在 Azure AD 环境中,无需任何特殊权限即可确定用户是否禁用了多重身份验证 (MFA)。这可以通过分析帐户的创建日期和上次密码更改日期来完成。
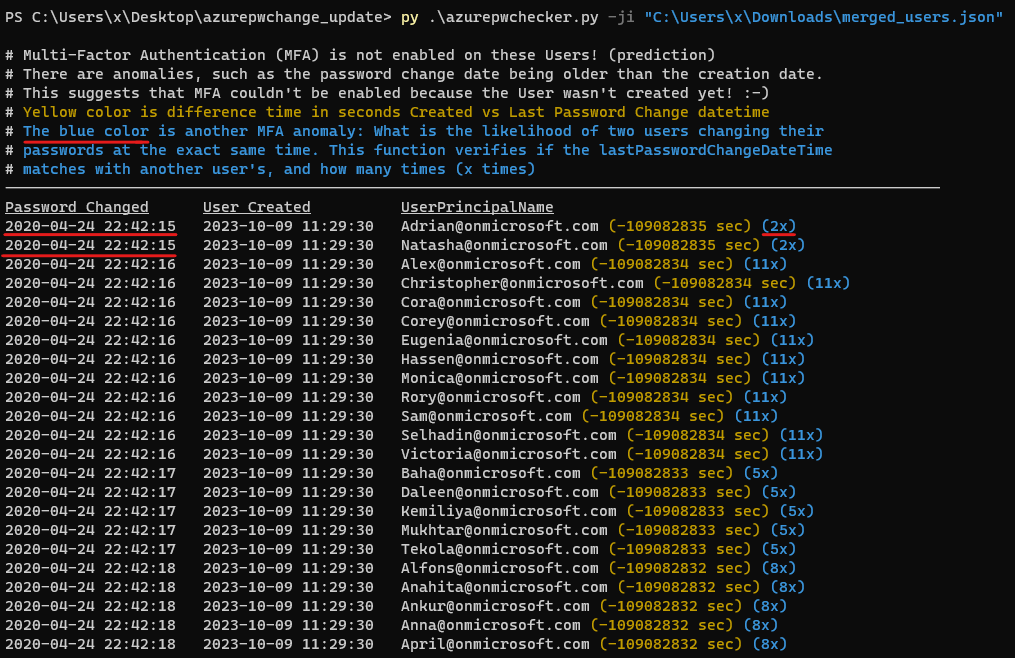
如果帐户的创建日期和时间与其上次密码更改日期和时间相匹配,则可能表明自该帐户创建以来未发生任何人工交互,并且用户无法启用多重身份验证 (MFA) 或更改其密码密码。还有其他“异常”,例如密码更改日期早于创建日期。这还表明无法启用多重身份验证 (MFA),因为尚未创建用户!
2023 年 10 月 16 日更新:
2024 年 2 月 18 日更新:
此信息可用于识别设计供红队和蓝队使用的潜在安全风险。
此工具需要借助 --code-javascript 选项提取的 roadrecon 数据库文件或 JSON 文件。 Roadrecon 工具由 dirkjanm 开发,可以在 github https://github.com/dirkjanm/ROADtools 或pip install roadrecon下载。
使用方法见:
python3 azurepwchecker.py
usage: azurepwchecker.py [-h] [--roadrecon-dump] [--roadrecon-dump-mfa] [-d DB] [-m] [-l] [-ll] [-lll] [-la] [-lo]
[-ji JSON_INPUT] [-c]
Azure AD Password Checker - This is a parser for generated JSON file or the roadrecon database file designed for use by both red and blue teams.
Database can be created when using --code-javascript option to extract 'merged_users.json' file with be created to later input this file with --json-input argument.
And roadrecon generated roadrecon.db file can be used! roadrecon is developed by https://github.com/dirkjanm credits to him!
options:
-h, --help show this help message and exit
-d DB, --db DB Specify the path to the 'roadrecon.db' database file, default is this location
-m, --mfa-list User Accounts without MFA (No privileged user required)! This argument helps identify user
accounts that have not enabled Multi-Factor Authentication (MFA). If an account's creation
date and time match its last password change date and time, it may indicate that no human
interaction has occurred since the account was created, and the user has not been able to
enable MFA or change their password. And there are other 'anomalies' such as the password
change date being older than the creation date. This suggests also that Multi-Factor
Authentication (MFA) couldn't be enabled because the User wasn't created yet! :-]
-mo OUTFILE, --outfile OUTFILE
Output users with MFA anomalies to file
-l, --pw-month User accounts that had their passwords changed last month
-ll, --pw-year User accounts that had their passwords changed last year
-lll, --pw-older User accounts that haven't changed their passwords in a long time, oldest first
-la, --admin User accounts that are members of 'Admin' named groups, including 'Global Reader'
-lo, --out-of-hours User password change that occurred outside of office hours, specifically between 5:00 PM
(17:00) and 8:00 AM (08:00) on weekdays, as well as on Saturdays and Sundays
-ji JSON_INPUT, --json-input JSON_INPUT
Provide the JSON file imported from your web browser's console using JavaScript. For
'createdDateTime' and 'lastPasswordChange' details, ensure you download the JSON output using
the '--code-javascript' option.
-c, --code-javascript
Perform extraction even if 'azurepwchecker.py' or 'roadrecon' is unavailable. This script
enables extraction through the JavaScript console of a web browser. To proceed, ensure you
have a valid account to log in at https://portal.azure.com/#view/Microsoft_AAD_UsersAndTenants
/UserManagementMenuBlade/~/AllUsers or an active session on a computer. Copy and paste the
provided JavaScript code into the browser's console. Once the session is validated and you
have the necessary permissions, a JSON file named 'merged_users.json' will be generated. You
can then import it using the following command as example: 'azurepwchecker.py --json-input
merged_users.json -m'
-v, --version show program's version number and exit
run roadrecon first:
(Run the following command to install the tool "pip install roadrecon)"
--roadrecon-dump "roadrecon dump" command or do it with roadrecon
--roadrecon-dump-mfa "roadrecon dump --mfa" command (requires privileged access) or do it with roadrecon
azurepwchecker.py --code-javascript或 js 文件:按照以下步骤使用提供的脚本检索用户列表及其帐户信息。
登录 Azure 门户
访问用户管理
打开开发者工具
F12打开开发人员工具。执行脚本
检索用户列表和用户信息
下载合并后的用户信息
merged_users.json的文件。在 Azure AD 密码检查器上运行
azurepwchecker.py --json-input merged_users.json参见示例:
参见简介:
2023 年 10 月 16 日更新:
如何使用--code-javascript参数在 Azure 门户上生成用户列表,然后可以使用命令azurepwchecker.py --json-input merged_users.json导入该列表:
2024 年 2 月 13 日更新:
我从 @dafthack 上传了 GraphRunner 的编辑版本并感谢他。在此修改版本中,我添加了一项新功能,可让您直接从“受害者”设备读取 HAR 文件。此新功能有助于检查和检查访问令牌以访问不同的权限或范围。此外,如果访问令牌已过期,此版本允许使用刷新令牌来创建新的访问令牌。此过程对时间敏感,但如果您已经登录 Office365 环境,则无需输入用户名和密码,因为它只需要在 HAR 文件中找到的会话令牌。
请理解,代码可能看起来有点混乱。我的专业知识主要不是 JavaScript,因此我的主要关注点是添加新功能而不是组织代码。
下载 HAR 文件,您可以使用 Web 浏览器中提供的开发工具。对于大多数浏览器,只需按 F12 打开开发工具,然后导航到“网络”选项卡以保存 HAR 文件,刷新网页后:
通过提供的界面上传您的 HAR 文件。上传后,您可以浏览各种访问令牌来分析会话详细信息,包括其范围等。显示为红色的令牌表示它们已过期。 GraphRunner 还支持在必要时使用刷新令牌生成新的有效访问令牌:视频
添加了允许下载 JSON 文件中的完整用户数据、检测帐户中的 MFA 异常以及下载这些异常列表的功能:视频