cloudgrep 搜尋雲端儲存。

它目前支援在 AWS S3、Azure 儲存或 Google 雲端儲存中搜尋記錄文件,可以選擇使用 gzip (.gz) 或 zip (.zip) 壓縮。
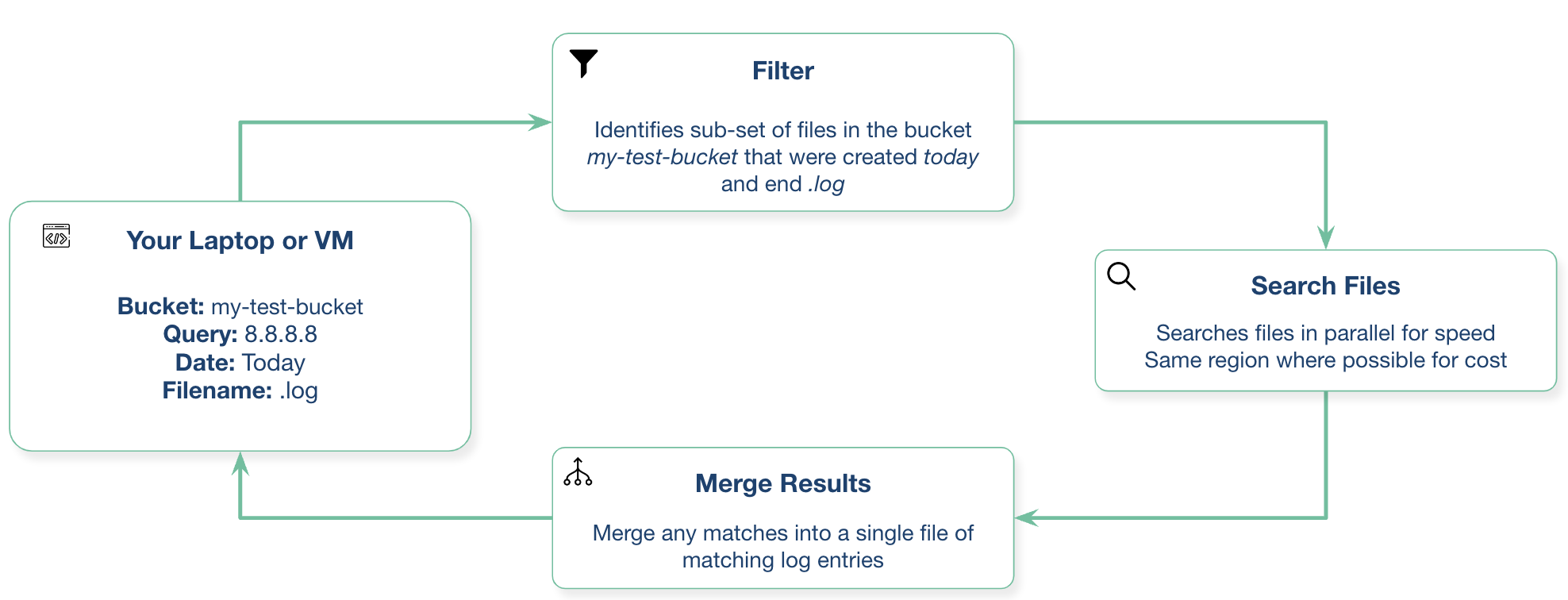
簡單的例子:
./cloudgrep --bucket test-s3-access-logs --query 9RXXKPREHHTFQD77
python3 cloudgrep.py -b test-s3-access-logs -q 9RXXKPREHHTFQD77
簡單的 Azure 範例:
python3 cloudgrep.py -an some_account -cn some_container -q my_search
簡單的谷歌範例:
python3 cloudgrep.py -gb my-gcp-bucket -q my_search
簡單的 CloudTrail 日誌範例,以 JSON 形式輸出結果:
python3 cloudgrep.py -b test-s3-access-logs -q 9RXXKPREHHTFQD77 -lt cloudtrail -jo
簡單的自訂日誌範例:
python3 cloudgrep.py -b test-s3-access-logs -q 9RXXKPREHHTFQD77 -lf json -lp Records
更複雜的例子:
python3 cloudgrep.py -b test-s3-access-logs --prefix "logs/" --filename ".log" -q 9RXXKPREHHTFQD77 -s "2023-01-09 20:30:00" -e "2023-01-09 20:45:00" --file_size 10000 --debug
將輸出儲存到文件中:
python3 cloudgrep.py -b test-s3-access-logs -q 9RXXKPREHHTFQD77 --hide_filenames > matching_events.log
輸出範例:
[2023-11-30 13:37:12,416] - Bucket is in region: us-east-2 : Search from the same region to avoid egress charges.
[2023-11-30 13:37:12,417] - Searching 11 files in test-s3-access-logs for 9RXXKPREHHTFQD77...
{"key_name": "access2023-01-09-20-34-20-EAC533CB93B4ACBE", "line": "abbd82b5ad5dc5d024cd1841d19c0cf2fd7472c47a1501ececde37fe91adc510 bucket-72561-s3bucketalt-1my9piwesfim7 [09/Jan/2023:19:20:00 +0000] 1.125.222.333 arn:aws:sts::000011110470:assumed-role/bucket-72561-myResponseRole-1WP2IOKDV7B4Y/1673265251.340187 9RXXKPREHHTFQD77 REST.GET.BUCKET - "GET /?list-type=2&prefix=-collector%2Fproject-&start-after=&encoding-type=url HTTP/1.1" 200 - 946 - 33 32 "-" "Boto3/1.21.24 Python/3.9.2 Linux/5.10.0-10-cloud-amd64 Botocore/1.24.46" - aNPuHKw== SigV4 ECDHE-RSA-AES128-GCM-SHA256 AuthHeader bucket-72561-s3bucketalt-1my9piwesfim7.s3.us-east-2.amazonaws.com TLSv1.2 - -"}
usage: cloudgrep.py [-h] [-b BUCKET] [-an ACCOUNT_NAME] [-cn CONTAINER_NAME] [-gb GOOGLE_BUCKET] [-q QUERY]
[-v FILE] [-y YARA] [-p PREFIX] [-f FILENAME] [-s START_DATE] [-e END_DATE]
[-fs FILE_SIZE] [-pr PROFILE] [-d] [-hf] [-lt LOG_TYPE] [-lf LOG_FORMAT]
[-lp LOG_PROPERTIES] [-jo JSON_OUTPUT]
CloudGrep searches is grep for cloud storage like S3 and Azure Storage. Version: 1.0.5
options:
-h, --help show this help message and exit
-b BUCKET, --bucket BUCKET
AWS S3 Bucket to search. E.g. my-bucket
-an ACCOUNT_NAME, --account-name ACCOUNT_NAME
Azure Account Name to Search
-cn CONTAINER_NAME, --container-name CONTAINER_NAME
Azure Container Name to Search
-gb GOOGLE_BUCKET, --google-bucket GOOGLE_BUCKET
Google Cloud Bucket to Search
-q QUERY, --query QUERY
Text to search for. Will be parsed as a Regex. E.g. example.com
-v FILE, --file FILE File containing a list of words or regular expressions to search for. One per line.
-y YARA, --yara YARA File containing Yara rules to scan files.
-p PREFIX, --prefix PREFIX
Optionally filter on the start of the Object name. E.g. logs/
-f FILENAME, --filename FILENAME
Optionally filter on Objects that match a keyword. E.g. .log.gz
-s START_DATE, --start_date START_DATE
Optionally filter on Objects modified after a Date or Time. E.g. 2022-01-01
-e END_DATE, --end_date END_DATE
Optionally filter on Objects modified before a Date or Time. E.g. 2022-01-01
-fs FILE_SIZE, --file_size FILE_SIZE
Optionally filter on Objects smaller than a file size, in bytes. Defaults to 100 Mb.
-pr PROFILE, --profile PROFILE
Set an AWS profile to use. E.g. default, dev, prod.
-d, --debug Enable Debug logging.
-hf, --hide_filenames
Dont show matching filenames.
-lt LOG_TYPE, --log_type LOG_TYPE
Return individual matching log entries based on pre-defined log types, otherwise
custom log_format and log_properties can be used. E.g. cloudtrail.
-lf LOG_FORMAT, --log_format LOG_FORMAT
Define custom log format of raw file to parse before applying search logic. Used if
--log_type is not defined. E.g. json.
-lp LOG_PROPERTIES, --log_properties LOG_PROPERTIES
Define custom list of properties to traverse to dynamically extract final list of log
records. Used if --log_type is not defined. E.g. [Records].
-jo JSON_OUTPUT, --json_output JSON_OUTPUT
Output as JSON.
安裝方式: pip3 install -r requirements.txt或在此下載最新編譯版本
您可以從本機筆記型電腦或雲端提供者的虛擬機器執行此程式。
這需要python3.10或更高版本
建置方式: docker build -t cloudgrep .
運作方式: docker run --rm -ti cloudgrep
傳遞環境變量,例如對於 AWS: docker run --rm --env-file <(env|grep AWS) -ti cloudgrep
您的系統需要存取 S3 儲存桶。例如,如果您在筆記型電腦上運行,則需要設定 AWS CLI。如果您在 EC2 上執行,執行個體設定檔可能是最佳選擇。
如果您在與 S3 儲存桶位於相同區域的 EC2 執行個體上執行且具有 S3 的 VPC 終端節點,則可以避免出口費用。您可以透過多種方式進行身份驗證。
使用 Azure 進行身份驗證的最簡單方法是先執行:
az login
這將開啟一個瀏覽器視窗並提示您登入 Azure。
您需要建立一個服務帳戶並下載憑證文件,然後設定:
export GOOGLE_APPLICATION_CREDENTIALS="/Users/creds.json"
我們歡迎對此項目做出任何貢獻!請透過拉取請求添加。
未來可能的工作可能包括:
如果您有任何問題或建議,請開啟 GitHub 問題。這不是官方支援的 Cado Security 產品。