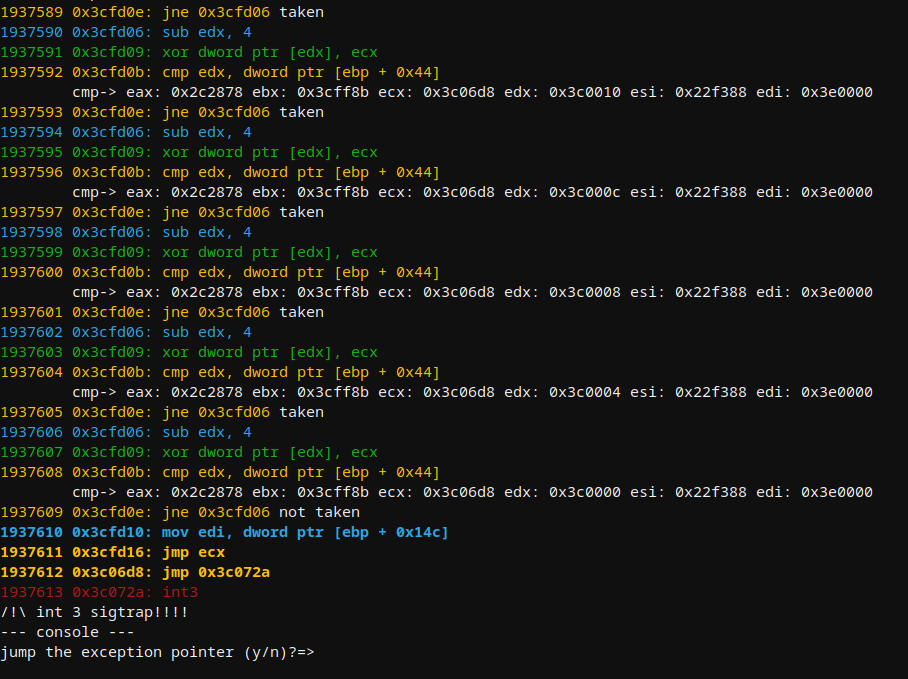
API 로더의 메모리 덤프 예. 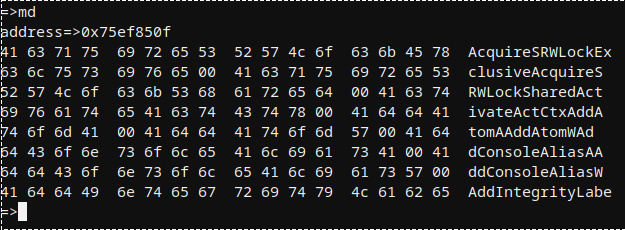
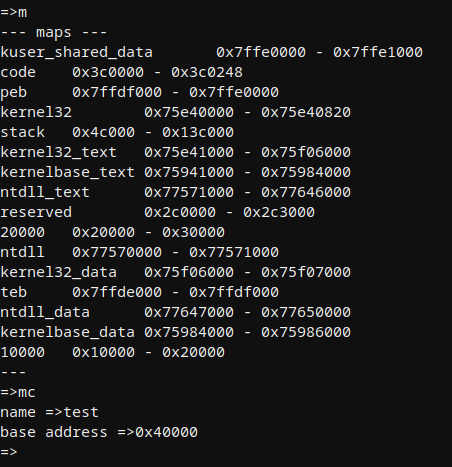
기본적으로 여러 맵이 있으며 LoadLibraryA와 같은 API를 사용하거나 콘솔에서 수동으로 더 많은 맵을 생성할 수 있습니다.
메시지를 인쇄하는 LdrLoadDLl()을 기반으로 기본 Windows 쉘코드를 에뮬레이션합니다. 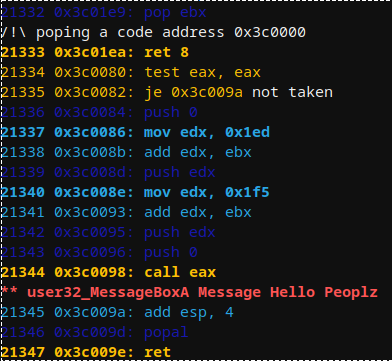
콘솔을 사용하면 CPU의 현재 상태를 편집하여 볼 수 있습니다.
--- console ---
=>h
--- help ---
q ...................... quit
cls .................... clear screen
h ...................... help
s ...................... stack
v ...................... vars
r ...................... register show all
r reg .................. show reg
rc ..................... register change
f ...................... show all flags
fc ..................... clear all flags
fz ..................... toggle flag zero
fs ..................... toggle flag sign
c ...................... continue
ba ..................... breakpoint on address
bi ..................... breakpoint on instruction number
bmr .................... breakpoint on read memory
bmw .................... breakpoint on write memory
bc ..................... clear breakpoint
n ...................... next instruction
eip .................... change eip
push ................... push dword to the stack
pop .................... pop dword from stack
fpu .................... fpu view
md5 .................... check the md5 of a memory map
seh .................... view SEH
veh .................... view vectored execption pointer
m ...................... memory maps
ma ..................... memory allocs
mc ..................... memory create map
mn ..................... memory name of an address
ml ..................... memory load file content to map
mr ..................... memory read, speficy ie: dword ptr [esi]
mw ..................... memory read, speficy ie: dword ptr [esi] and then: 1af
md ..................... memory dump
mrd .................... memory read dwords
mds .................... memory dump string
mdw .................... memory dump wide string
mdd .................... memory dump to disk
mt ..................... memory test
ss ..................... search string
sb ..................... search bytes
sba .................... search bytes in all the maps
ssa .................... search string in all the maps
ll ..................... linked list walk
d ...................... dissasemble
dt ..................... dump structure
enter .................. step into
Cobalt Strike API 로더는 Metasploit과 동일하며 이를 에뮬레이션합니다. 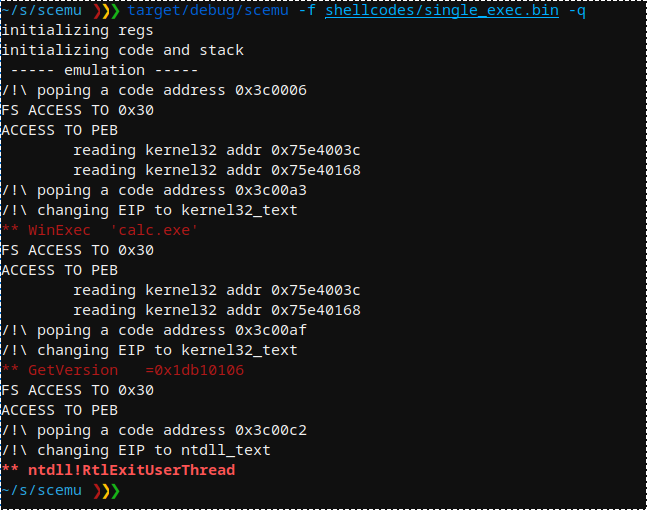
Cobalt Strike API 호출: 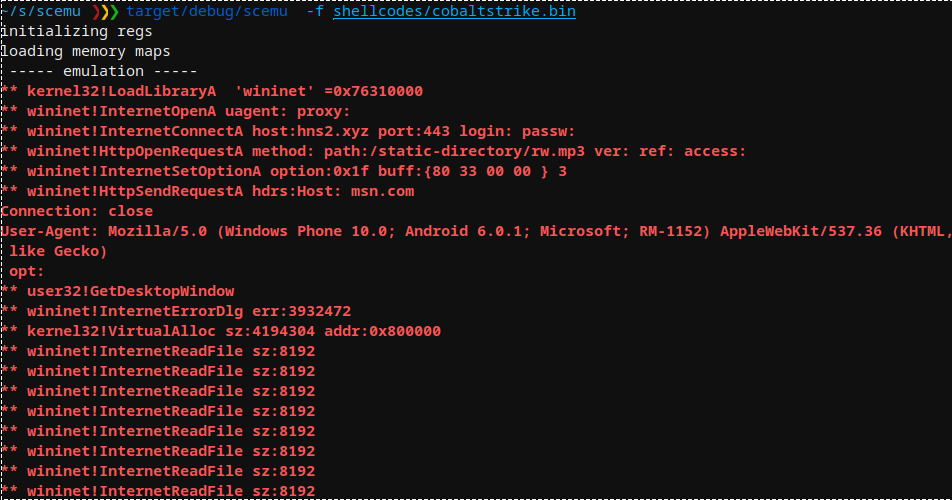
Metasploit rshell API 호출: 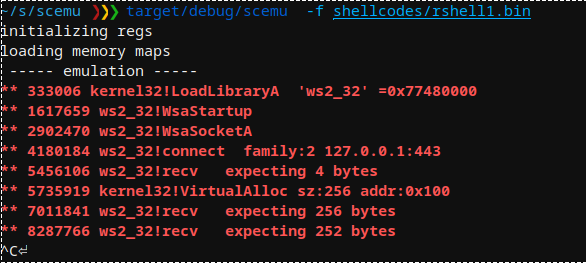
다형성을 숨기기 위해 소수의 fpu를 사용하는 Metasploit SGN 인코더: 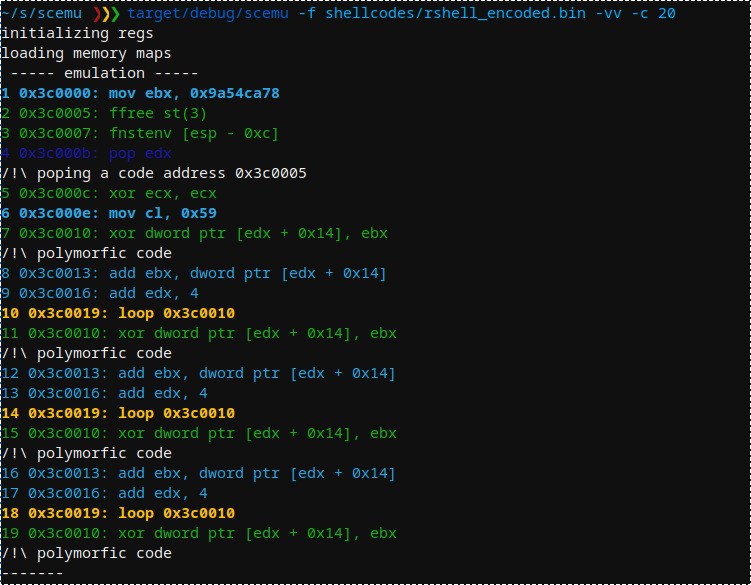
fpu로 시작하는 Metasploit shikata-ga-nai 인코더: 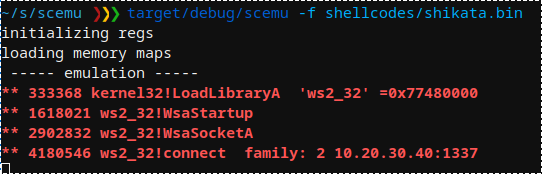
PEB 구조 표시:
=>dt
structure=>peb
address=>0x7ffdf000
PEB {
reserved1: [
0x0,
0x0,
],
being_debugged: 0x0,
reserved2: 0x0,
reserved3: [
0xffffffff,
0x400000,
],
ldr: 0x77647880,
process_parameters: 0x2c1118,
reserved4: [
0x0,
0x2c0000,
0x77647380,
],
alt_thunk_list_ptr: 0x0,
reserved5: 0x0,
reserved6: 0x6,
reserved7: 0x773cd568,
reserved8: 0x0,
alt_thunk_list_ptr_32: 0x0,
reserved9: [
0x0,
...
PEB_LDR_DATA 구조 표시:
=>dt
structure=>PEB_LDR_DATA
address=>0x77647880
PebLdrData {
length: 0x30,
initializated: 0x1,
sshandle: 0x0,
in_load_order_module_list: ListEntry {
flink: 0x2c18b8,
blink: 0x2cff48,
},
in_memory_order_module_list: ListEntry {
flink: 0x2c18c0,
blink: 0x2cff50,
},
in_initialization_order_module_list: ListEntry {
flink: 0x2c1958,
blink: 0x2d00d0,
},
entry_in_progress: ListEntry {
flink: 0x0,
blink: 0x0,
},
}
=>
LDR_DATA_TABLE_ENTRY 및 첫 번째 모듈 이름 표시
=>dt
structure=>LDR_DATA_TABLE_ENTRY
address=>0x2c18c0
LdrDataTableEntry {
reserved1: [
0x2c1950,
0x77647894,
],
in_memory_order_module_links: ListEntry {
flink: 0x0,
blink: 0x0,
},
reserved2: [
0x0,
0x400000,
],
dll_base: 0x4014e0,
entry_point: 0x1d000,
reserved3: 0x40003e,
full_dll_name: 0x2c1716,
reserved4: [
0x0,
0x0,
0x0,
0x0,
0x0,
0x0,
0x0,
0x0,
],
reserved5: [
0x17440012,
0x4000002c,
0xffff0000,
],
checksum: 0x1d6cffff,
reserved6: 0xa640002c,
time_date_stamp: 0xcdf27764,
}
=>
악성 코드가 예외에 뭔가를 숨기고 있습니다.
3307726 0x4f9673: push ebp
3307727 0x4f9674: push edx
3307728 0x4f9675: push eax
3307729 0x4f9676: push ecx
3307730 0x4f9677: push ecx
3307731 0x4f9678: push 4F96F4h
3307732 0x4f967d: push dword ptr fs:[0]
Reading SEH 0x0
-------
3307733 0x4f9684: mov eax,[51068Ch]
--- console ---
=>
예외 구조를 살펴보겠습니다.
--- console ---
=>r esp
esp: 0x22de98
=>dt
structure=>cppeh_record
address=>0x22de98
CppEhRecord {
old_esp: 0x0,
exc_ptr: 0x4f96f4,
next: 0xfffffffe,
exception_handler: 0xfffffffe,
scope_table: PScopeTableEntry {
enclosing_level: 0x278,
filter_func: 0x51068c,
handler_func: 0x288,
},
try_level: 0x288,
}
=>
여기에는 오류 루틴 0x4f96f4와 필터 0x51068c가 있습니다.