.__ .__ .__ __
| |__ ____________ | | ____ |__|/ |_ __
| | / ___/____ | | / _ | __ (,--------'()'--o
| Y ___ | |_> > |_( <_> ) || | (_ ___ /~"
|___| /____ >| __/|____/____/|__||__| (_)_) (_)_)
/ / |__|
作者:尼古拉斯·卡羅洛 [email protected]
版權所有:© 2020,尼可拉斯卡羅洛。
日期:2020-05-16
版本:2.1.0
hsploit是一個用Python開發的用於Exploit-DB的高階命令列搜尋引擎,其誕生的目的是向使用者展示最準確的搜尋結果。
nicolas@carolo:~$ hsploit -s "wordpress core 2.1.0"
11 exploits and 0 shellcodes found.
EXPLOITS:
+-------+--------------------------------------------------------------------------------------------+
| ID | DESCRIPTION |
+=======+============================================================================================+
| 35414 | WORDPRESS CORE < 4.0.1 - Denial of Service |
+-------+--------------------------------------------------------------------------------------------+
| 47800 | WORDPRESS CORE < 5.3.x - 'xmlrpc.php' Denial of Service |
+-------+--------------------------------------------------------------------------------------------+
| 6 | WORDPRESS CORE 2.1.0 - 'cache' Remote Shell Injection |
+-------+--------------------------------------------------------------------------------------------+
| 4397 | WORDPRESS CORE 1.5.1.1 < 2.2.2 - Multiple Vulnerabilities |
+-------+--------------------------------------------------------------------------------------------+
| 10088 | WORDPRESS CORE 2.0 < 2.7.1 - 'admin.php' Module Configuration Security Bypass |
+-------+--------------------------------------------------------------------------------------------+
| 10089 | WORDPRESS CORE < 2.8.5 - Unrestricted Arbitrary File Upload / Arbitrary PHP Code Execution |
+-------+--------------------------------------------------------------------------------------------+
| 29754 | WORDPRESS CORE < 2.1.2 - 'PHP_Self' Cross-Site Scripting |
+-------+--------------------------------------------------------------------------------------------+
| 41497 | WORDPRESS CORE < 4.7.1 - Username Enumeration |
+-------+--------------------------------------------------------------------------------------------+
| 41963 | WORDPRESS CORE < 4.7.4 - Unauthorized Password Reset |
+-------+--------------------------------------------------------------------------------------------+
| 44949 | WORDPRESS CORE < 4.9.6 - (Authenticated) Arbitrary File Deletion |
+-------+--------------------------------------------------------------------------------------------+
| 47690 | WORDPRESS CORE < 5.2.3 - Viewing Unauthenticated/Password/Private Posts |
+-------+--------------------------------------------------------------------------------------------+
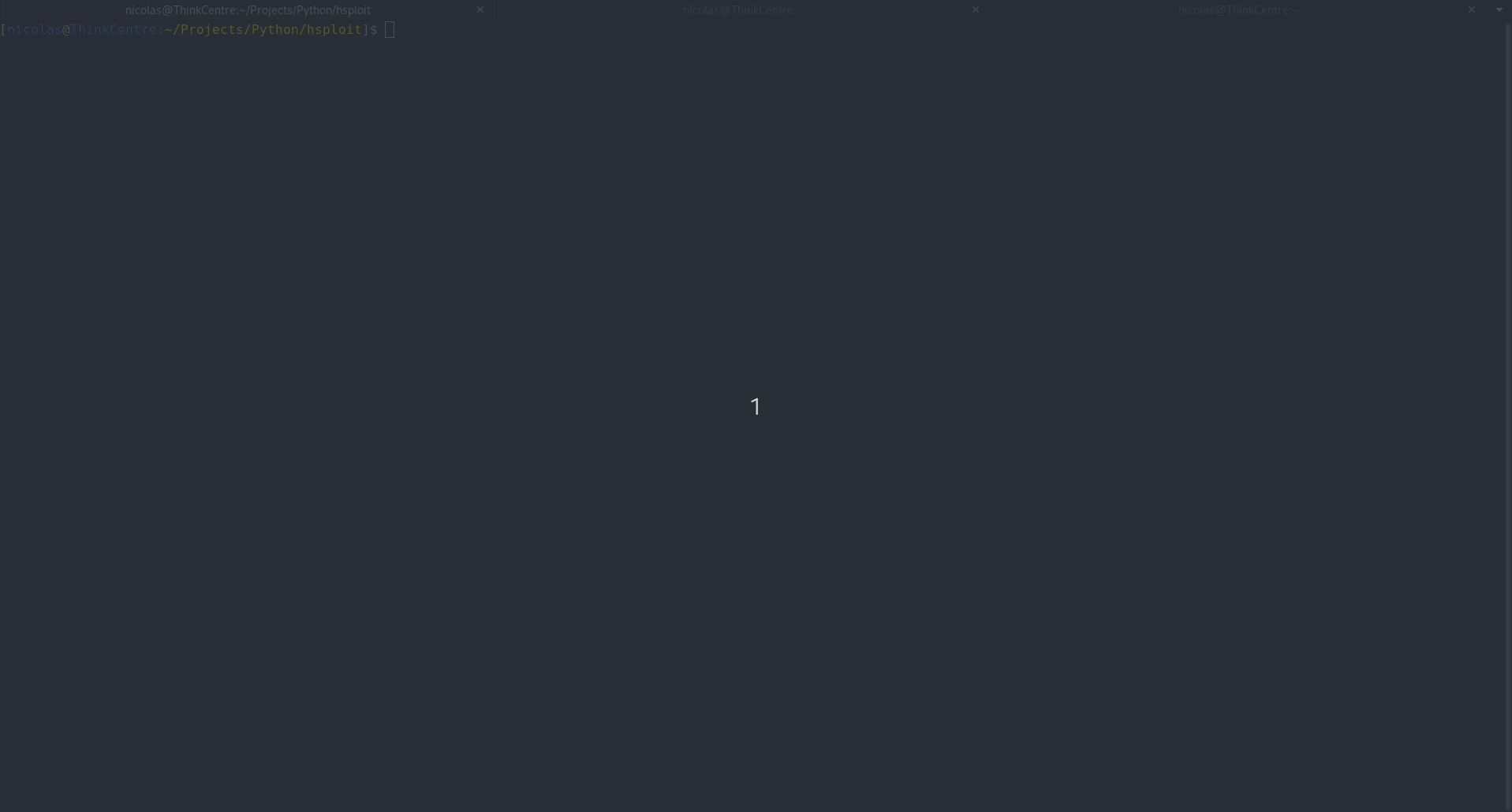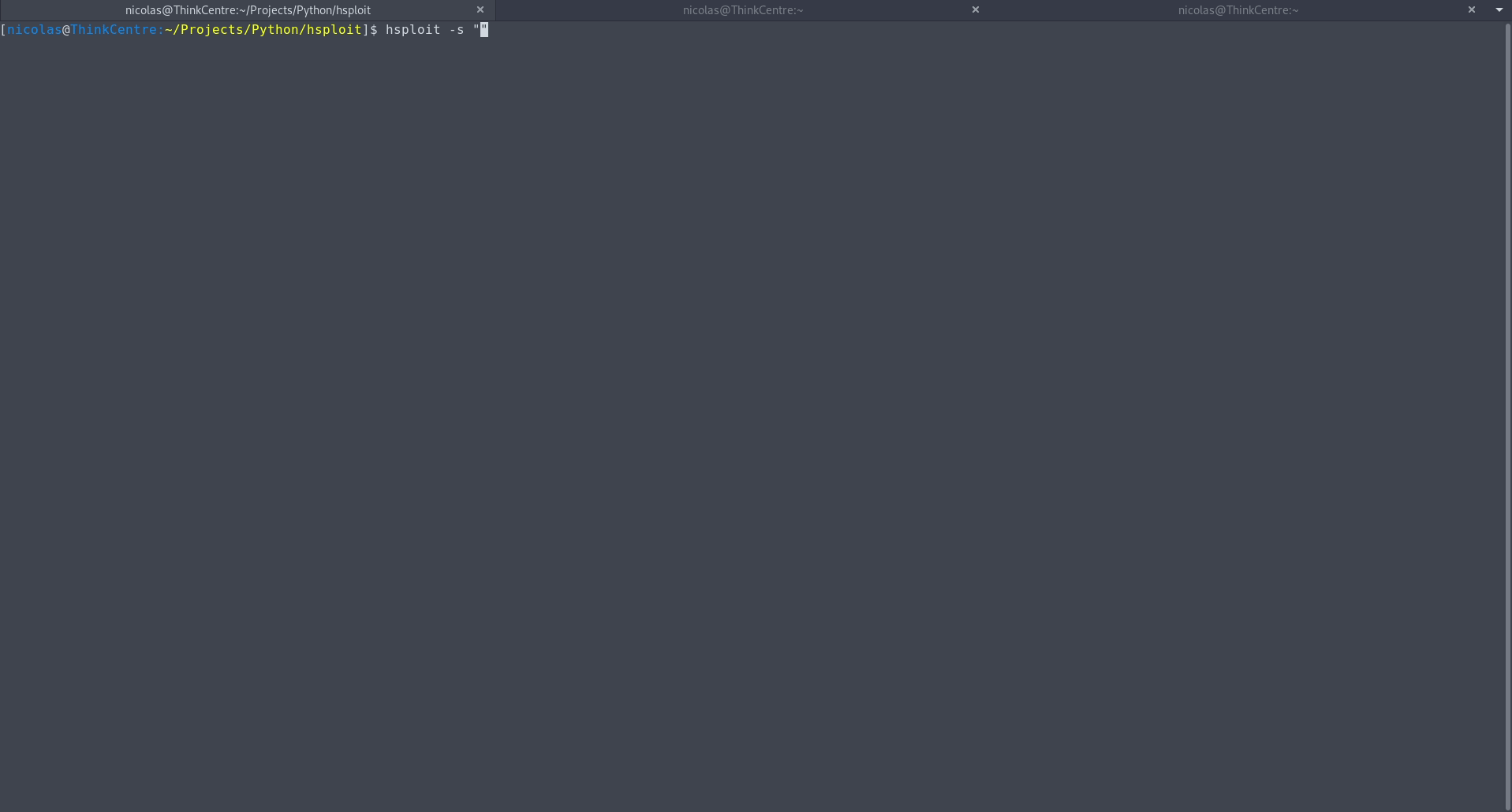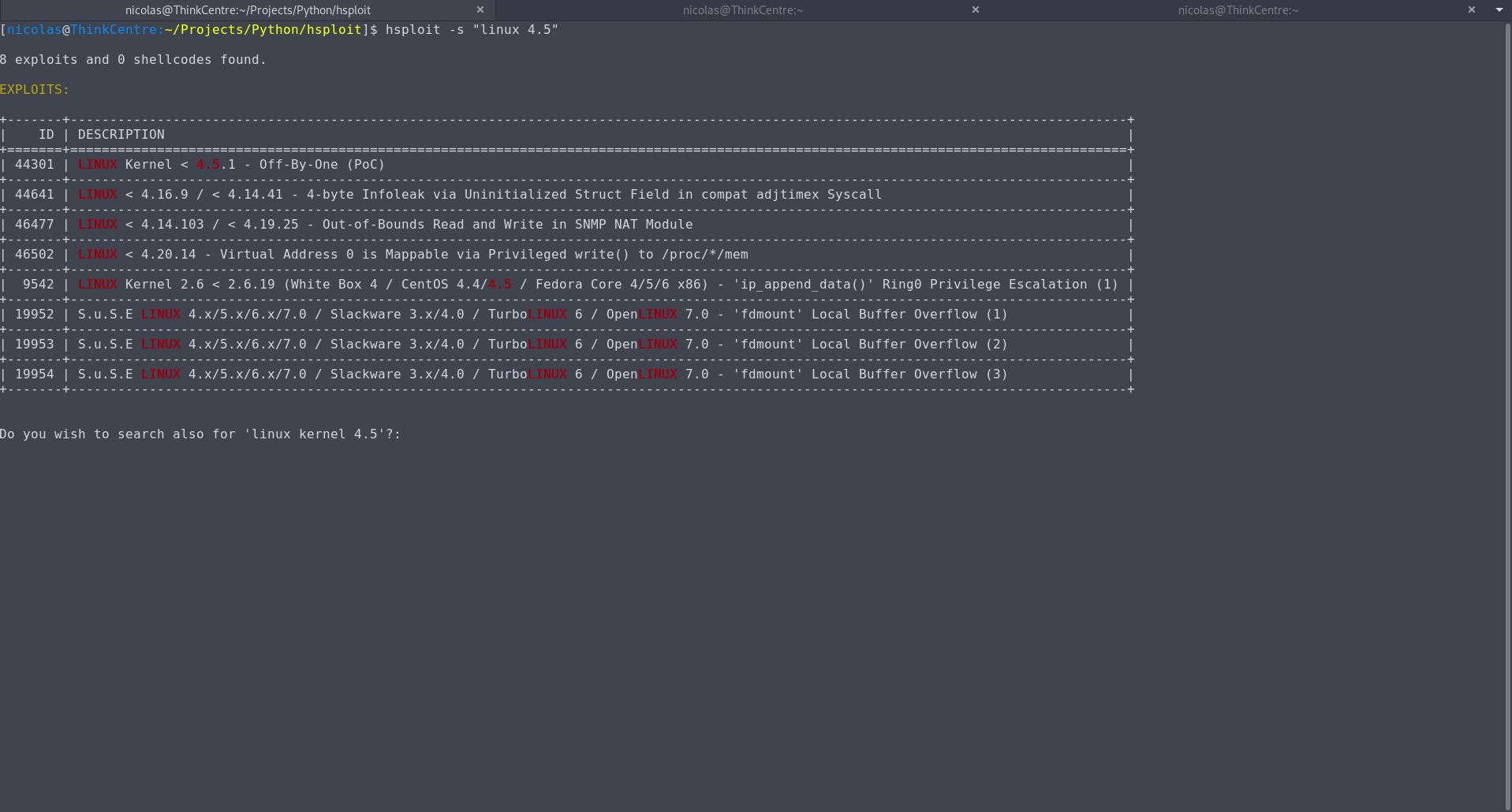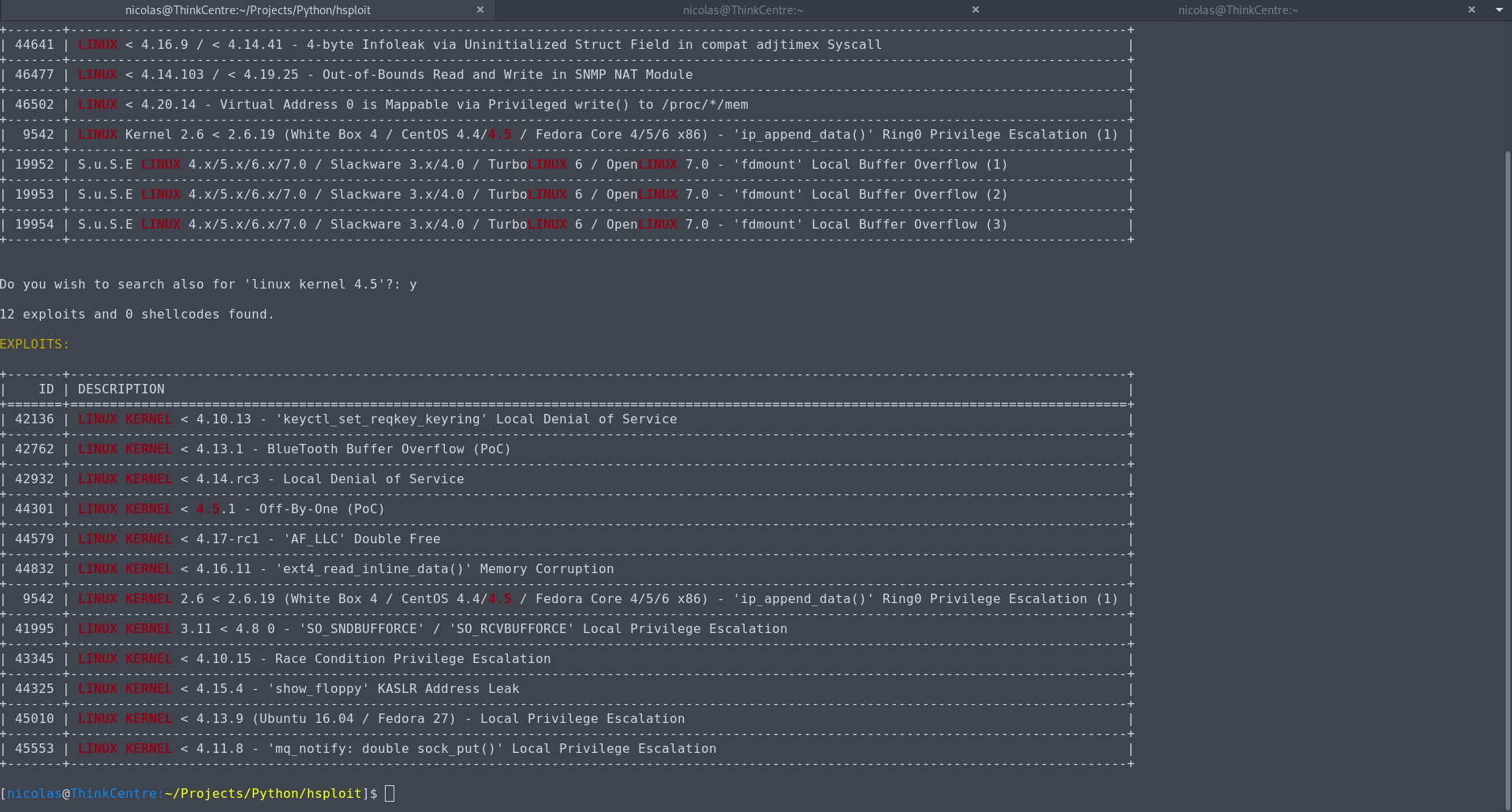
nicolas@carolo:~$ hsploit -s "linux kernel 4.4.1"
14 exploits and 0 shellcodes found.
EXPLOITS:
+-------+--------------------------------------------------------------------------------------------------+
| ID | DESCRIPTION |
+=======+==================================================================================================+
| 42136 | LINUX KERNEL < 4.10.13 - 'keyctl_set_reqkey_keyring' Local Denial of Service |
+-------+--------------------------------------------------------------------------------------------------+
| 42762 | LINUX KERNEL < 4.13.1 - BlueTooth Buffer Overflow (PoC) |
+-------+--------------------------------------------------------------------------------------------------+
| 42932 | LINUX KERNEL < 4.14.rc3 - Local Denial of Service |
+-------+--------------------------------------------------------------------------------------------------+
| 44301 | LINUX KERNEL < 4.5.1 - Off-By-One (PoC) |
+-------+--------------------------------------------------------------------------------------------------+
| 44579 | LINUX KERNEL < 4.17-rc1 - 'AF_LLC' Double Free |
+-------+--------------------------------------------------------------------------------------------------+
| 44832 | LINUX KERNEL < 4.16.11 - 'ext4_read_inline_data()' Memory Corruption |
+-------+--------------------------------------------------------------------------------------------------+
| 39277 | LINUX KERNEL 4.4.1 - REFCOUNT Overflow Use-After-Free in Keyrings Local Privilege Escalation (1) |
+-------+--------------------------------------------------------------------------------------------------+
| 40003 | LINUX KERNEL 4.4.1 - REFCOUNT Overflow Use-After-Free in Keyrings Local Privilege Escalation (2) |
+-------+--------------------------------------------------------------------------------------------------+
| 39772 | LINUX KERNEL 4.4.x (Ubuntu 16.04) - 'double-fdput()' bpf(BPF_PROG_LOAD) Privilege Escalation |
+-------+--------------------------------------------------------------------------------------------------+
| 41995 | LINUX KERNEL 3.11 < 4.8 0 - 'SO_SNDBUFFORCE' / 'SO_RCVBUFFORCE' Local Privilege Escalation |
+-------+--------------------------------------------------------------------------------------------------+
| 43345 | LINUX KERNEL < 4.10.15 - Race Condition Privilege Escalation |
+-------+--------------------------------------------------------------------------------------------------+
| 44325 | LINUX KERNEL < 4.15.4 - 'show_floppy' KASLR Address Leak |
+-------+--------------------------------------------------------------------------------------------------+
| 45010 | LINUX KERNEL < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation |
+-------+--------------------------------------------------------------------------------------------------+
| 45553 | LINUX KERNEL < 4.11.8 - 'mq_notify: double sock_put()' Local Privilege Escalation |
+-------+--------------------------------------------------------------------------------------------------+
使用進階搜尋( -sad選項),您可以使用以下篩選器來過濾搜尋結果:
AND或OR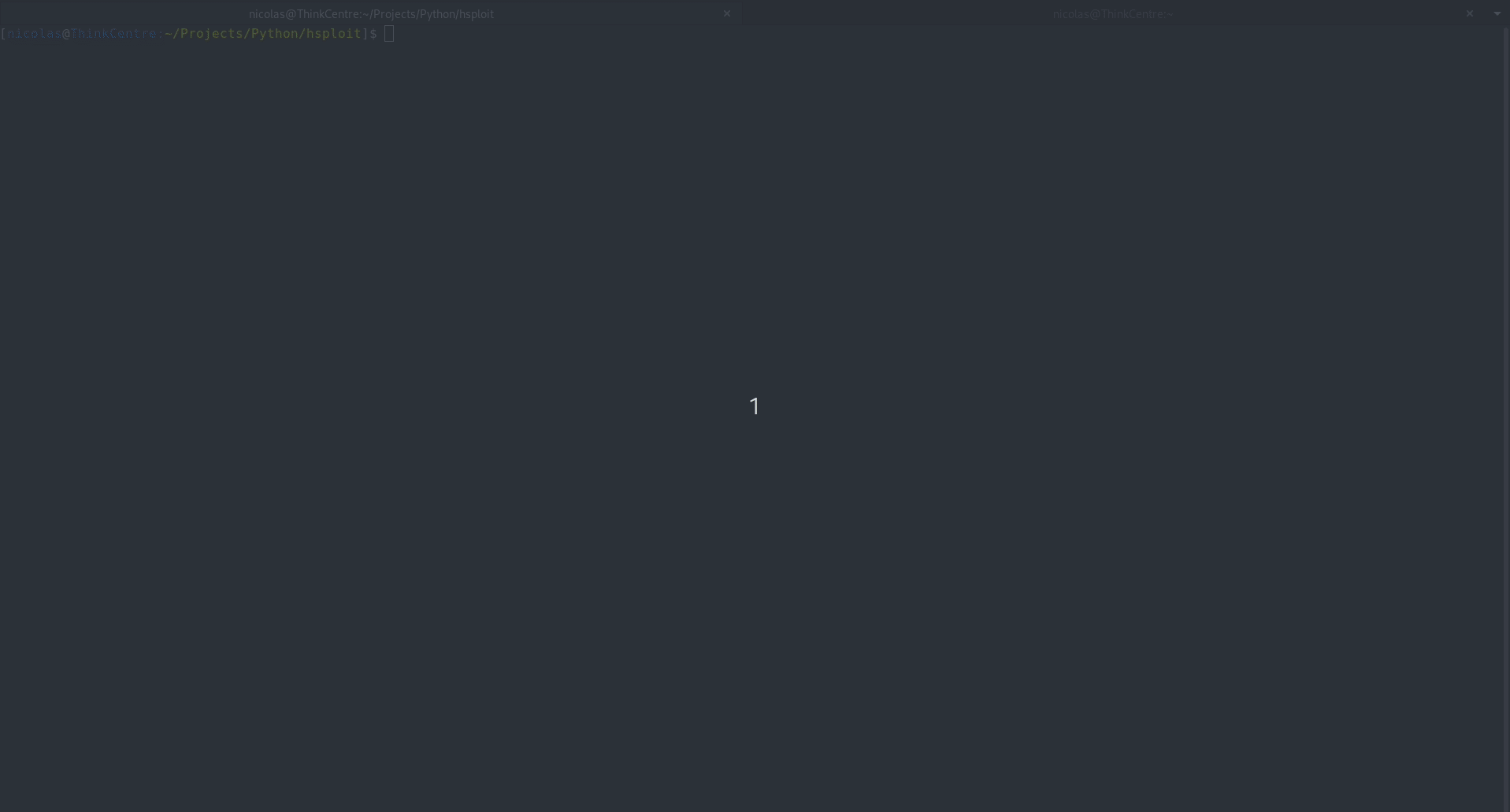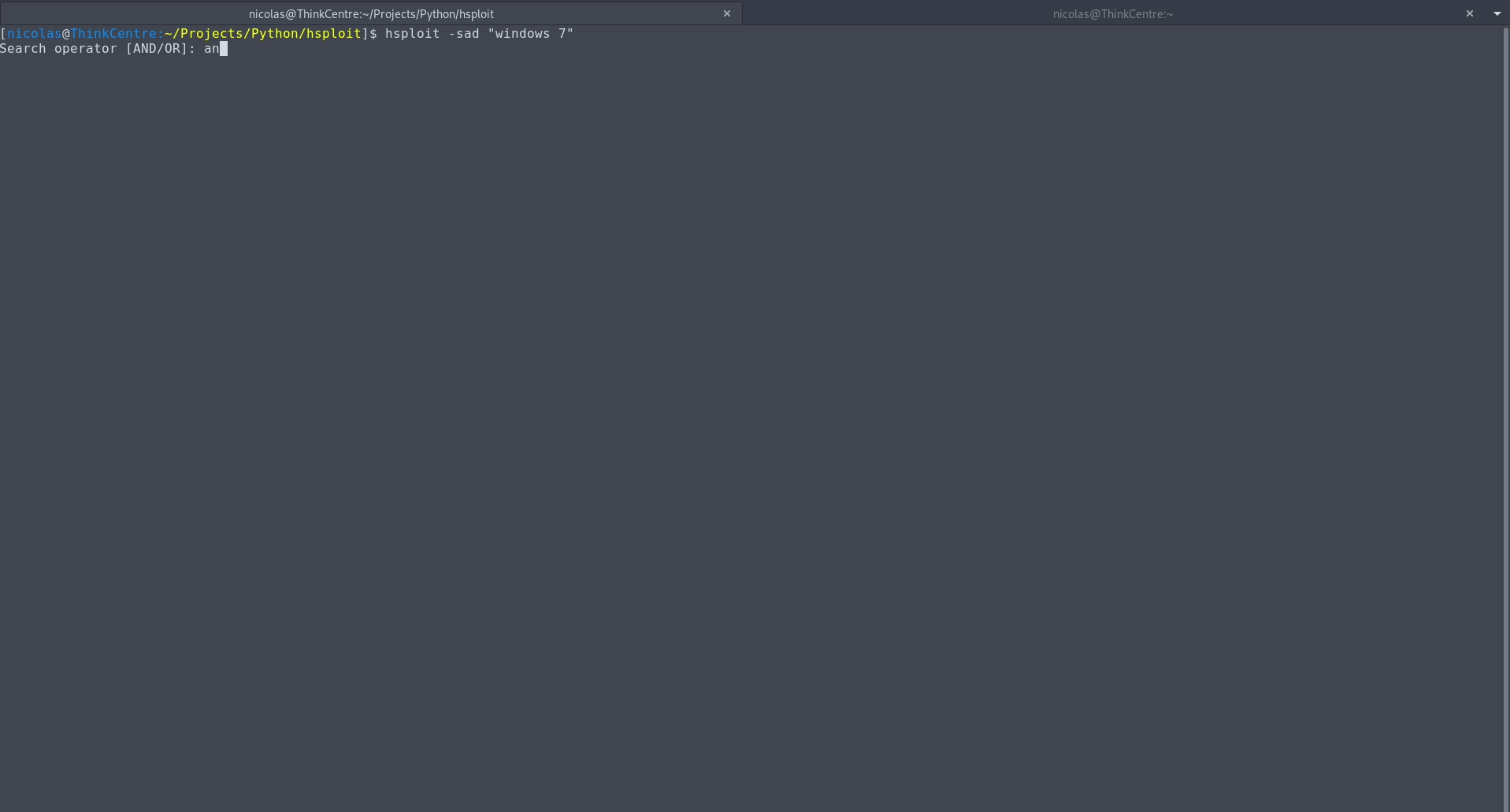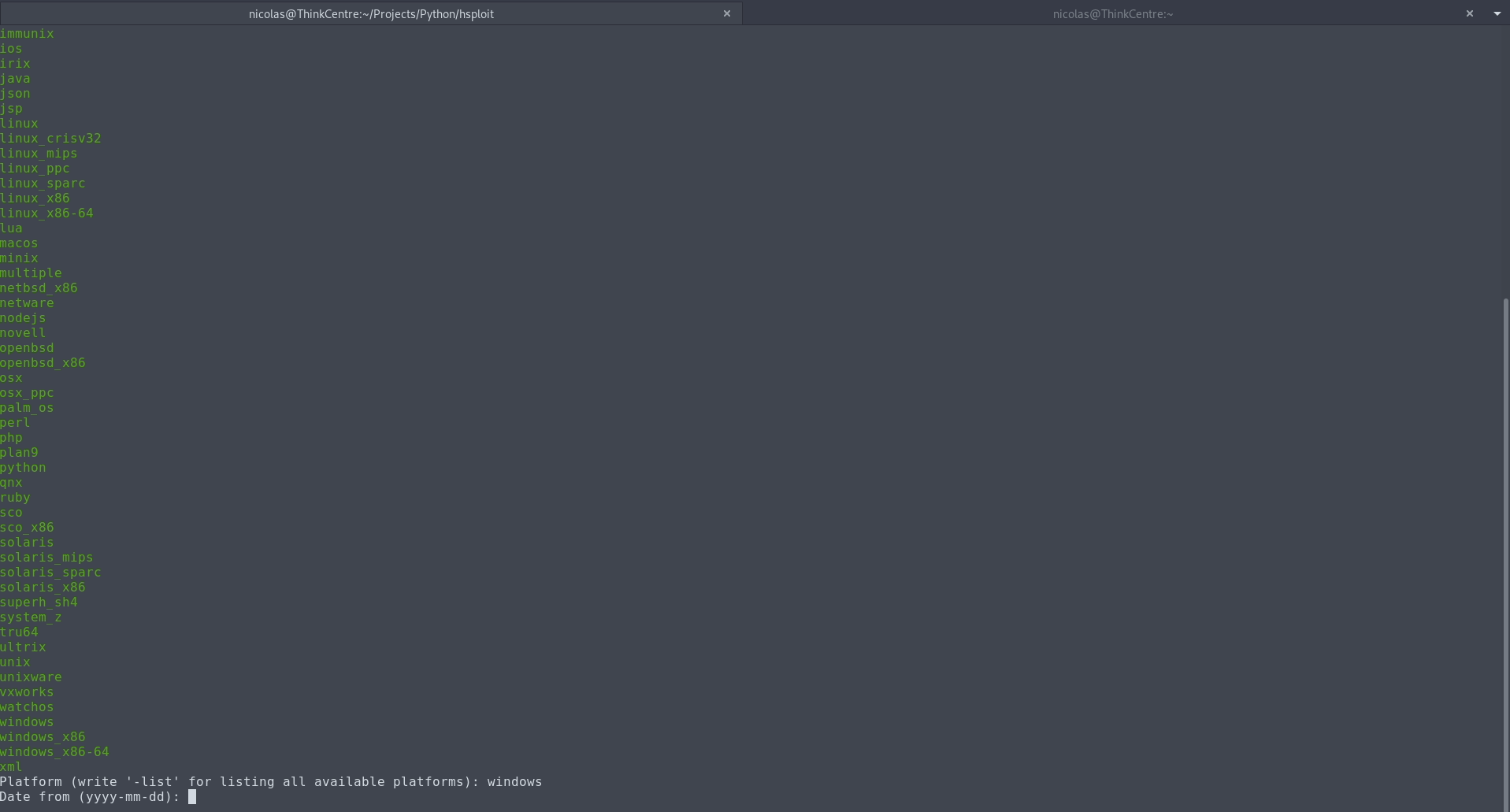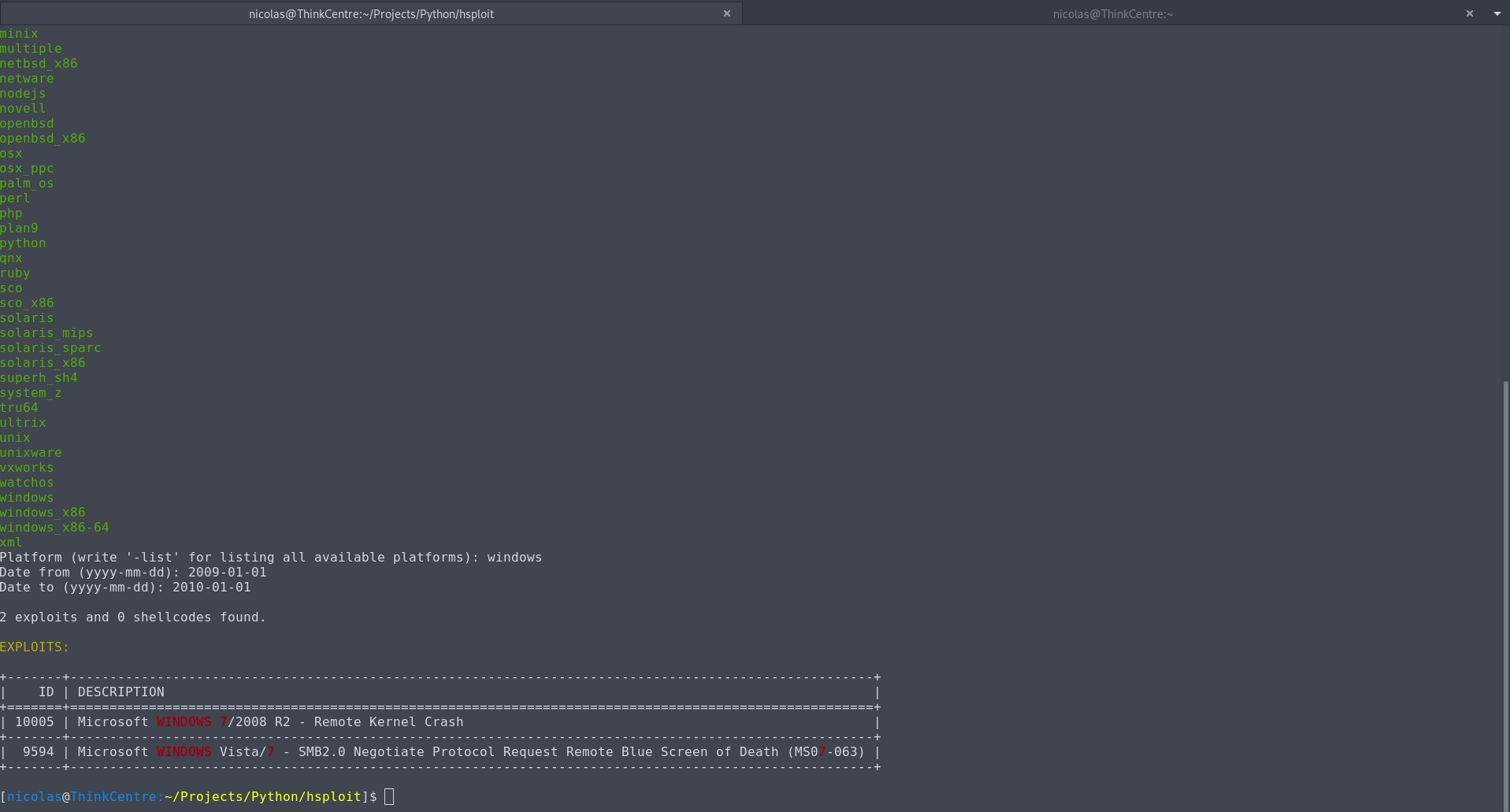
您可以選擇顯示針對給定搜尋字串的特定建議。對於每種情況,您還可以決定是否使用自動替換。可以新增建議和刪除現有建議。
我們可以簡單地透過執行以下操作來安裝 hsploit:
$ git clone https://github.com/nicolas-carolo/hsploit
$ cd hsploit
$ ./install_db_linux.sh
$ pip install -r requirements.txt
$ python setup.py install現在您可以刪除已下載的hsploit儲存庫,因為該儲存庫已複製到~/.HoundSploit/hsploit中以支援自動更新。如果您已經安裝了HoundSploit 2.3.0版本或從未安裝過HoundSploit ,您可以檢查是否有~/HoundSploit目錄,然後將其刪除。
我們可以簡單地透過執行以下操作來安裝 hsploit:
$ git clone https://github.com/nicolas-carolo/hsploit
$ cd hsploit
$ mkdir /root/.HoundSploit
$ touch /root/.HoundSploit/enable_root.cfg
$ ./install_db_linux.sh
$ pip install -r requirements.txt
$ python setup.py install現在您可以刪除已下載的hsploit儲存庫,因為該儲存庫已複製到~/.HoundSploit/hsploit中以支援自動更新。如果您已經安裝了HoundSploit 2.3.0版本或從未安裝過HoundSploit ,您可以檢查是否有~/HoundSploit目錄,然後將其刪除。
我們可以簡單地透過執行以下操作來安裝 hsploit:
$ git clone https://github.com/nicolas-carolo/hsploit
$ cd hsploit
$ ./install_db_darwin.sh
$ pip install -r requirements.txt
$ python setup.py install現在您可以刪除已下載的hsploit儲存庫,因為該儲存庫已複製到~/.HoundSploit/hsploit中以支援自動更新。如果您已經安裝了HoundSploit 2.3.0版本或從未安裝過HoundSploit ,您可以檢查是否有~/HoundSploit目錄,然後將其刪除。
如果您在安裝階段遇到問題,請執行:
$ rm -fr ~ /.HoundSploit然後重複安裝階段。
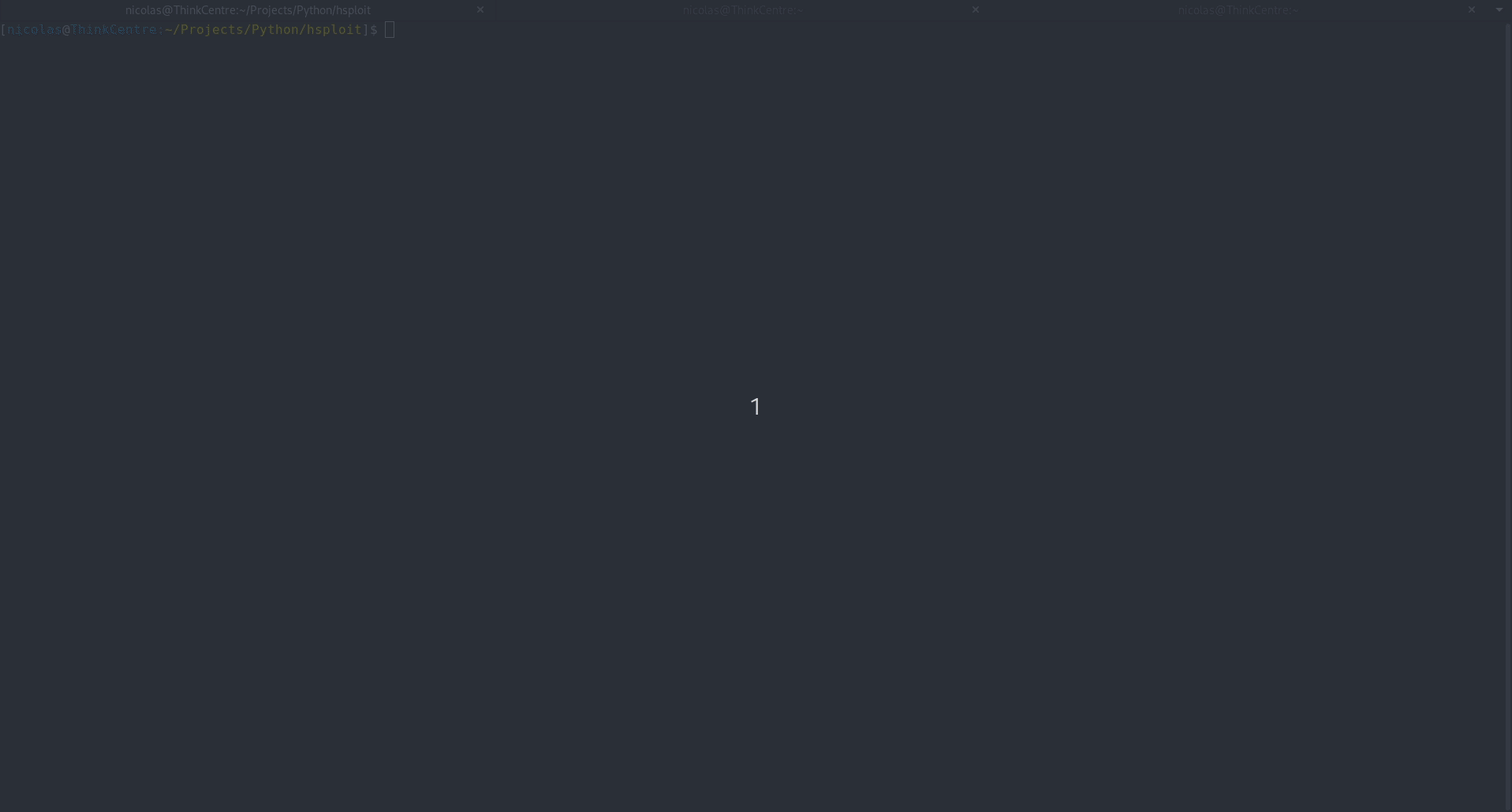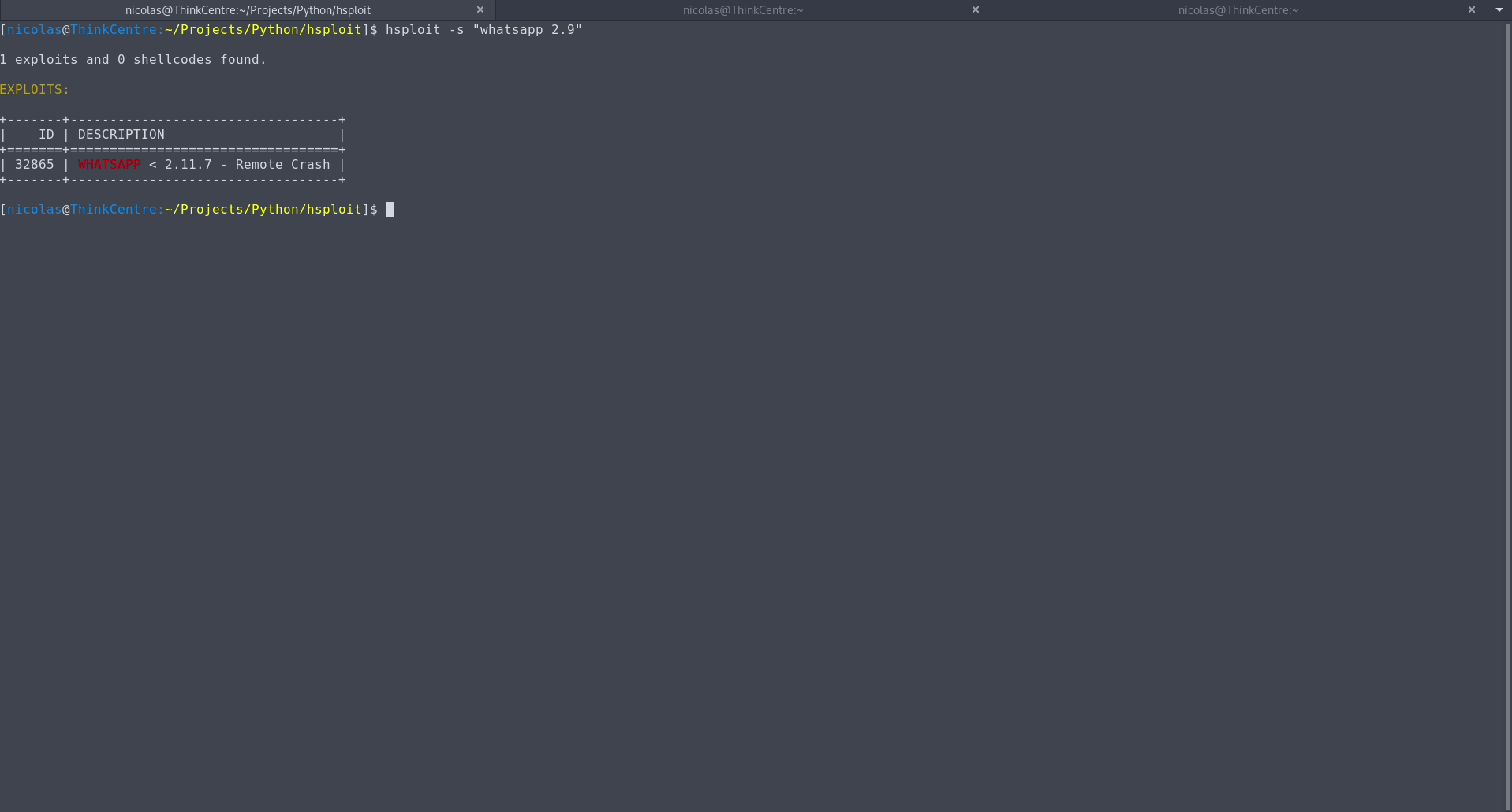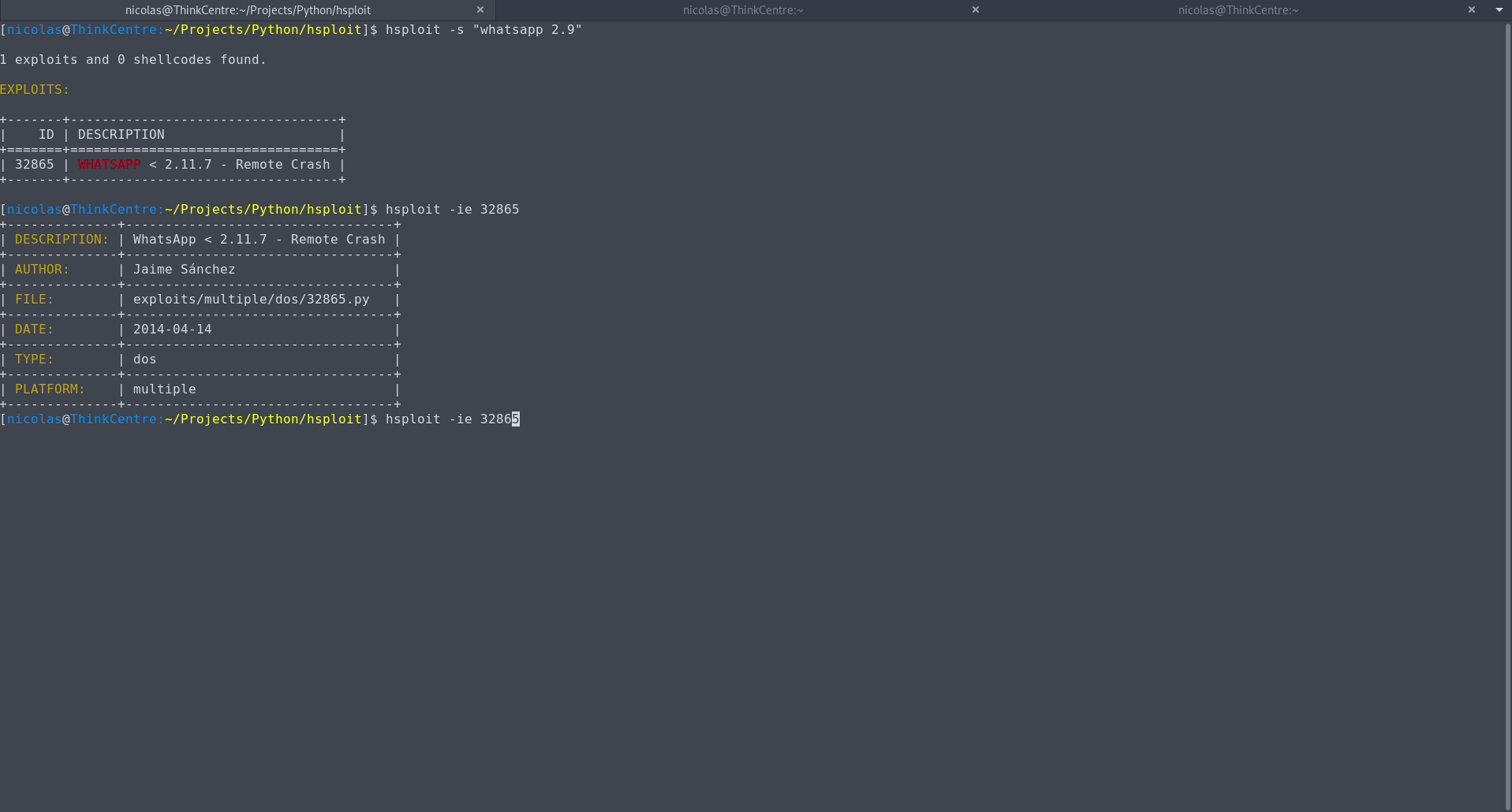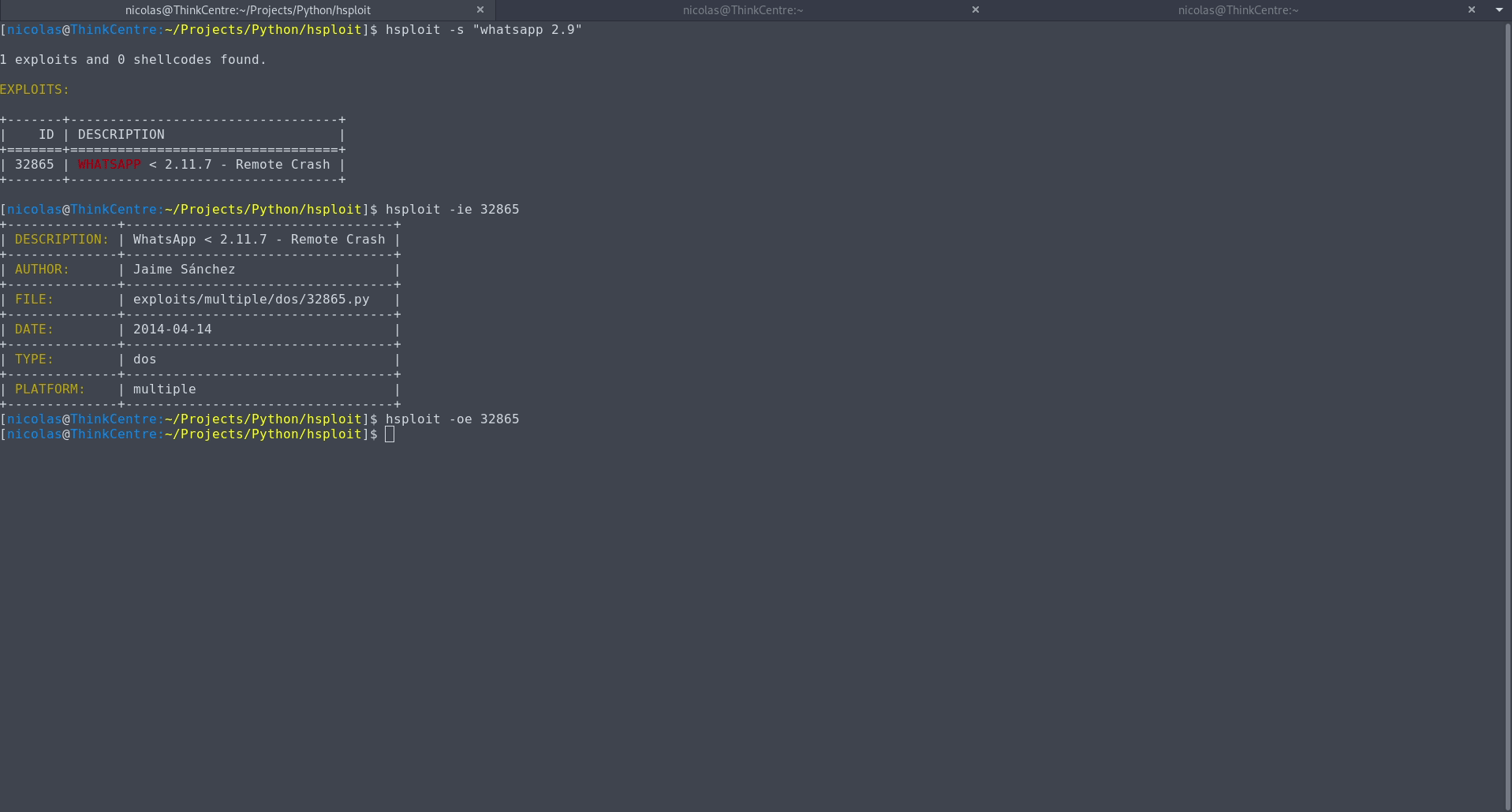
$ hsploit -s " [search text] "$ hsploit -s --nokeywords " [search text] "$ hsploit -s --notable " [search text] "$ hsploit -s --file [filename] " [search text] "$ hsploit -sad " [search text] "$ hsploit -sad --nokeywords " [search text] "$ hsploit -sad --notable " [search text] "$ hsploit -sad --file [filename] " [search text] "$ hsploit -ie [exploit ' s id]$ hsploit -is [shellcode ' s id]$ hsploit -oe [exploit ' s id]$ hsploit -os [shellcode ' s id]$ hsploit -cpe [exploit ' s id] [file or directory]$ hsploit -cps [shellcode ' s id] [file or directory]$ hsploit -ls$ hsploit -as " [keyword(s)] "$ hsploit -rs " [keyword(s)] "$ hsploit -v$ hsploit -u$ hsploit -h當漏洞描述太長而無法在一行中顯示時,為了更好地查看搜尋結果,建議使用less-RS command ,如下例所示:
$ hsploit -s " windows " | less -SR使用-sad選項不支援此功能。
版權所有 © 2020,尼古拉斯卡羅洛。版權所有。
如果滿足以下條件,則允許以原始程式碼和二進位形式重新分發和使用,無論是否經過修改:
原始碼的重新散佈必須保留上述版權聲明、此條件清單以及以下免責聲明。
以二進位形式重新散佈必須在隨散佈提供的文件和/或其他資料中複製上述版權聲明、此條件清單以及以下免責聲明。
未經事先明確書面同意,本軟體作者的姓名或本軟體貢獻者的姓名均不得用於認可或推廣源自本軟體的產品。
本軟體由版權所有者和貢獻者「按原樣」提供,不承擔任何明示或默示的保證,包括但不限於適銷性和特定用途適用性的默示保證。在任何情況下,版權所有者或貢獻者均不對任何直接、間接、附帶、特殊、懲戒性或後果性損害(包括但不限於採購替代商品或服務;使用損失、數據或利潤損失;或損失)承擔責任。告知可能發生此類損害。